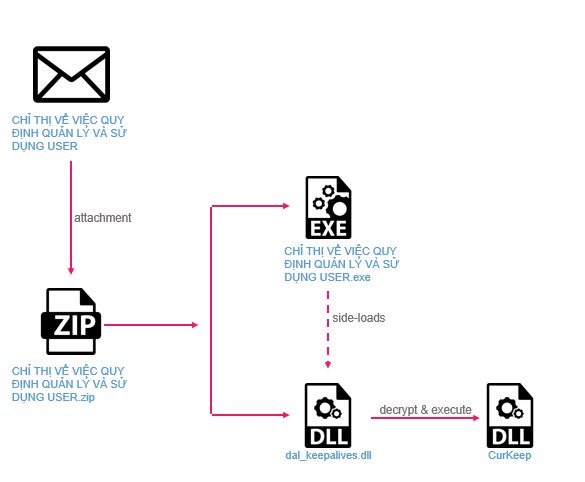
The CurKeep infection chain | Image: Check Point
Researchers have unveiled an expansive campaign dubbed “Stayin’ Alive,” targeting governmental bodies and telecommunication firms across several Asian nations. According to experts at Check Point, these attacks, orchestrated by the Chinese hacker collective, ToddyCat, have been ongoing since 2021.
The principal victims are located in Kazakhstan, Uzbekistan, Pakistan, and Vietnam. The adversaries adopt an inventive approach: frequently crafting unique tools tailored to each victim, complicating the task for researchers to link the incidents. This method also effectively circumvents security measures, considering various individual characteristics such as the scale of the organization, language, and region.
Typically, the onslaught commences with targeted phishing email campaigns. Attached are ZIP files containing malicious executables bearing digital signatures. These files are camouflaged as innocuous documents: contracts, invoices, and business proposals.
Upon activation of the malicious code, the culprits exploit the CVE-2022-23748 vulnerability in the Audinate Dante Discovery software. This flaw enables the surreptitious upload of the CurKeep program, evading standard detection tools.
CurKeep is a mere 10 KB backdoor, establishing a persistent presence within the system, harvesting data, and awaiting directives from hackers.
Other tools employed in these attacks include loaders such as CurLu, CurCore, and CurLog. These facilitate the execution of arbitrary codes and the upload of additional malicious modules.
One of the more sophisticated tools is the StylerServ backdoor. It covertly monitors network traffic across five ports (ranging from 60810 to 60814) and downloads an encrypted configuration package, stylers.bin, containing subsequent instructions.
Check Point experts warn that these malefactors continually refine their techniques, suggesting that the real scale of their operations might be far more extensive.
Despite variations in the source code of the tools deployed, all connect to a singular command and control infrastructure. It has been previously determined by the Kaspersky Lab team that this infrastructure belongs to ToddyCat.