A series of vulnerabilities have been uncovered in the widely deployed Adtran 834-5 Wi-Fi 5 Service Delivery Gateway (SDG), potentially leaving countless users and networks exposed to malicious exploitation. The flaws, discovered by security researcher Edward Warren, range from easily guessed default passwords to hidden backdoor accounts.
The Vulnerabilities
-
CVE-2024-31970 (CVSS 8.8): Open Door for Root Access During the setup process, the affected Adtran devices use a default “admin/admin” username and password combination, granting complete root-level access. Attackers could exploit this brief window to gain unauthorized control and execute commands at will.
-
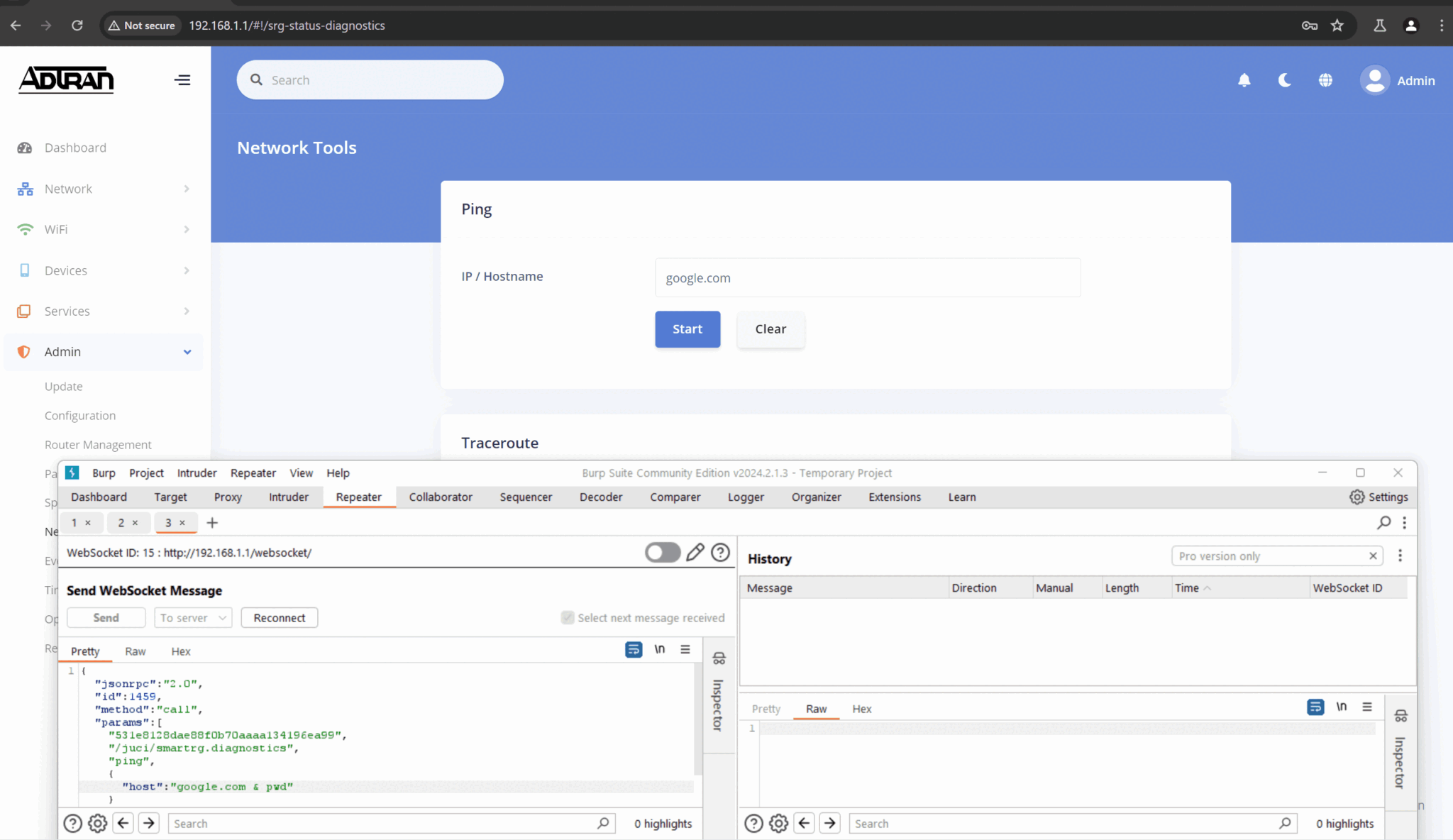
CVE-2024-31977 (CVSS 8.8): Injection Attacks via Network Tools A command injection vulnerability allows attackers to insert malicious code into the device’s ping or traceroute utilities. This could enable attackers to bypass security measures, steal sensitive information, or disrupt network operations.
-
CVE-2024-39345 (CVSS 7.2): Hidden Backdoor Account Perhaps the most alarming flaw is a hidden, undocumented “support” account with a password derived from the device’s MAC address. This backdoor grants root-level access to anyone who can crack the simple password pattern.
Widespread Impact
The Adtran 834-5 SDG is widely used by service providers and businesses for its carrier-class performance and reliability. The prevalence of these devices, coupled with the severity of the vulnerabilities, makes this a significant security concern.
Mitigation and Response
Adtran has released firmware updates (SmartOS Version 12.1.3.1 and later) that address these vulnerabilities. Users are strongly urged to update their devices immediately. Additionally, it’s crucial to change default passwords and implement strong, unique passwords for all accounts.
Related Posts:
- CVE-2024-40897: Vulnerability in Orc Compiler Opens Door to Code Execution Attacks
- PKfail Vulnerability: A New Threat to UEFI Security Unveiled by Binarly Research Team
- CVE-2024-39676: Apache Pinot Flaw Exposes Sensitive Data, Urgent Upgrade Needed