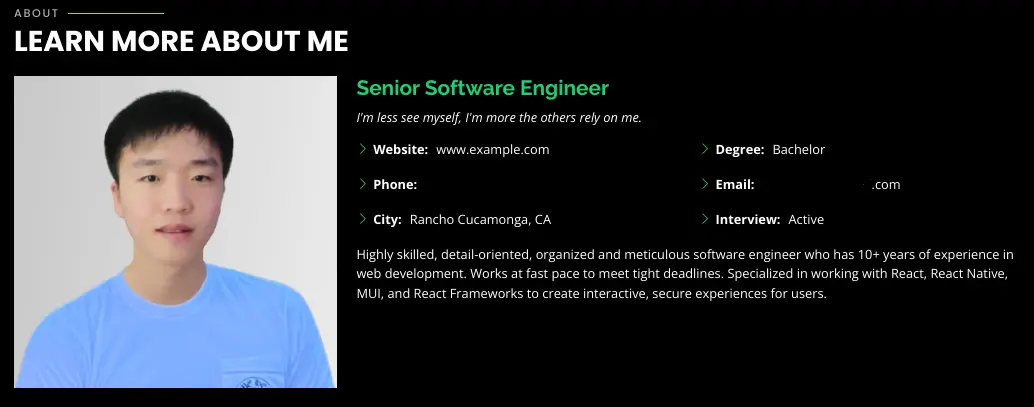
Observed image of threat actor resume | Image: Mandiant
In a recent report, Mandiant has uncovered the ongoing and sophisticated operations of a North Korean-aligned cyber group designated as UNC5267. This group comprises North Korean IT workers deployed abroad—primarily to China and Russia—by the DPRK government to infiltrate Western companies, particularly those in the U.S. tech sector. These workers, operating under false identities, secure remote work positions to gain financial benefits for the regime and possibly establish access for future cyber-espionage or disruptive operations.
UNC5267’s operations have been active since at least 2018 and remain a present-day threat. Unlike many traditional cyber groups, UNC5267 is not a centralized unit but a decentralized network of individuals acting under government directive. These individuals leverage fraudulent resumes and stolen identities to apply for 100% remote jobs in the tech industry. Mandiant’s report revealed that “UNC5267 operators have primarily applied for positions that offer 100% remote work,” allowing them to work covertly from overseas while pretending to be located in the U.S.
In one case, a single facilitator working with North Korean IT workers compromised over 60 identities of U.S. citizens and impacted more than 300 companies. This operation generated approximately $6.8 million in revenue between 2020 and 2023.
Mandiant discovered that UNC5267 employs various tactics to secure positions at Western firms, primarily using fraudulent resumes and fabricated credentials. A hallmark of these operations is the use of fake profiles across multiple platforms, including LinkedIn and Netlify. In one instance, a suspected North Korean IT worker was found using a resume with stolen images and fabricated testimonials, designed to create a convincing persona as a software engineer.
Mandiant highlights the complexity of these deceptions, noting, “The resumes provide evidence of the DPRK IT workers utilizing multiple personas in attempts to gain employment across multiple organizations.” In some cases, resumes list education credentials from universities outside of North America, making it difficult for North American employers to verify their authenticity.
Once employed, UNC5267 workers frequently gain elevated access to company networks and systems, presenting a significant security risk. While Mandiant has primarily observed these workers performing their official job duties, their elevated access leaves victim companies vulnerable to both financial exploitation and potential espionage.
Mandiant has also tracked the use of laptop farms—locations where multiple corporate laptops are set up to be remotely accessed by DPRK workers. These setups are often staffed by a facilitator who manages the devices, allowing the IT workers to control the systems from abroad. The group commonly uses remote management tools such as AnyDesk, Chrome Remote Desktop, and TeamViewer to access these corporate laptops remotely, all while using VPNs like Astrill VPN to mask their true locations.
In response to this growing threat, Mandiant advises companies to adopt more stringent hiring practices and technical defenses. Recommendations include thorough background checks, including the use of biometric information to verify identities, and requiring candidates to use cameras during interviews to confirm their appearance matches their online profiles.
Technical defenses should focus on monitoring for the installation of multiple remote access tools, the use of VPNs, and suspicious connections to corporate systems. Mandiant also suggests verifying laptop serial numbers during onboarding and utilizing hardware-based multi-factor authentication to enforce physical access to corporate devices.
As Mandiant warns, “Countering the threat posed by North Korean cyber actors requires a multifaceted approach,” combining technical defenses with proactive threat detection and user education. Companies must act now to protect their assets from this sophisticated and evolving threat.
Related Posts:
- LockBit Ransomware: The Hidden Threat in Resume Word Files
- A Local Privilege Escalation flaw exists on Western Digital My Cloud
- Western Digital Cyberattack: Unveiling the Stolen Data and Fallout