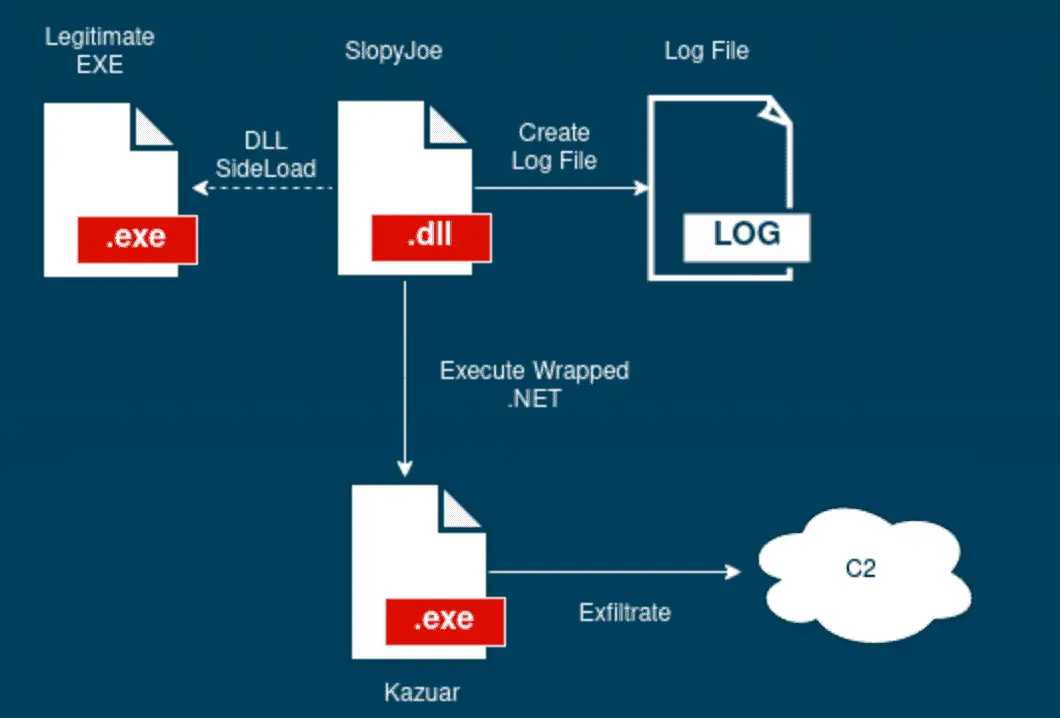
Infection chain
Research from Lab52 has uncovered a recent Turla campaign exhibiting novel tactics and a customized variant of the Kazuar trojan. This analysis offers technical insights into the campaign’s methodology and provides indicators of compromise (IOCs) to bolster defensive measures.
Turla, a cyberespionage group with suspected links to the Russian FSB, is known for its precision targeting and persistent operational tempo. Active since at least 2004, Turla targets government entities, research institutions, embassies, and industries within the energy, telecommunications, and pharmaceutical sectors globally.
The campaign investigated demonstrates Turla’s focus on targeted attacks. Initial access likely occurs via prior infection, followed by the deployment of a malicious DLL disguised within legitimate-looking libraries (SkyTel, NVIDIA, etc.). This ‘Pelmeni Wrapper’ loads the next stage payload.

The Pelmeni Wrapper exhibits the following functionality:
- Operational Logging: Generates a hidden log file using randomized names and extensions for tracking campaign activity.
- Payload Delivery: Employs a custom decryption scheme leveraging a pseudorandom number generator to facilitate function loading and execution.
- Execution Flow Redirection: Manipulates process threads and injects code to divert execution to a decrypted .NET assembly containing the core malware.
The climax of Turla‘s elaborate scheme culminates with the activation of Kazuar, a multiplatform trojan horse that has been a staple in Turla’s arsenal since its discovery in 2017. Lab52’s analysis sheds light on subtle yet significant evolutions in Kazuar’s deployment, noting a new protocol for data exfiltration and variations in the logging directory – deviations that mark this sample’s uniqueness from its predecessors.
The extracted .NET assembly is a modified Kazuar trojan. Key differences compared to previously analyzed versions include:
- Expanded Exfiltration Protocol: Support for socket-based exfiltration enhances the malware’s communication adaptability.
- Modified Log Storage: A shift in log directory placement suggests customization for this campaign.
This research sheds light on Turla’s evolving tactics and their ongoing use of the Kazuar trojan. As APTs adapt, understanding their techniques remains critical for proactive defense. By integrating threat intelligence and remaining vigilant, organizations can mitigate the risks posed by this advanced threat actor.