Uitkyk: Runtime memory analysis framework to identify Android malware
Uitkyk is a framework that allows you to identify Android malware according to the instantiated objects on the heap for a specific Android process.
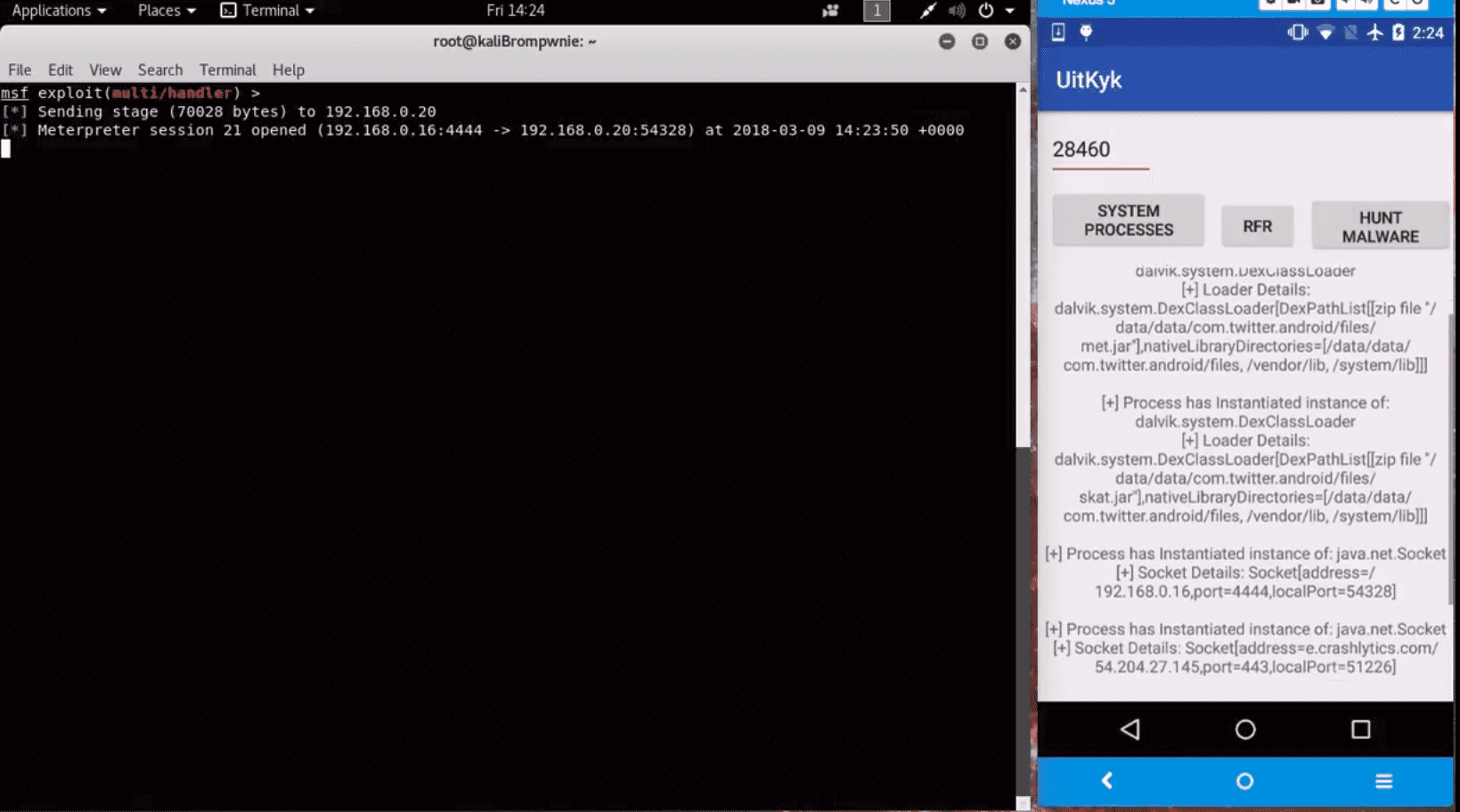
Uitkyk scans the heap of a specific Android process using custom Frida scripts to identify malicious behaviour according to the objects instantiated by a specific Android process.
It can be used in multiple ways. Firstly as an Android library with existing Android applications which can be done by adding the code in the “Android Library” folder or the AAR release as a library to your Android application. Secondly as a standalone application which can be done by building and running the Android application located in the “UitkykDemoApp” folder. Thirdly, Uitkyk can be implemented using the Frida CLI by running the Frida scripts located in the “FridaScripts” folder.
Requirement
A Frida Server instance is required to be running on the device. By default Uitkyk makes use of Frida running on tcp:host=127.0.0.1,port=27042 but a custom host and IP can be used.
To run the Frida server binary on your device, you could run the command:
./fridaBinary &&
Demo
Source: https://github.com/brompwnie/