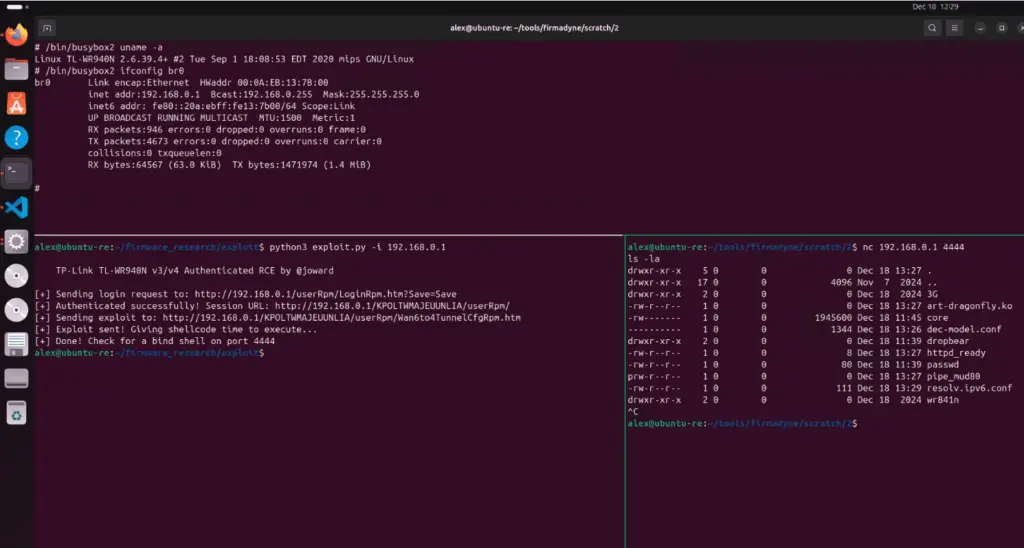
Security researcher Joward has published an in-depth analysis and Proof of Concept (PoC) exploit for a critical vulnerability, tracked as CVE-2024-54887, affecting TP-Link TL-WR940N routers. This flaw is a buffer overflow vulnerability discovered in the device’s handling of IPv6 DNS server configuration parameters, potentially allowing attackers to execute arbitrary code or cause denial-of-service attacks.
Joward’s research revealed that two parameters—dnsserver1 and dnsserver2—within the router’s web interface fail to validate string lengths before copying them into memory. As Joward explained, “Upon initial observation, it appears we may have a stack buffer overflow vulnerability.” This issue affects hardware versions 3 and 4 of the TL-WR940N router running the latest firmware and has been mitigated in subsequent hardware iterations.
Static analysis of the device’s firmware uncovered several critical shortcomings, including the absence of modern mitigations such as NX and PIE protections. These gaps make it significantly easier for researchers—and potentially attackers—to exploit vulnerabilities.
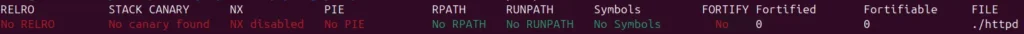
The PoC demonstrates a sophisticated approach to exploiting the vulnerability, leveraging Return Oriented Programming (ROP) techniques to achieve remote code execution. Joward meticulously details the process, from identifying unsafe function calls to constructing a functional exploit:
- Static and Dynamic Analysis: The analysis began with unpacking and emulating the router firmware using tools like Firmadyne and Ghidra. “The dnsserver1 and dnsserver2 parameters allow you to pick which IPv6 DNS servers the router should default to, and it appears that neither one is having its length checked before being copied into memory,” Joward notes.
- ROP Exploit Development: A series of carefully crafted gadgets facilitated the execution of shellcode. “Writing a ROP exploit for MIPS Linux has a few unique considerations that x86 exploits do not, and it’s not as straight forward as a hard coded jump to a location on the stack. Chief among these concerns: Cache incoherency & Delay instructions,” Joward explains.
- Custom Shellcode: The exploit uses a bind shell for simplicity, allowing others to replicate the attack without modifying IP addresses. This shellcode enables full control over the compromised device.
CVE-2024-54887 presents a severe risk for users relying on outdated hardware. With no Address Space Layout Randomization (ASLR) implemented on affected devices, the exploit can reliably achieve remote code execution. Joward emphasizes the gravity of the vulnerability: “Not only can we crash the program, we can likely control execution flow.”
Unfortunately, hardware versions 3 and 4 of the TL-WR940N have reached their end-of-life support and no longer receive security updates. TP-Link confirmed this during the disclosure process and has encouraged users to upgrade to newer devices to ensure ongoing protection.
For those interested in exploring the technical details, the PoC and additional resources are available on GitHub.
Related Posts:
- Congress Scrutinizes TP-Link Routers Over Cybersecurity Concerns
- Old Vulnerability, New Attacks: Botnets Swarm Exploited CVE-2023-1389 in TP-Link Routers
- Researchers Uncover Massive Quad7 Botnet Targeting Microsoft 365
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- CVE-2024-42815 (CVSS 9.8): Buffer Overflow Flaw in TP-Link Routers Opens Door to RCE