Image: Perception Point
Cybercriminals are always looking for new ways to bypass security defenses, and the latest tactic, as reported by Perception Point, involves using ZIP concatenation to deliver Trojan malware to Windows users. This technique leverages the ZIP file format’s flexibility, allowing attackers to embed malicious payloads in ways that evade detection methods.
ZIP files are widely used for bundling files, thanks to their compression efficiency and ease of use. However, this structure can be exploited. Threat actors can manipulate ZIP files by concatenating multiple ZIP archives into a single file. Perception Point’s report explains, “This discrepancy in handling concatenated ZIPs allows attackers to evade detection tools by hiding malicious payloads in parts of the archive that some ZIP readers cannot or do not access.”
The impact of this evasion tactic varies based on the ZIP reader used:
- 7zip: It reveals only part of the archive, typically the benign file, while potentially malicious content remains hidden.
- WinRAR: This tool uncovers the entire payload, exposing both benign and malicious contents.
- Windows File Explorer: It struggles to process concatenated ZIPs, often leaving hidden content invisible to users.
This variability, Perception Point highlights, allows attackers to target specific software. As noted in the report, “Many security vendors rely on popular ZIP handlers like 7zip or OS-native tools… threat actors know these tools will often miss or overlook the malicious content hidden within concatenated archives.”
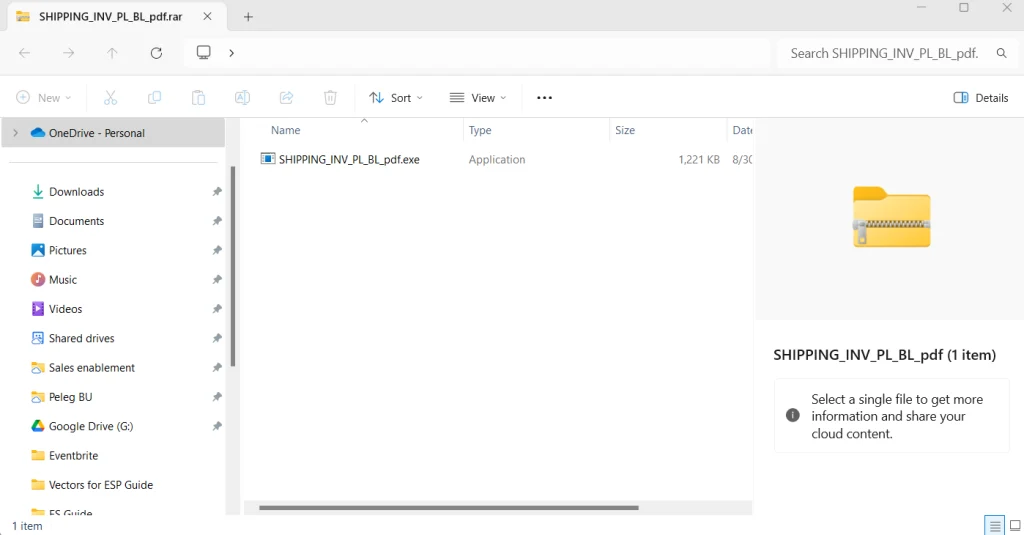
Perception Point’s analysis uncovered a phishing email campaign distributing a concatenated ZIP file disguised as a legitimate shipping document. The malicious file, SHIPPING_INV_PL_BL_pdf.rar, once opened with WinRAR or Windows File Explorer, reveals an executable Trojan hidden within the archive. This Trojan, embedded using AutoIt scripting, is capable of downloading additional malicious payloads, potentially leading to severe system compromise.
Perception Point introduced its “Recursive Unpacker,” a proprietary anti-evasion algorithm capable of detecting and extracting deeply hidden content. By analyzing each layer of concatenated ZIP files, Recursive Unpacker mitigates risks and provides enhanced visibility into potential threats.
Related Posts:
- Exploitation of URL Rewriting: A New Phishing Paradigm Threatens Cybersecurity
- PhantomBlu Campaign Unleashes Stealthy Attack – Old RAT, Dangerous New Tricks