Trend Micro said on Wednesday that their research team has discovered a new type of Android malware that was designed to tap the CPU power of infected devices to mine Monroe.
According to the researchers, this malicious software called “HiddenMiner (detected by Trend Micro as ANDROIDOS_HIDDENMINER)” was discovered in a third-party app store, and most of the victims were located in China and India.
In addition, because there is no switch, controller, or optimizer in the mining code of HiddenMiner, this means that once it starts performing the mining process, it will continue until the equipment is exhausted. Given this characteristic of HiddenMiner, it is very likely that the infected device will eventually be damaged by overheating.
The researchers said that this feature is very similar to the previously reported Android malware Loapi that can cause the battery of an infected device to swell. In fact, HiddenMiner also uses Loapi-like “lock screen” technology (locking device screens when victims try to remove malware).
In further investigations, the researchers also discovered mining pool and wallet addresses associated with HiddenMiner. According to the data, the operating team behind HiddenMiner has already discovered 26 XMR (approximately US$5,360).
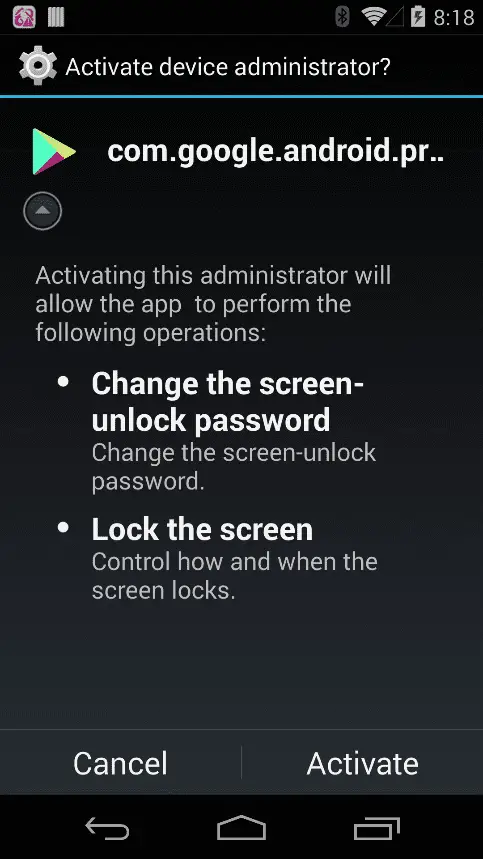
The researchers pointed out that HiddenMiner pretends to be a legitimate Google Play Store app updater that displays “com.google.android.provider” and uses the same icon as the Google Play Store.
It will ask the victim to activate it as the device administrator. This window will continue to pop up until the victim clicks the activation button. Once approved, HiddenMiner will begin mining operations in the background.
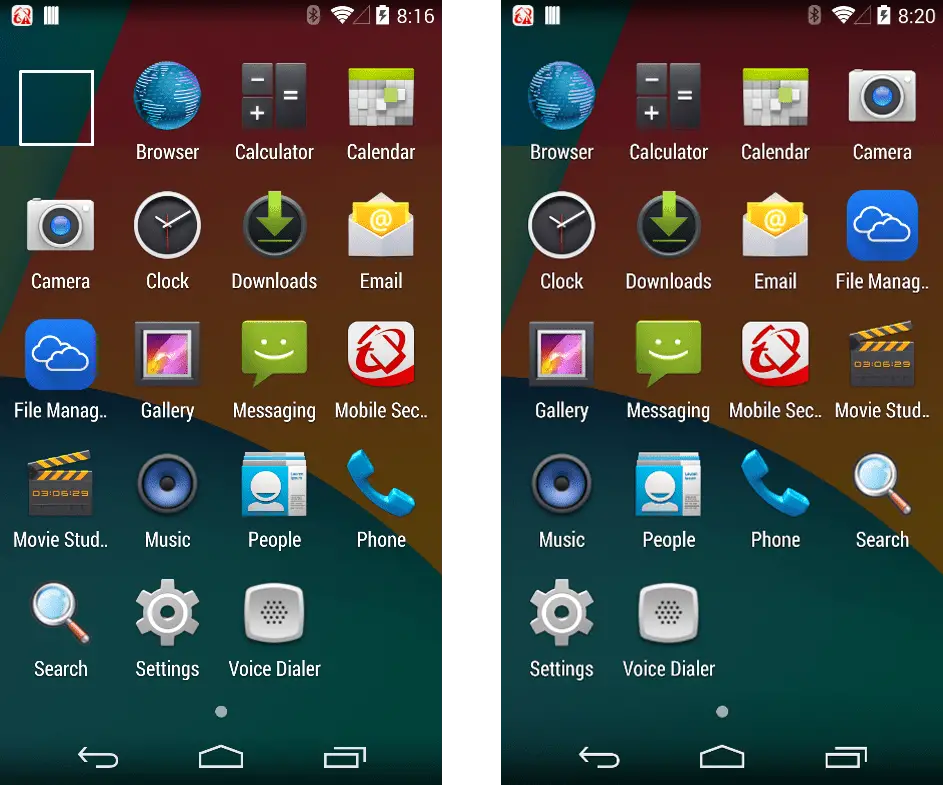
HiddenMiner also uses a variety of techniques to keep it hidden, such as clearing application tags and using transparent icons after installation. Once the victim activates it as the device administrator, it will hide from the application launcher by calling “setComponentEnableSetting()”.
In addition, HiddenMiner also has the ability to reverse analysis, bypassing the detection of most security products and automated analysis programs. It also checks whether it is running on the emulator by using an Android emulator detector posted on Github.
Researchers also said that for devices running Android 6.0 and earlier operating systems, it is not easy to remove HiddenMiner. Because, once HiddenMiner detects that the victim is trying to delete its administrator privilege, it will lock the screen of the infected device so that the victim cannot perform any operation.
In this case, the only way is to reboot the device in safe mode, and then remove HiddenMiner’s administrator privileges and HiddenMiner-infected applications.
It is worth noting that this situation does not occur on devices that use Nougat (Android 7.0) and later because Google solves this problem by reducing the permissions of the device administrator application.
Source, Image: TrendMicro