CVE-2023-39777: XSS Vulnerability in vBulletin, No Patch Available
A critical cross-site scripting (XSS) vulnerability has been discovered in the latest version of vBulletin, which could allow attackers to gain unauthorized access to the Admin Control Panel and potentially compromise the site’s sensitive data.
For those unfamiliar with the intricacies of the web, vBulletin stands as a leading proprietary Internet forum software package. It is a brainchild of MH Sub I, LLC, previously known as Jelsoft Enterprises and vBulletin Solutions. Written primarily in PHP and relying on MariaDB or MySQL database servers, vBulletin is a formidable competitor to names like XenForo, WordPress, Joomla, Drupal, MyBB, and phpBB.

Recently, a renowned security researcher, GiongfNef, unveiled a potential flaw in vBulletin’s otherwise robust framework. The vulnerability, tracked as CVE-2023-39777, termed Cross-Site Scripting or XSS, has far-reaching implications, especially in the vBulletin version 6.0.0, with prior versions equally at risk.
XSS is a type of web security vulnerability that allows an attacker to inject malicious code into a website. This code can then be executed by other users who visit the website, potentially giving the attacker control over their accounts or stealing their personal information.
The vBulletin XSS vulnerability is due to inadequate input sanitization. This means that the software does not properly clean user input before displaying it on the page. As a result, an attacker can inject malicious scripts into the Admin Control Panel by simply entering them in a parameter field.
The bug lies in the path `/admincp`. When an authenticated user attempts to log into the Admin Control Panel, this vulnerability springs into action. The root cause is a seemingly benign oversight: poor input sanitization. This allows an attacker to input malicious scripts which then run in the context of the targeted administrator’s session, potentially stealing the admin’s credentials.
Here’s a step-by-step process:
1. Access `/admincp` in vBulletin Admin Control Panel.
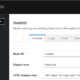
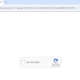
2. Manipulate the `url` parameter by injecting a JS query, such as `</script><script>alert(String.fromCharCode(88,83,83))</script>`
3. Implement the changes, and if the malicious script runs successfully, voila! The XSS vulnerability stands confirmed.
GiongfNef offers valuable insights to counter the CVE-2023-39777 vulnerability:
1. Stay Updated: Always ensure your vBulletin software is the latest version as soon as available.
2. Embrace Rigorous Checks: Enforce stringent input validation and output encoding, especially in the Admin Control Panel.
3. Comprehensive Security Reviews: Periodically analyze the software for any lurking security threats and rectify them.