UNC1151 Escalates Cyber Warfare: Attacks Target Ukrainian Defense Infrastructure
Cyble Research and Intelligence Labs (CRIL) has uncovered a sophisticated cyber campaign linked to the threat actor group UNC1151, known for its ties to the Belarusian government and its involvement in the GhostWriter information operation. This latest attack targeted the Ukrainian Ministry of Defence and military base A0000, demonstrating an alarming evolution in tactics and techniques.
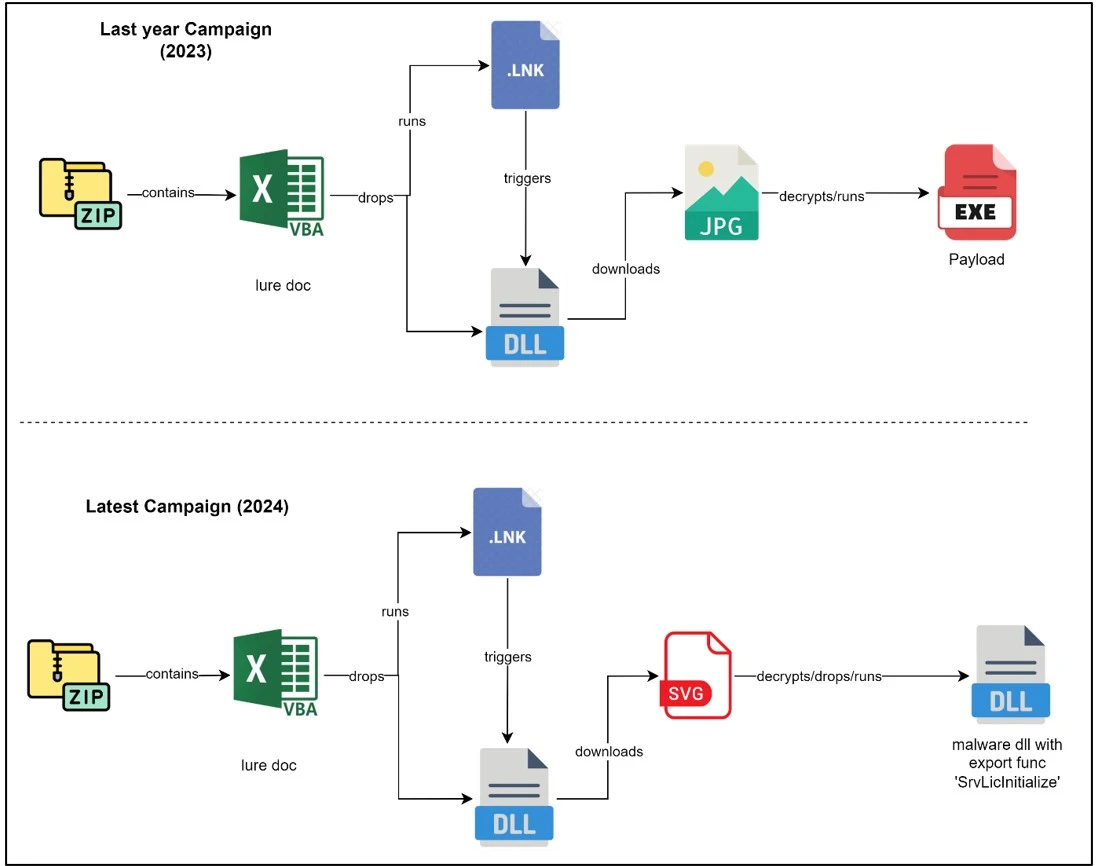
The infection chain typically begins with a spam email containing a compressed attachment that includes a malicious Excel worksheet. When the Excel document is executed, it runs embedded VBA Macro content that drops an LNK and a DLL file. Executing the LNK file triggers the DLL loader, leading to a malware infection on the target system.
