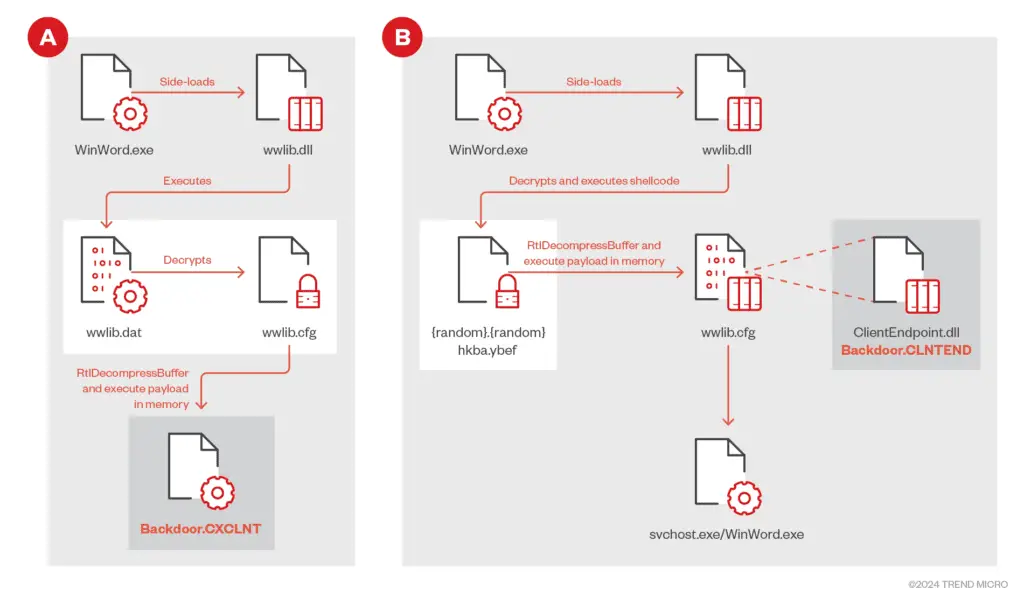
Execution flow of CLNTEND | Image: Trend Micro
A newly identified threat cluster, dubbed TIDRONE, has been actively targeting the Taiwanese military and satellite industries since the beginning of 2024, according to a report from Trend Micro. Leveraging evolving tools and sophisticated techniques, this threat actor has demonstrated a particular interest in drone manufacturers, raising concerns about potential espionage and intellectual property theft.
TIDRONE’s primary targets are organizations connected to Taiwan’s defense and satellite industries, especially those involved in drone manufacturing. The attack chain suggests the group’s intent to extract sensitive information related to military technologies, reinforcing suspicions that TIDRONE is engaged in cyber espionage with geopolitical motives. Notably, the group’s activities have extended beyond Taiwan, indicating a broader strategy targeting other countries’ defense sectors.
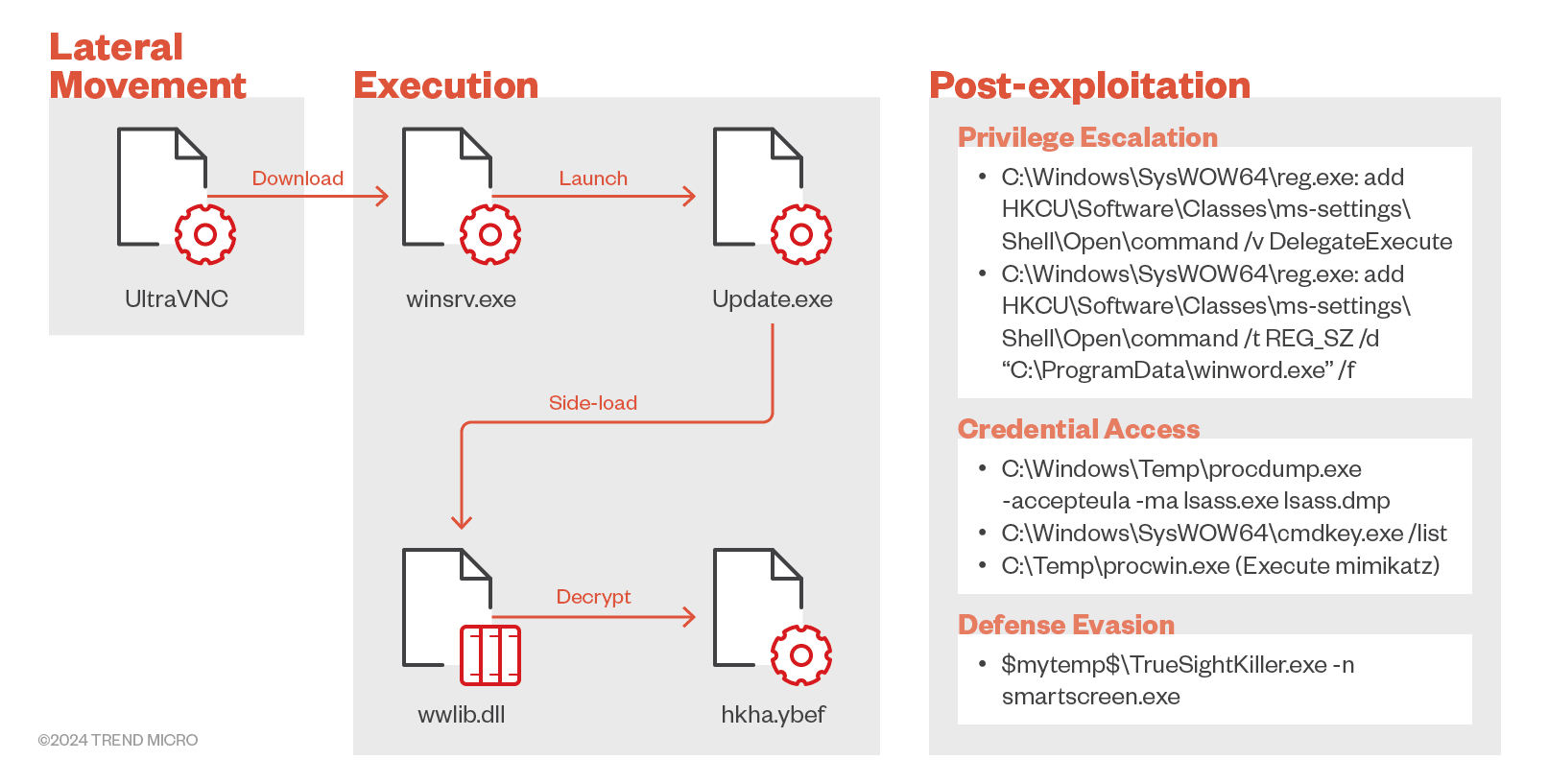
TIDRONE’s arsenal includes the backdoors CXCLNT and CLNTEND, which have undergone significant updates and optimizations. These tools now incorporate anti-analysis techniques, such as verifying entry point addresses and hooking APIs to evade detection.
TIDRONE’s malware employs advanced anti-analysis techniques, making it difficult for researchers to reverse-engineer the malicious code. For example, the malware hooks into widely-used APIs, such as GetProcAddress, to alter the execution flow and evade detection.
Additionally, the malware avoids common methods of starting new threads, such as CreateThread or _beginthread, instead using ConvertThreadToFiber and SwitchToFiber techniques. This approach allows the malware to bypass traditional antivirus detection mechanisms, further highlighting TIDRONE’s ability to evolve its attack methods.
