If Microsoft Windows 7 and Server 2008 R2 users have not upgraded the Intel CPU Meltdown vulnerability patch, please upgrade the system patch as soon as possible. The original Microsoft patch also has a flaw.
In January and February of this year, Swedish researcher Ulf Frisk announced the Total Meltdown vulnerability in Intel chips. In late March, Microsoft released a system update for the vulnerability, but the patch made Microsoft’s operating system, especially Windows 7 and Server 2008 R2. Worse, there was a malicious program that was previously exploited to exploit this vulnerability to steal data from the chip’s memory. Microsoft engineers inadvertently changed the read and write permissions of the computer’s memory input page table into the normal software mode so that any software installed on the computer can read/modify the data in the chip memory. Therefore, the user needs to ensure that the system has the latest version of the system patch installed.
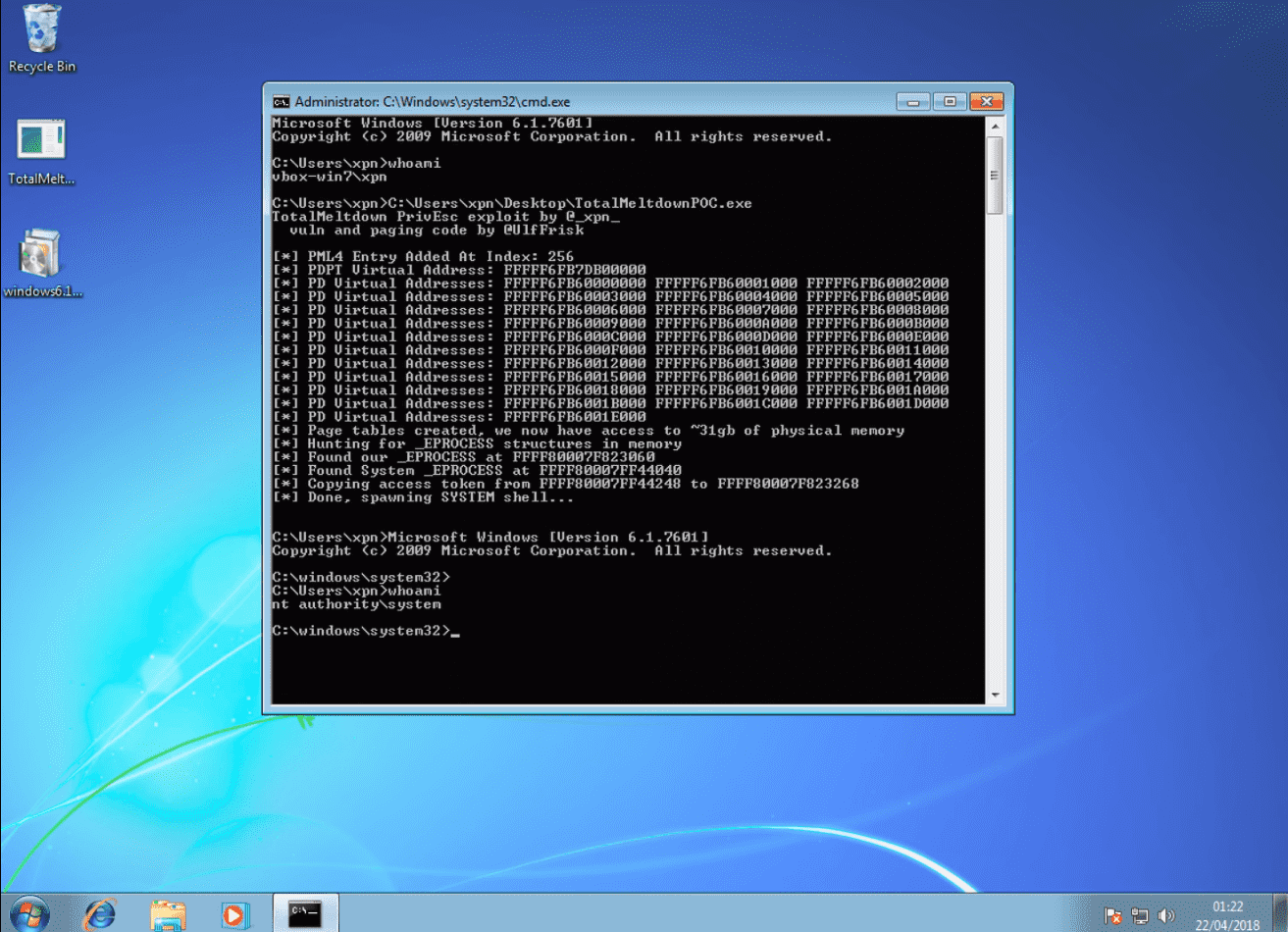
Now the XPN team researchers found that you can open a command line window with administrator rights under normal user rights. This will provide the convenience for hackers to access the memory page table of the chip. The specific operations are as follows:
- Create a new set of page tables which will allow access to any physical memory address;
- Create a set of signatures which can be used to hunt for _EPROCESS structures in kernel memory;
- Find the _EPROCESS memory address for our executing process, and for the System process; and
- Replace the token of our executing process with that of System, elevating us to NT AUTHORITY\System.
The Xen project team also submitted a Meltdown-related vulnerability in January that required system administrators to install another patch. They found that the previous system patch ignored an error code in INT 80 that would be associated with the system’s general exception handling. If a PV client does not call INT 80 on the virtual CPU, the system writes 0 near memory address 2^64 and closes the entire body. This patching method is ready to release system patch packages. Of course, this vulnerability will only occur in x86-based paravirtualized objects.
Source: theregister