TimbreStealer: Stealthy Information Thief Targets Mexico
Cisco Talos has discovered a highly targeted and persistent phishing campaign preying on users in Mexico. The attackers are luring potential victims with financial-themed emails tailored to the region and then tricking them into downloading an insidious new information stealer dubbed “TimbreStealer.” This malware exhibits a high level of sophistication in its obfuscation techniques, anti-analysis mechanisms, and multi-stage execution, indicating a well-resourced and skilled adversary.
TimbreStealer: Evasion and Persistence

TimbreStealer goes to extreme lengths to avoid detection and analysis. Its core components are heavily obfuscated using custom loaders, encryption schemes, and even the Heaven’s Gate technique to execute 64-bit code in a 32-bit process. Furthermore, it leverages direct system calls to bypass conventional API monitoring.
The malware’s decryption process is meticulously orchestrated, involving a central decryption key that is constantly updated as execution progresses. This dynamic encryption scheme thwarts attempts by security researchers to reverse engineer the malware’s functionality or extract embedded payloads. The authors demonstrate a deep understanding of analysis techniques, clearly intending to hinder investigation efforts.
Geofencing Techniques and Evolution
To maximize impact within their target region, the attackers behind TimbreStealer employ geofencing techniques. The malware meticulously checks the victim’s system language and timezone to ensure it is within the Latin American region. Attempts to access the payload from outside Mexico result in a blank PDF file, further limiting exposure and analysis. Interestingly, Talos observed that this same threat group initially distributed the Mispadu banking trojan with a similar campaign, but shifted to TimbreStealer in November 2023.
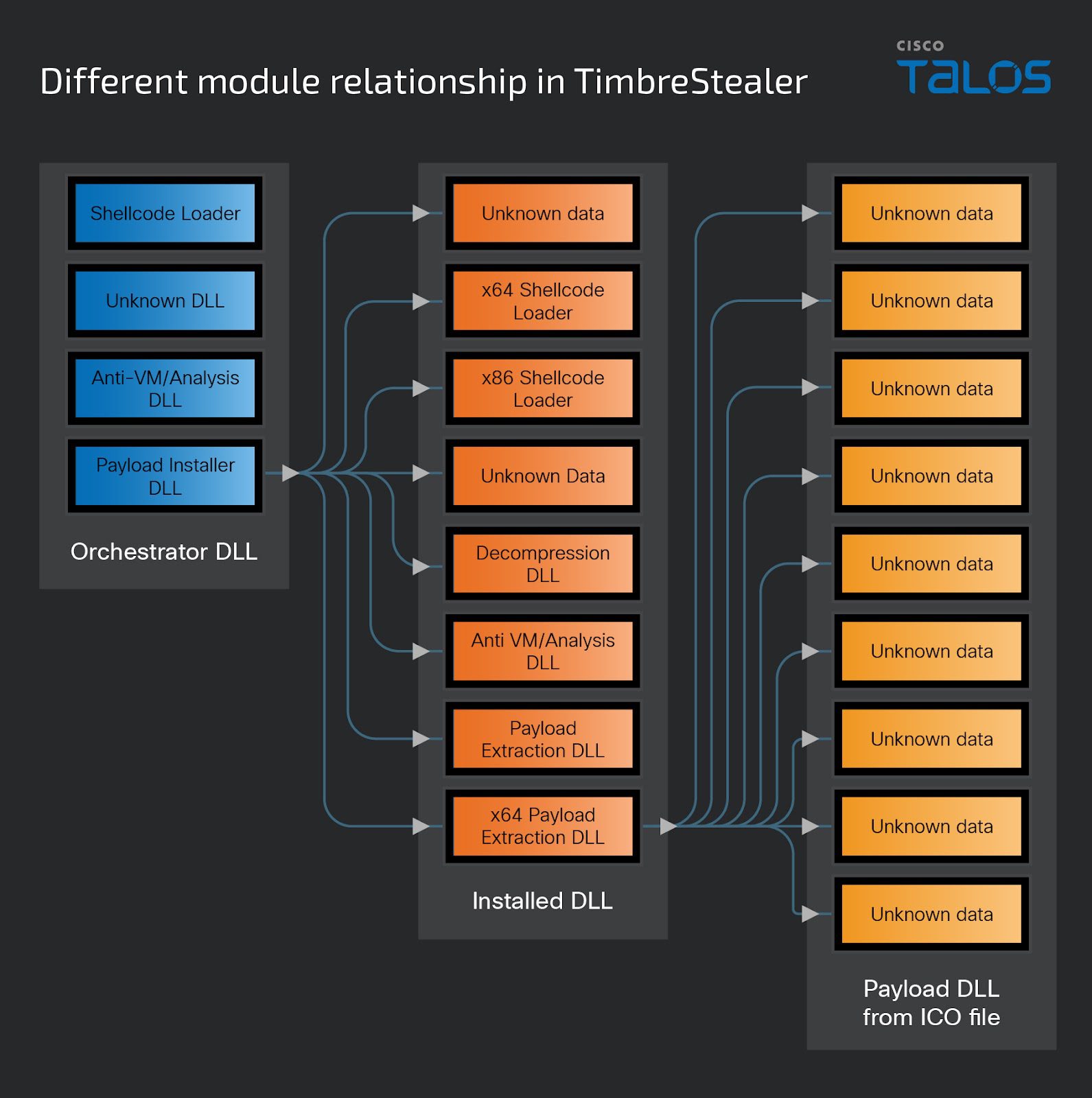
Multi-Stage Infection
TimbreStealer’s installation process is highly modularized and involves multiple stages, each with varying obfuscation and anti-analysis measures.
-
Stage 1: Initial Dropper – The dropper is heavily packed and includes an embedded DLL. It carefully scans for Zw* exports, building a hash table for direct system calls. It then decrypts the next stage payload from its .data section.
-
Stage 2: Orchestrator – This layer determines victim suitability by checking language, timezone, and even the presence of specific files and registry keys (suggesting a focused targeting scope). It also conducts sandbox detection, and debugger checks, and looks for browser activity to avoid automated analysis.
-
Stage 3: Installer – Using the ITaskService COM interface, the installer drops several files to disk and triggers execution through a benign-looking decoy document. Persistence is sometimes established via registry keys or altered Group Policy options.
The Final Payload
The final payload is a DLL (Cecujujajofubo475.dll) with a complex internal architecture employing even deeper levels of encryption and obfuscation than observed previously. Its core capabilities include:
- Disabling Event Tracing for Windows (ETW) – Cripples system data collection.
- Patching Loaded DLLs – Removes analysis hooks and breakpoints.
- Data Exfiltration and Credential Theft – Scans for various file types, targets browser credential stores, and harvests system and network information (OS, hardware, network domain, installed applications).
- Network Communication – Exfiltrates stolen data to attacker-controlled domains.
Conclusion
TimbreStealer represents a significant threat to Mexican users and organizations. Its advanced evasion mechanisms and targeted nature indicate a skilled and determined adversary. This campaign highlights the importance of robust email security with user awareness training, combined with endpoint protection solutions capable of detecting sophisticated malware that evades traditional signature-based detection.
Talos is actively monitoring the evolution of TimbreStealer and will continue to provide updates as new information and indicators of compromise become available.