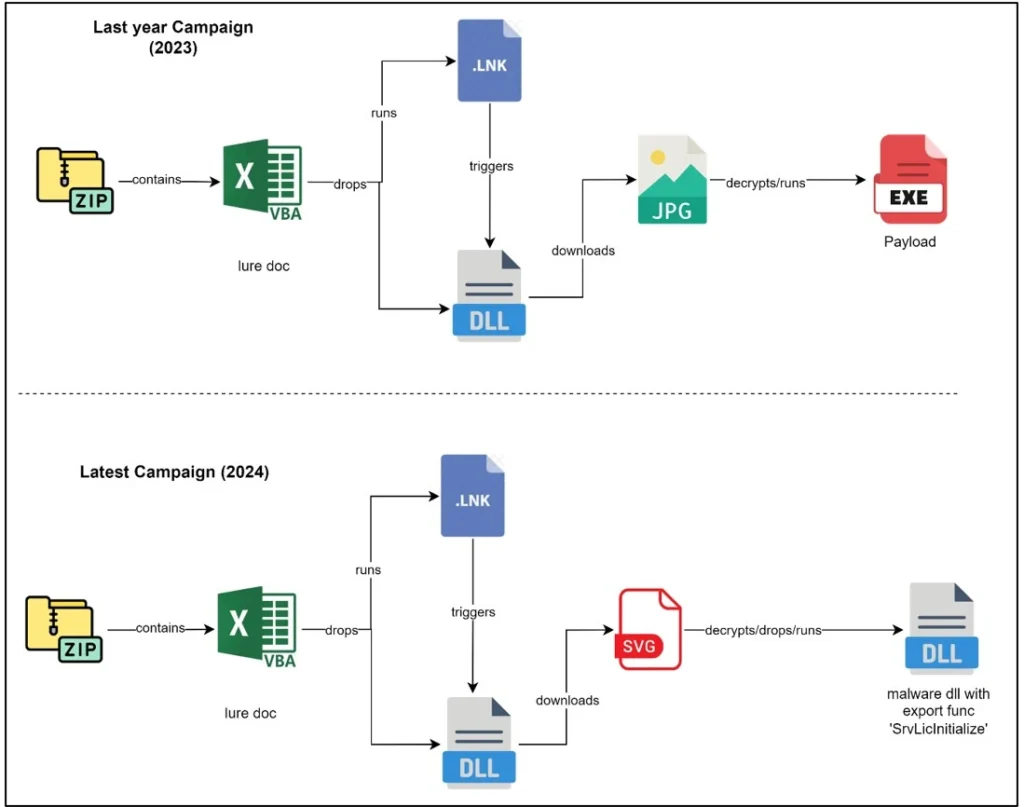
Differences in the infection chain of the UNC1151 malware campaign | Image: CRIL
In previous campaigns, UNC1151 employed DLL loaders that downloaded an encrypted JPG file, which was then decrypted to deploy a final payload executable. However, the latest campaign shows a shift in tactics. The TA likely downloads an encrypted SVG file, which decrypts to deliver another DLL payload file. The final payload possibly includes AgentTesla, Cobalt Strike beacons, and njRAT, as observed in previous UNC1151 campaigns.
The initial campaign observed in April 2024 targeted the Ukrainian Military, employing a combination of drone image files and a malicious Excel spreadsheet. The strategy involved using socially engineered Excel lures sent via spam email to convince targeted users to enable macros, triggering the execution chain.
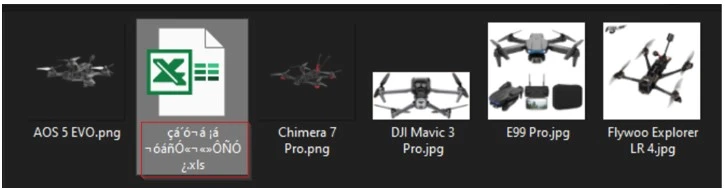
Files inside the compressed attachment | Image: CRIL
Upon opening the Excel file, a button labeled ‘Enable Content’ is displayed. Clicking this button initiates the execution of the embedded VBA Macro, dropping a shortcut file named “CybereasonActiveProbe.lnk” and a malicious DLL file named “F072d76c85A40hjf9a3c0ab.dll.” The LNK file is executed using Rundll32.exe, leading to the DLL loader and ultimately, a malware infection.
The DLL loader is an obfuscated .NET file that carries out various malicious actions. These include terminating specific processes to evade detection, modifying system security protocols, and downloading additional malicious content from specified URLs. The downloaded file, likely another DLL, is decrypted and executed, leading to the final malware infection.
UNC1151’s sustained cyber offensive against Ukraine represents a significant and evolving threat to national security. The group’s advanced tactics and persistent targeting underscore the importance of a comprehensive and collaborative approach to cybersecurity. By understanding the evolving threat landscape and adopting proactive measures, organizations and governments can better protect critical infrastructure and sensitive information from sophisticated adversaries like UNC1151.





