T-Pot – The All In One Honeypot Platform
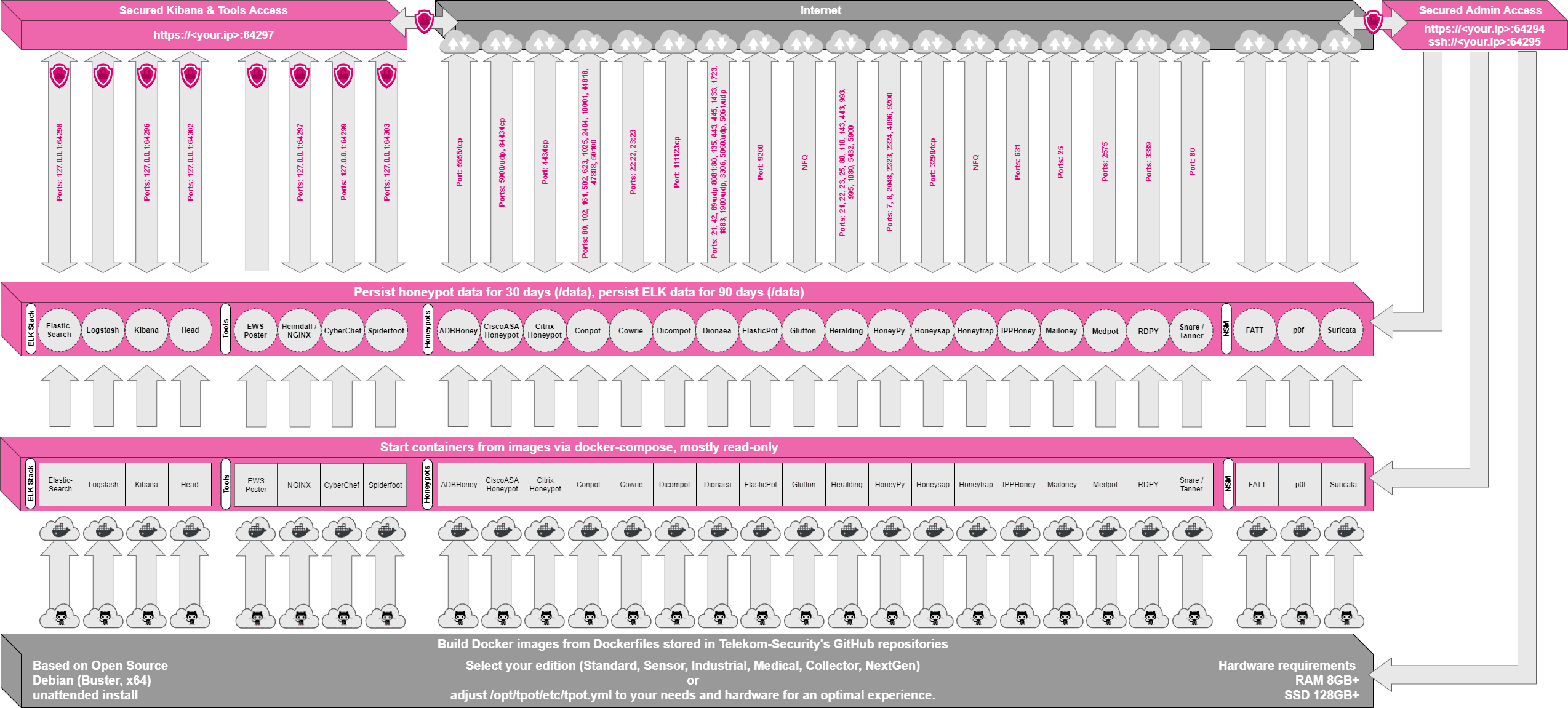
T-Pot is based on the Debian (Stable) network installer. The honeypot daemons as well as other support components are dockered. This allows T-Pot to run multiple honeypot daemons and tools on the same network interface while maintaining a small footprint and constrain each honeypot within its own environment.
