“TuDoor” Attack: New DNS Vulnerability Threatens Internet Security
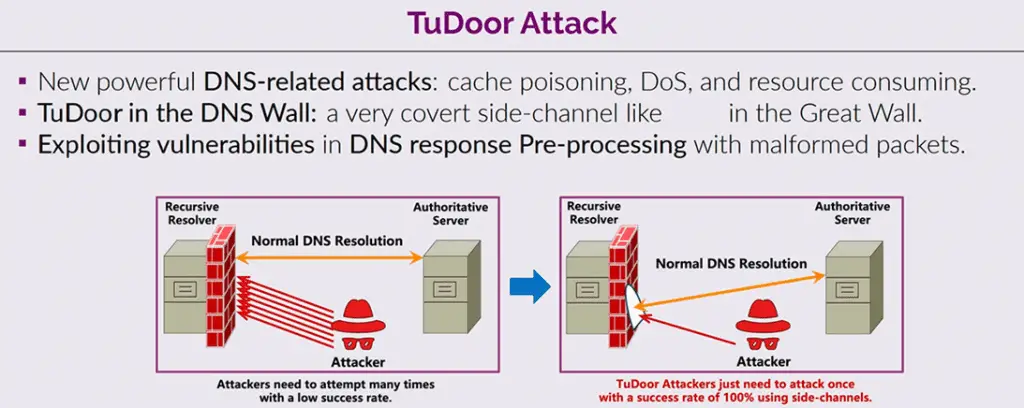
Researchers have discovered a new critical vulnerability in the Domain Name System (DNS), which enables a specialized attack termed “TuDoor.” This attack can be used to poison DNS caches, initiate denial-of-service (DoS) conditions, and deplete resources, making it a significant threat to internet security.
Experiments conducted by specialists have confirmed that the TuDoor attack is feasible and has serious implications in real-world scenarios. A total of 24 popular DNS programs, including BIND, PowerDNS, and Microsoft DNS, are vulnerable to TuDoor. Attackers can execute cache poisoning or DoS attacks against vulnerable resolvers using only a few specially crafted packets in less than a second.
To assess the extent of the problem, researchers tested 16 popular Wi-Fi router models, 6 router operating systems, 42 public DNS services, and approximately 1.8 million open DNS resolvers. The results showed that TuDoor could exploit 7 routers (and their OS), 18 public DNS services, and 424,652 (23.1%) open DNS resolvers.
The researchers adhered to best practices for responsible disclosure, notifying all affected vendors of the identified vulnerabilities. Consequently, 18 vendors, including BIND, Chrome, Cloudflare, and Microsoft, confirmed the findings and discussed remediation measures. Additionally, 33 CVE identifiers were assigned to the discovered vulnerabilities, and an online tool was proposed for their detection.
New vulnerabilities like TuDoor underscore the necessity for constant vigilance and collaboration among researchers, developers, and users. Only through joint efforts can we create a more secure digital environment where innovation and protection coexist harmoniously.