The TIDRONE campaign uses two types of backdoors, CXCLNT and CLNTEND, each designed for specific purposes:
- CXCLNT (Backdoor): Collects sensitive information such as IP addresses, MAC addresses, and system architecture from the victim’s machine. It can also receive and execute payloads from the command-and-control (C2) server, delete files to hide its presence, and maintain persistence via registry settings.
- CLNTEND (Backdoor): Operates as a remote shell tool, capable of injecting further payloads into system processes, such as svchost.exe, and establishing communication with the C2 server using multiple protocols, including TCP, HTTP, and TLS. This backdoor’s flexibility and stealth make it an effective tool for long-term espionage.
In a recent case study, the malware was delivered via UltraVNC and exploited a vulnerability in an ERP system, hinting at a possible supply chain attack. Once inside, the malware escalated privileges and performed malicious activities, including UAC bypass, credential dumping, and disabling antivirus software.
Based on file compilation times and operation patterns, Trend Micro’s analysis suggests that TIDRONE may be linked to Chinese state-sponsored cyber espionage activities. The group’s focus on Taiwan’s military sector, combined with the use of advanced anti-detection techniques, reinforces the likelihood that this is a carefully coordinated espionage campaign targeting sensitive geopolitical information.
Related Posts:
- Chinese APT41 Group Breaches Taiwanese Research Institute
- 160GB of confidential data leaked, PC giant Acer confirms its servers were hacked