Infection lifecycle diagram | Image: Mandiant
Mandiant has unveiled a new wave of cyber-espionage attacks orchestrated by the North Korea-linked group UNC2970. This group has recently employed a sophisticated method to deliver a custom backdoor named MISTPEN, by trojanizing a legitimate PDF reader, SumatraPDF. The report highlights that UNC2970 is primarily targeting senior-level employees in critical industries such as energy and aerospace through highly tailored phishing campaigns.
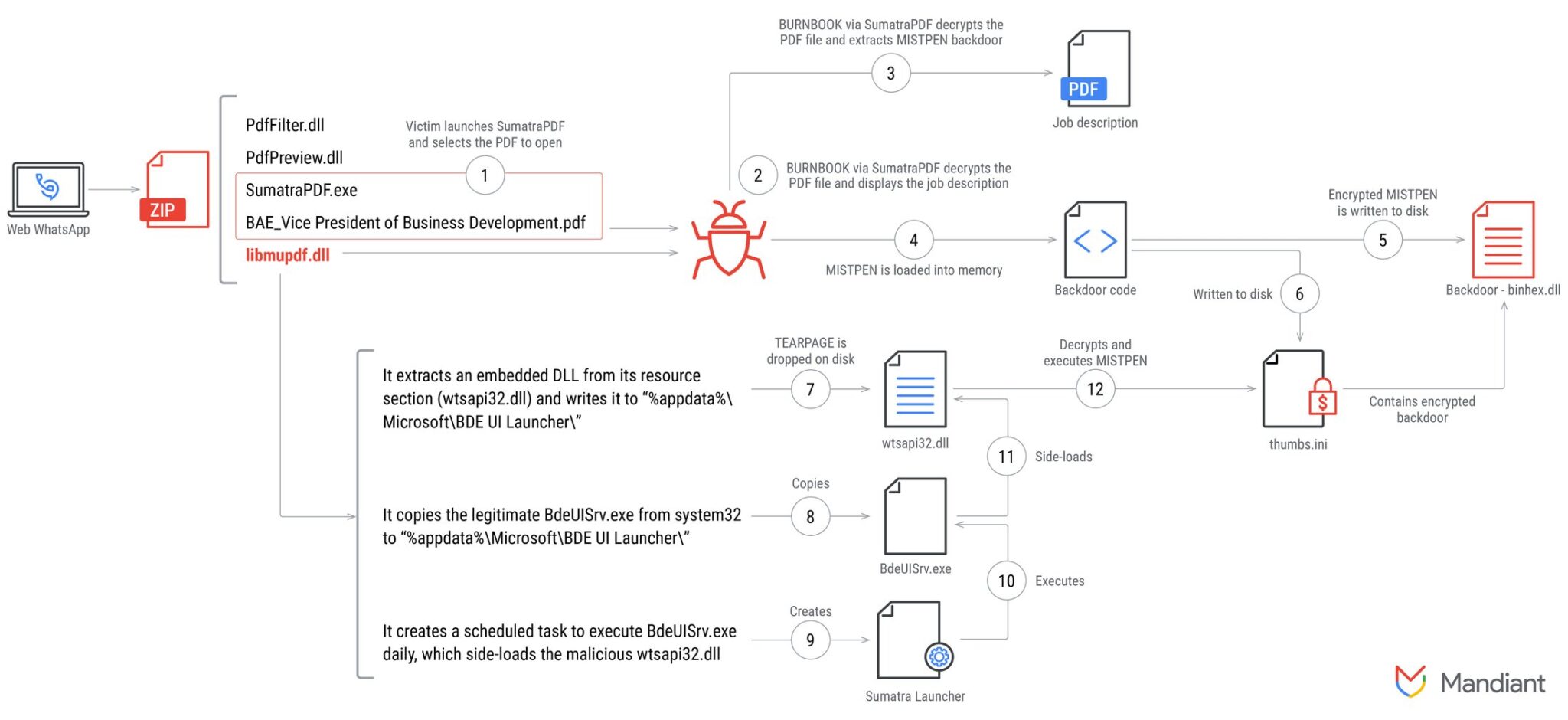
In June 2024, UNC2970 was caught using phishing lures disguised as job opportunities from well-known companies to entice victims. These lures are tailored to fit the job profiles of their targets, often senior employees with access to sensitive information. Victims receive an email or WhatsApp message with a malicious ZIP file, which contains a trojanized version of SumatraPDF and an encrypted PDF file, appearing to be the job description.
When the victim opens the file using the provided SumatraPDF executable, the modified application launches a sophisticated infection chain. The real PDF file is displayed, but behind the scenes, a payload is activated. The trojanized PDF reader, along with other files, deploys a backdoor—MISTPEN—which allows the attackers to remotely control the compromised system.
The ZIP archive includes:
- BAE_Vice President of Business Development.pdf: A trojanized job description that also acts as a carrier for the MISTPEN backdoor.
- libmupdf.dll: A malicious DLL file that serves as a dropper, loading MISTPEN into the system.
- SumatraPDF.exe: A legitimate PDF reader modified to include malicious functionality.
Once the victim opens the PDF, the infection process begins. The trojanized SumatraPDF decrypts and loads the backdoor in memory, executing MISTPEN. This backdoor is a lightweight, stealthy tool designed to download and execute additional payloads. By using DLL hijacking techniques and persistence mechanisms, the attackers ensure the malware remains on the victim’s system long after initial infection.
Mandiant’s analysis revealed that UNC2970 constantly refines its tactics. For instance, the attackers modified the open-source SumatraPDF code to avoid detection, and implemented a network connectivity check, which blocks the PDF from being displayed if the infected machine cannot connect to Google. This prevents offline analysis of the payload.
Additionally, UNC2970 has shown the ability to craft highly convincing job descriptions by subtly altering legitimate postings. These modifications are designed to better align with the profile of the target victim, making the lure even more effective.
MISTPEN is a trojanized version of a legitimate Notepad++ plugin and serves as the core of the malware’s operation. It supports several commands, allowing the attackers to execute arbitrary code, terminate processes, and maintain persistence. Communication with the command-and-control (C2) server is handled over HTTP, utilizing legitimate services like Microsoft Graph API, which helps the malware blend into normal network traffic.
UNC2970’s campaign is focused on targeting critical infrastructure sectors, including energy and aerospace. Their phishing tactics, combined with the stealthy deployment of MISTPEN, pose a serious threat to organizations involved in national security and key economic sectors. The group has been observed targeting entities across the United States, United Kingdom, Germany, and several other countries, indicating a widespread and coordinated effort.
Organizations operating in critical infrastructure sectors should immediately review their defenses against such spear-phishing attacks.
Related Posts:
- Trojanized MS Visual Studio targeting developers is spreading
- Widespread Supply Chain Attack on NPM: Trojanized jQuery Discovered
- New Malvertising Campaign Leads to Ransomware Through Trojanized Installers of WinSCP and PuTTY
- Malware Hiding in PDFs: What You Need to Know
- Attacker pushes trojanized BitTorrent software, infects nearly 500,000 computers within 12 hours