In T-Pot we combine the dockerized honeypots …
- adbhoney,
- ciscoasa,
- citrixhoneypot,
- conpot,
- cowrie,
- dicompot,
- dionaea,
- elasticpot,
- glutton,
- heralding,
- honeypy,
- honeysap,
- honeytrap,
- ipphoney,
- mailoney,
- medpot,
- rdpy,
- snare,
- tanner
… with the following tools …
- Cockpit for a lightweight, WebUI for docker, os, real-time performance monitoring, and web terminal.
- Cyberchef a web app for encryption, encoding, compression, and data analysis.
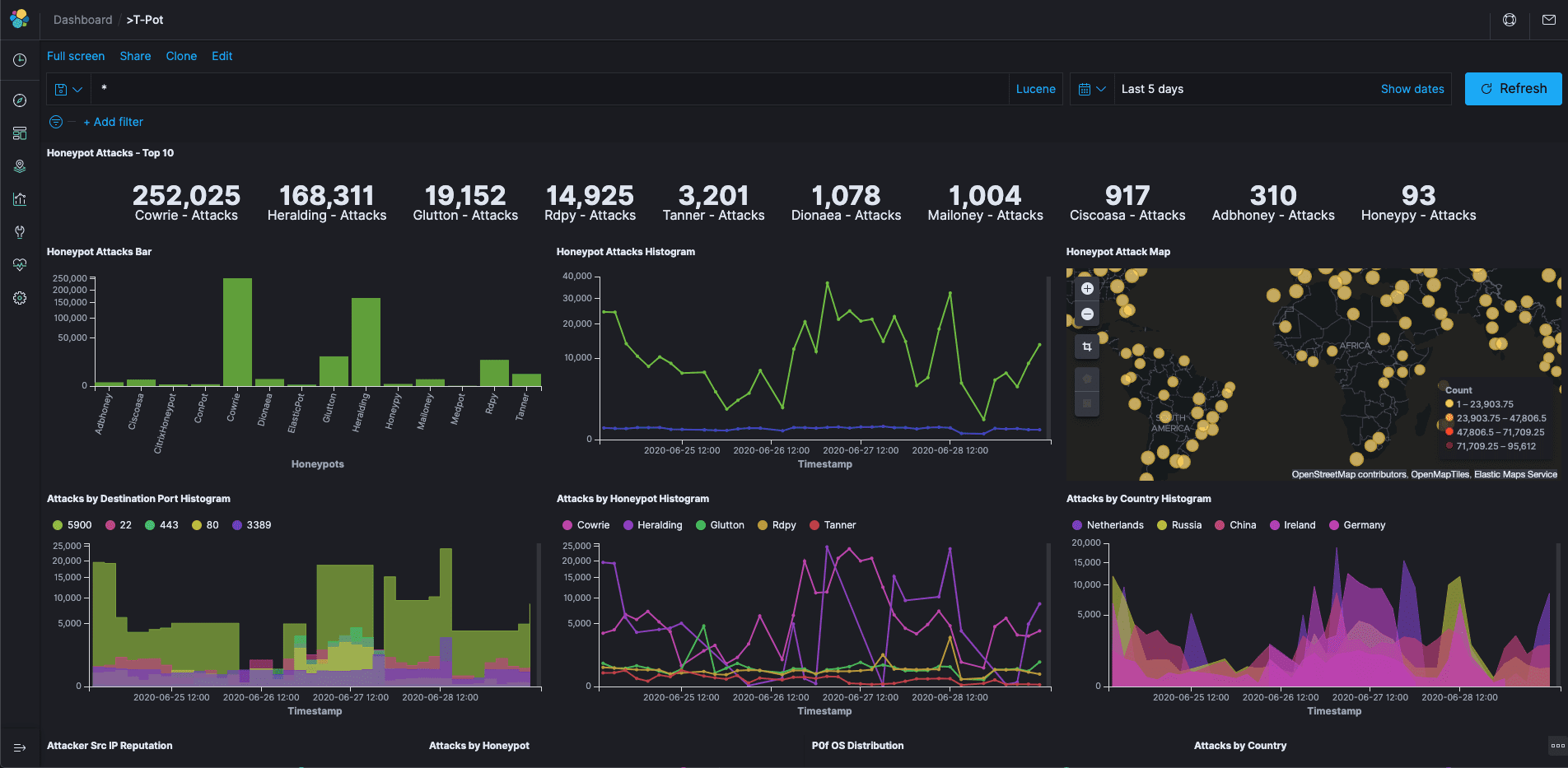
- ELK stack to beautifully visualize all the events captured by T-Pot.
