Get-EnhancedWinEvent
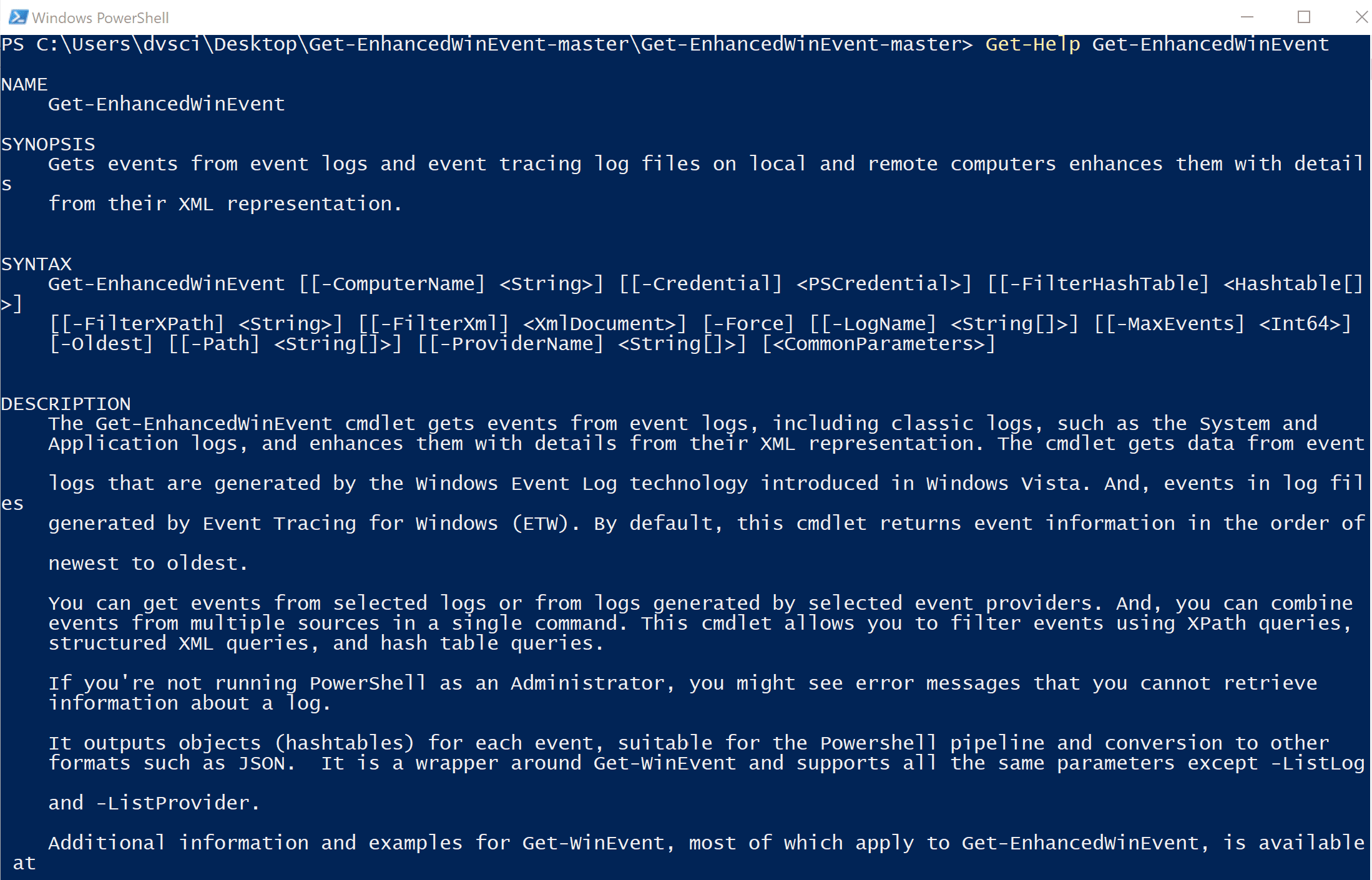
A Powershell Cmdlet that gets events from event logs and event tracing log files on local and remote computers enhances them with details from their XML representation.
The Get-EnhancedWinEvent cmdlet gets events from event logs, including classic logs, such as the System and Application logs, and enhances them with details from their XML representation … which for some reason often contains more detail, such as property names.
This is very helpful for use in things like log aggregation and forensics. The current version has all the XML-derived properties as strings, which is a minor limitation to be addressed in future releases. To be clear, sometimes the XML does not add much clarity, but even in those cases, it is better to have the full picture of what the event contained.
The cmdlet gets data from event logs that are generated by the Windows Event Log technology introduced in Windows Vista. And, events in log files generated by Event Tracing for Windows (ETW). By default, this cmdlet returns event information in the order of newest to oldest.
You can get events from selected logs or from logs generated by selected event providers. And, you can combine events from multiple sources in a single command. This cmdlet allows you to filter events using XPath queries, structured XML queries, and hash table queries.
If you’re not running PowerShell as an Administrator, you might see error messages that you cannot retrieve information about a log.
It outputs objects (hashtables) for each event, suitable for the Powershell pipeline and conversion to other formats such as JSON. It is a wrapper around Get-WinEvent and supports all the same parameters except -ListLog and -ListProvider.
Additional information and examples for Get-WinEvent, most of which apply to Get-EnhancedWinEvent, is available at from Microsoft.
Download
git clone https://github.com/counteractive/Get-EnhancedWinEvent.git
Use
PS C:\> Import-Module .\path\to\Get-EnhancedWinEvent.psm1
Import the module to get access to the Get-EnhancedWinEvent cmdlet
PS C:\> Get-EnhancedWinEvent –Path “.\Application.evtx“
Gets all events from the provided Application.evtx file
PS C:\> Get-EnhancedWinEvent –Path “.\Security.evtx“ –FilterXPath “*[System[EventID=4624]“
Gets all login events (ID 4624) from the provided Security.evtx file.
PS C:\> Get-EnhancedWinEvent –Path “.\Security.evtx“ –FilterXPath “*[System[EventID=4624]“ –MaxEvents 25
Gets at most the newest 25 logon events (ID 4624) from the provided Security.evtx file.
PS C:\> Get-EnhancedWinEvent –Path “.\Security.evtx“ –FilterXPath “*[System[EventID=4624]“ –MaxEvents 25 | ConvertTo-Json –Depth 100 | Out-File ./security.json –Encoding utf8
Gets at most the newest 25 logon events (ID 4624) from the provided Security.evtx file, which is piped to ConvertTo-Json to get nice compressed, serialized output (-Depth is set to the max of 100 because the default is 2, leading to frustrating bugs).
This is then piped to a UTF-8 encoded file for use in other tools like filebeat or jq (the default is UTF-16 if you use the redirect operator (>)).
Copyright (C) 2019
Source: https://github.com/counteractive/