Attack Methodology
A recent investigation by Trustwave SpiderLabs’ Email Security team has uncovered a sophisticated Phishing-as-a-Service (PaaS) platform known as Tycoon Group. This platform’s capabilities and ease of use highlight the growing threat posed by PaaS offerings to organizations and individuals alike.
What is Tycoon Group?
Sold and marketed on Telegram for as low as $120, Tycoon Group offers features designed to outmaneuver modern cybersecurity measures, including the ability to bypass Microsoft’s two-factor authentication and leverage Cloudflare to evade antibot measures. Key features include:
- Evasion Tactics: The ability to bypass even advanced security measures like Microsoft’s two-factor authentication and Cloudflare anti-bot defenses
- Real-time Control: WebSocket technology gives attackers near-instant access to stolen data as soon as a victim is tricked.
- Continuous Development: Tycoon Group’s frequent updates, including Gmail-focused attacks and ADFS cookie theft, mean the threat is never static.
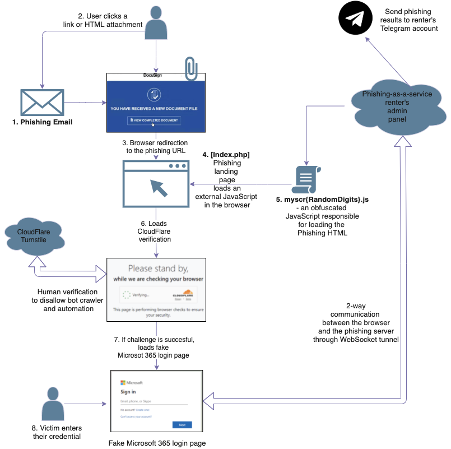
Attack Methodology

Tycoon Group’s phishing scheme starts with the use of trusted domains and cloud-based services to disguise the true nature of phishing URLs, employing services like DocuSign, Microsoft Cloud, and Google Drive as either redirectors or hosts for decoy documents. These documents lure unsuspecting users to the main phishing landing page, a carefully constructed trap designed to harvest user credentials.
The technical backbone of Tycoon’s phishing pages is a PHP script named “index.php,” complemented by a JavaScript file “myscr,” which together generate the HTML code for the phishing page. These components employ obfuscation techniques to evade detection, using a blend of Base64 encoding, XOR operations, and opaque predicates to mask their true intent.
Tycoon Group’s introduction of WebSocket for data exfiltration marks a significant innovation in phishing attacks. This method allows for seamless communication between the victim’s browser and the phisher’s server, facilitating the efficient transmission of stolen credentials. This capability, combined with recent updates to target Gmail users and bypass two-factor authentication, highlights the group’s commitment to evolving its tools in line with advancements in cybersecurity.
One of the most alarming aspects of Tycoon Group’s service is its user-friendly admin panel, which allows subscribers to easily manage phishing campaigns and harvested credentials. This panel not only simplifies the process of conducting cyber attacks but also democratizes access to sophisticated phishing tools, lowering the barrier to entry for aspiring cyber criminals.
Analysis: The PaaS Threat
The rise of PaaS models like Tycoon Group signifies a troubling trend in cybercrime, where sophisticated tools and services are made available to a wide array of actors, including those with minimal technical expertise. These simple cybercrime tools increase the volume and sophistication of phishing attacks, posing significant challenges to individuals and organizations alike.