- Elasticsearch Head a web front end for browsing and interacting with an Elastic Search cluster.
- Fatt a pyshark based script for extracting network metadata and fingerprints from pcap files and live network traffic.
- Spiderfoot a open-source intelligence automation tool.
- Suricata a Network Security Monitoring engine.
… to give you the best out-of-the-box experience possible and an easy-to-use multi-honeypot appliance.
While data within docker containers is volatile T-Pot ensures a default 30-day persistence of all relevant honeypot and tool data in the well-known/data folder and sub-folders. The persistence configuration may be adjusted in /opt/tpot/etc/logrotate/logrotate.conf. Once a docker container crashes, all other data produced within its environment is erased and a fresh instance is started from the corresponding docker image.
Basically, what happens when the system is booted up is the following:
- start host system
- start all the necessary services (i.e. cockpit, docker, etc.)
- start all docker containers via docker-compose (honeypots, nms, elk, etc.)
The T-Pot project provides all the tools and documentation necessary to build your own honeypot system and contribute to our Sicherheitstacho.
The source code and configuration files are fully stored in the T-Pot GitHub repository. The docker images are preconfigured for the T-Pot environment. If you want to run the docker images separately, make sure you study the docker-compose configuration (/opt/tpot/etc/tpot.yml) and the T-Pot systemd script (/etc/systemd/system/tpot.service), as they provide a good starting point for implementing changes.
The individual docker configurations are located in the docker folder.
Changelog v22.04.0
New Features
- Distributed Installation with HIVE and HIVE_SENSOR
- ARM64 support for all provided Docker images
- GeoIP Attack Map visualizing Live Attacks on a dedicated webpage
- Kibana Live Attack Map visualizing Live Attacks from different HIVE_SENSORS
- Blackhole is a script trying to avoid mass scanner detection
- Elasticvue a web front end for browsing and interacting with an Elastic Search cluster
- Ddospot a honeypot for tracking and monitoring UDP-based Distributed Denial of Service (DDoS) attacks
- Endlessh is a SSH tarpit that very slowly sends an endless, random SSH banner
- HellPot is an endless honeypot based on Heffalump that sends unruly HTTP bots to hell
- qHoneypots 25 honeypots in a single container for monitoring network traffic, bots activities, and username \ password credentials
- Redishoneypot is a honeypot mimicking some of the Redis’ functions
- SentryPeer a dedicated SIP honeypot
- Index Lifecycle Management for Elasticseach indices is now being used
Upgrades
- Debian 11.x is now being used for the T-Pot ISO images and required for post installs
- Elastic Stack 8.x is now provided as Docker images
Updates
- Honeypots and tools were updated to their latest masters and releases
- Updates will be provided continuously through Docker Images updates
Breaking Changes
- For security reasons all Py2.x honeypots with the need of PyPi packages have been removed: HoneyPy, HoneySAP and RDPY
- If you are upgrading from a previous version of T-Pot (20.06.x) you need to import the new Kibana objects or some of the functionality will be broken or will be unavailabe
- Cyberchef is now part of the Nginx Docker image, no longer as individual image
- ElasticSearch Head is superseded by Elasticvue and part the Nginx Docker image
- Heimdall is no longer supported and superseded with a new Bento based landing page
- Elasticsearch Curator is no longer supprted and superseded with Index Lifecycle Policies available through Kibana.
Install & Use
Copyright (C) 2021 telekom-security