Trust Betrayed: 55% of Insider Attacks Use Privilege Escalation
In the shadowy realm of cybersecurity, a new predator emerges from within, turning the very defenses meant to protect into weapons of betrayal. A recent report by CrowdStrike Counter Adversary Operations and the CrowdStrike Falcon® Complete team has shed light on a startling development between January 2021 and April 2023. In multiple incidents, internal users, those trusted guardians of an organization’s digital sanctum, have either exploited or attempted to exploit known vulnerabilities within their enterprise environments.
The report unveils a chilling statistic: approximately 55% of these insider threat incidents involved the unauthorized use or attempted use of privilege escalation exploits. The remaining 45% encompassed insiders who, albeit unwittingly, introduced risks to their environments through the unauthorized downloading of exploits or other offensive security tools, ostensibly for testing or training purposes.

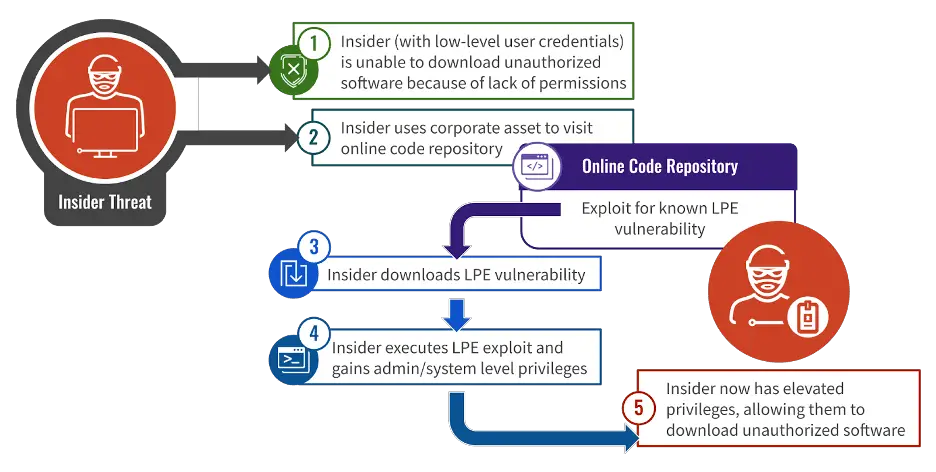
Hypothetical example of an insider threat leveraging a local privilege escalation (LPE) | Image: Crowdstrike
What makes these insider-led cybersecurity incidents particularly alarming is their growing frequency and cost. A study by the Ponemon Institute reveals a staggering 44% increase in insider threat events from 2020 to 2022. The financial burden is equally daunting, with the average cost per incident soaring to USD 648,000 for malicious and USD 485,000 for non-malicious incidents.
The essence of an insider threat lies in the abuse of legitimate access and knowledge, turning it against the organization. Whether it’s a deliberate act of subterfuge or an inadvertent error, the consequences can be devastating, resulting in substantial monetary and reputational damage.
CrowdStrike’s findings highlight that the exploitation of known vulnerabilities by insiders is not just a theoretical risk but a pressing reality. These individuals, equipped with insider knowledge and access, can exploit vulnerabilities such as the Windows Component Object Model (COM) Elevation of Privilege Vulnerability (CVE-2017-0213) or the Linux Kernel Privilege Escalation Vulnerability (CVE-2022-0847, aka DirtyPipe), among others.
Many defensive actions are used to detect and mitigate targeted intrusion and eCrime adversaries are also effective at stopping insider threats. This is due to the overlap in vulnerability usage and post-exploitation activity.
The report also underscores the criticality of privilege escalation in cyber intrusions. It’s often an intermediate step between initial access and reaching the ultimate objective. For insiders, who usually possess low-level access as part of their duties, escalating privileges without authorization is a clear abuse of their position.
CrowdStrike Counter Adversary Operations identified numerous incidents where insiders sought higher privileges to download unauthorized software, remove forensic evidence, or even troubleshoot IT systems. This witting or unwitting action introduces significant risk to the network, falling squarely under the banner of insider threats, regardless of the insider’s intentions.
The report serves as a stark reminder of the multifaceted nature of cybersecurity threats. It calls for a vigilant approach, combining robust vulnerability management, user behavior analysis, and tailored user training. As the digital landscape evolves, so must our defenses, especially against those threats that lurk within.