Intrusion and infection | Image: G DATA
A new campaign attributed to the notorious Turla APT group is exploiting a compromised website of the Philippine Daily Inquirer to deliver a fileless backdoor, as reported by G DATA Security Lab. This sophisticated malware leverages Microsoft’s msbuild.exe tool for an Application Whitelist bypass, employs memory patching to evade detection, and disables system logging for stealthy operation.

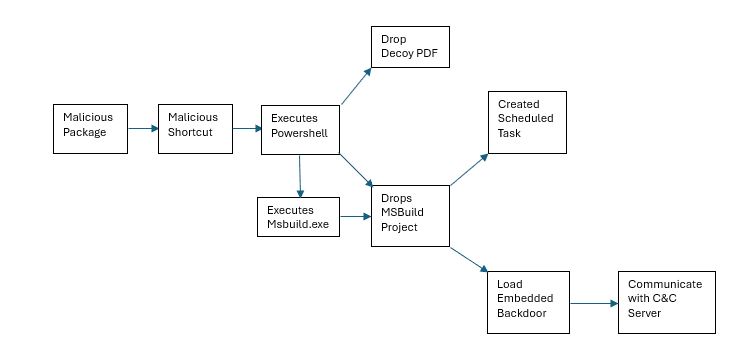
The attack initiates with a seemingly innocuous shortcut file downloaded from a compromised website of the Philippine Daily Inquirer, a leading newspaper outlet in the Philippines. This malicious package, disseminated through phishing emails, entices unsuspecting users to execute the extracted shortcut file, masquerading as a legitimate PDF document from the Philippine Statistic Authority (PSA).
Upon execution, the shortcut file triggers a PowerShell script that deploys a fileless backdoor. This backdoor exploits Microsoft’s msbuild.exe to bypass application whitelists, evading detection and creating a scheduled task to maintain persistence on the system.
Turla’s backdoor employs several sophisticated evasion tactics. By disabling Event Tracing for Windows (ETW), the malware prevents the system from logging crucial events that could reveal its presence. Additionally, it performs memory patching on critical system modules such as advapi32.dll and ntdll.dll, further obscuring its activities.
The malware also bypasses the Windows Antimalware Scan Interface (AMSI) by patching in-memory amsi.dll, allowing it to execute malicious PowerShell scripts undetected. These scripts establish a connection to a command-and-control (C2) server, receiving commands and transmitting logs back to the attacker.
The malware communicates with its command and control (C2) server via compromised websites, including a personal website. It transmits commands and receives instructions for executing malicious actions, such as disabling security features and executing PowerShell scripts.
While the attack bears similarities to previous Turla campaigns, researchers have also identified new techniques. This includes the use of LNK files, MSbuild for loading the fileless backdoor, and novel methods for disabling event logging and system modules.
To mitigate the risk of infection, users are advised to:
- Set PowerShell execution policy to “Restricted” or “AllSigned.”
- Consider removing PowerShell if not essential.
- Disable or restrict the WinRM Service.
- Remove MSBuild.exe if not needed.
- Implement application control to block unauthorized execution of msbuild.exe.