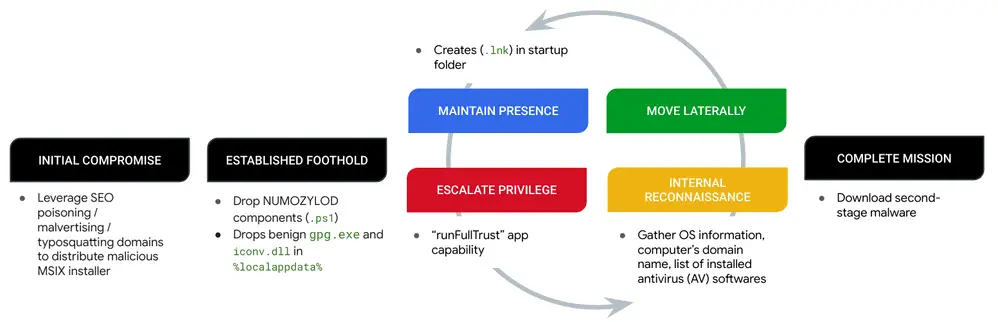
NUMOZYLOD Attack Lifecycle
Cybersecurity researchers have observed a sharp increase in infections associated with a malware distribution campaign that employs a loader known as NUMOZYLOD.
According to Mandiant cybersecurity experts, these attacks are opportunistic in nature, targeting users searching for popular business software. Infection occurs via a trojanized MSIX installer, which triggers a PowerShell script to download secondary malicious code.
NUMOZYLOD, also known as FakeBat, EugenLoader, and PaykLoader, is linked to a cyber group called Eugenfest. Mandiant specialists associate this malware with a Malware-as-a-Service (MaaS) operation orchestrated by the UNC4536 group.
The infection chain begins with Drive-by methods, where users, attempting to download popular software, are redirected to fake sites offering infected MSI installers. Among the malware distributed through FakeBat are well-known samples such as IcedID, RedLine Stealer, Lumma Stealer, SectopRAT, and Carbanak, the latter being associated with the FIN7 group.
The UNC4536 group employs a technique known as “malvertising” to distribute trojanized MSIX installers disguised as popular programs like Brave, KeePass, Notion, Steam, and Zoom. These installers are hosted on counterfeit sites that mimic legitimate resources, leading users to download compromised versions.
A distinctive feature of these attacks is the use of MSIX installers, which can execute a script before launching the primary application thanks to the startScript configuration. This makes the attacks particularly dangerous, as the malware begins its activity even before the program itself is installed.
UNC4536 essentially acts as a distributor of malware, using FakeBat as a vehicle to deliver the next stage of infection. This malware reportedly gathers system information, including data about the operating system, domain affiliation, and installed antivirus software.
In some variants, the public IP addresses of the host are also collected and sent to the command server. To maintain persistence within the system, a shortcut is created in the startup folder.
The NUMOZYLOD malware campaign examined by Mandiant underscores the critical importance of caution when downloading software from the internet, particularly from unknown or suspicious sites.
Even the most popular programs can become bait for cybercriminals who employ sophisticated techniques such as trojanized installers to infiltrate systems. Only vigilance and the use of verified sources for downloads can help minimize the risks of infection and data loss.
Related Posts:
- Malicious KMSPico installers is stealing users’ encrypted wallets
- New Malvertising Campaign Leads to Ransomware Through Trojanized Installers of WinSCP and PuTTY
- FakeBat Malware Surge Exposes the Dangers of Evolving Malvertising Campaigns
- Malvertising Campaign Uses Fake Installers to Spread Oyster Backdoor
- Atomic Stealer Malware Returns in New Disguises, Targets Mac Users’ Sensitive Data