Installer bundled with information stealer
Microsoft’s Visual Studio, a popular Integrated Development Environment (IDE), is a favored tool amongst developers for creating a variety of applications. Yet, Cyble Research and Intelligence Lab (CRIL) highlighted in a recent report that the software’s ubiquity has drawn the attention of cybercriminals, who are presently deceiving and compromising these users via a Trojanized MS Visual Studio malware.
CRIL recently uncovered a fraudulent installer masquerading as a Microsoft Visual Studio installer. This deceptive installer harbors a cookie-stealing program, meticulously designed to infiltrate and extract sensitive information stored within browser cookies. Consequently, this enables attackers to compromise user accounts and infringe upon their privacy. When unwary developers search for Visual Studio, they are inadvertently at risk of downloading this fraudulent installer.
The allure for hackers in targeting software developers is the valuable access rights to sensitive data that this demographic typically possesses. By pilfering certain information, attackers gain unauthorized access to various services and databases. Developers usually have high-level access rights, which facilitates malware propagation within the network.

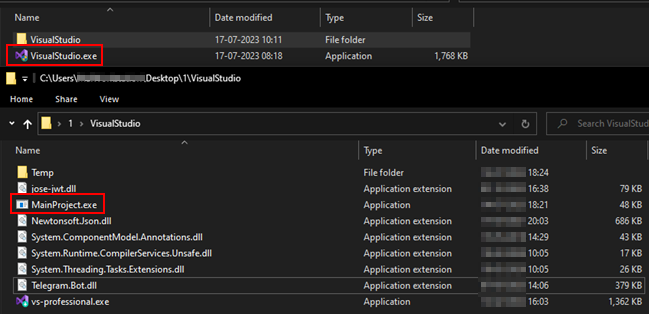
It’s understood that these malicious installers are disseminated via various deceptive means, such as phishing websites, third-party websites, file-sharing platforms, social engineering tactics, and misleading advertisements. Upon executing the malicious ‘VisualStudio.exe’ installer, it not only installs the legitimate development environment but also executes the information-stealing malware ‘MainProject.exe’.
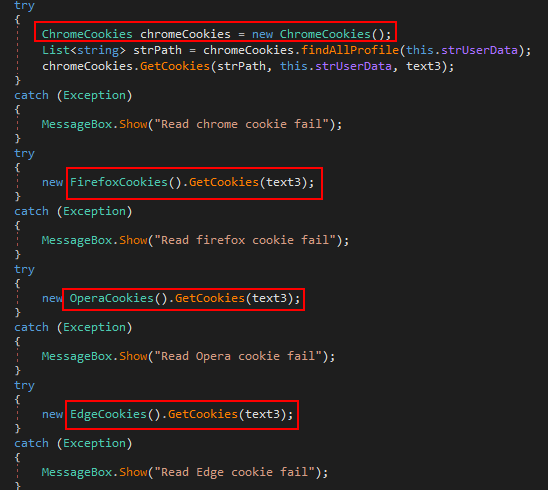
Subsequently, the information stealer continuously extracts a wealth of system details, including computer name, username, operating system version, and IP address. Upon successful extraction of system data, the information stealer continues to attack the cookies of various web browsers, including Google Chrome, Firefox, Opera, and Edge. Moreover, the stealer specifically targets cookies containing information related to well-known social media websites.
Once successful in its data pilfering, the stealer proceeds to execute the legitimate Visual Studio application ‘vs-professional.exe’, deletes the temporary folder containing the stolen data, and abruptly terminates the stealer, thereby concealing its traces.