Unit 42 Exposes Parrot TDS: A Global Malware Menace
Recently, Unit 42 from Palo Alto Networks provided an in-depth analysis of the Parrot TDS (Traffic Direction System). Emerging in 2021, this sophisticated malware campaign has evolved rapidly, leaving a trail of compromised websites and stolen data across the globe. Parrot TDS, known for injecting malicious scripts into existing JavaScript, has become a significant concern for cybersecurity experts and website administrators alike.
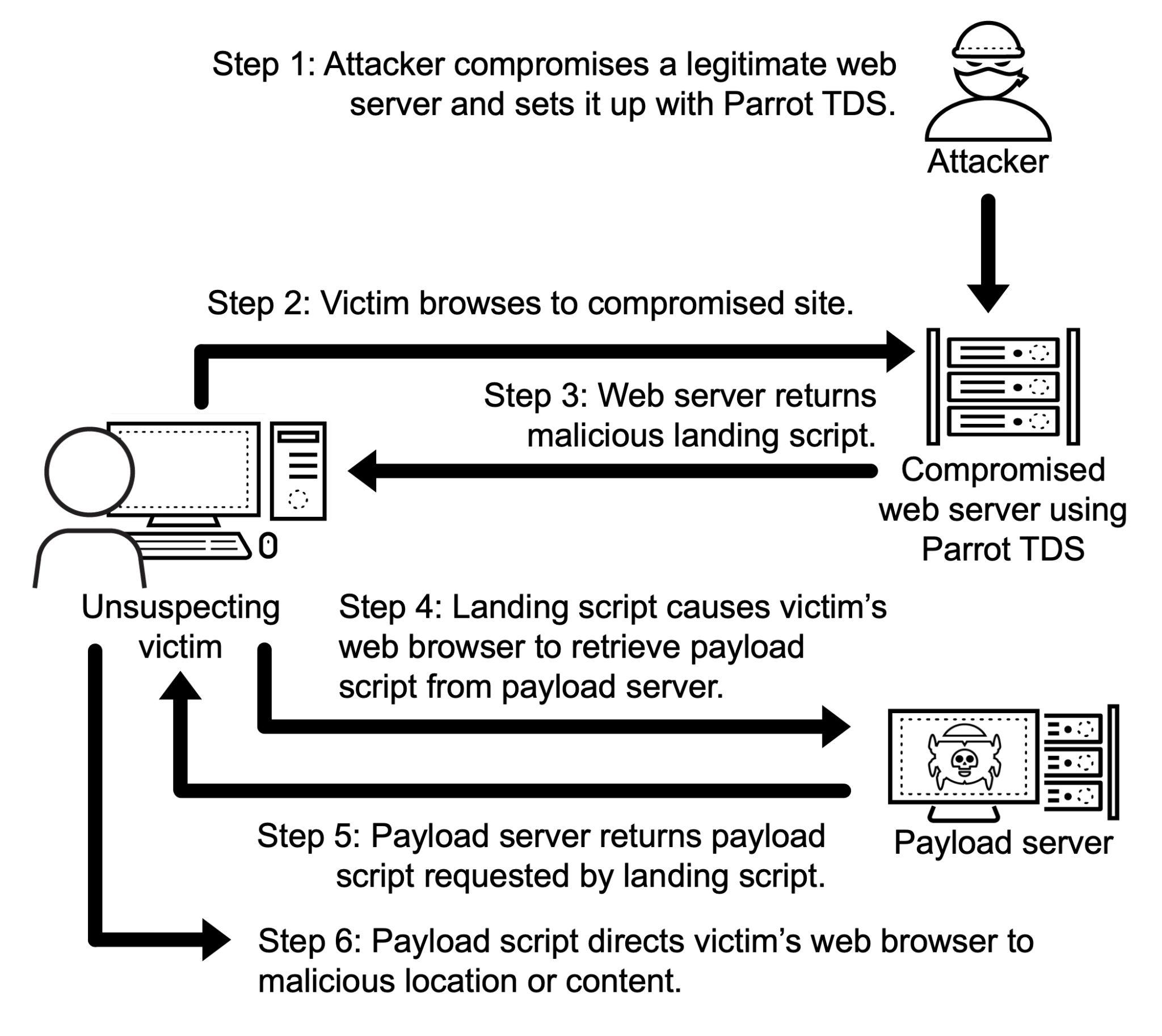
Parrot TDS operates by embedding two types of scripts into web pages: a landing script that profiles potential victims and a payload script that redirects browsers to harmful content. This dual-component structure allows Parrot TDS to efficiently target and compromise users’ systems.

Chain of events for payload distribution through Parrot TDS | Image: Unit 42
The malicious journey of Parrot TDS began in 2021, but its roots trace back to 2019. Throughout this period, various iterations of the malware have surfaced, each more sophisticated than the last. The campaign’s resilience and adaptability are evident in the numerous versions of its injected JavaScript, each employing increasingly intricate obfuscation techniques and encryption methods.
Parrot TDS’s reach is not confined to any specific region or sector. Its victims span a diverse range of industries and geographic locations, underscoring its role as a significant global cybersecurity threat. The attackers utilize automated tools to exploit known vulnerabilities, often targeting content management systems like WordPress and Joomla.
The continuous evolution of Parrot TDS necessitates vigilant and proactive measures by website administrators. Regular audits, searching for specific keywords associated with Parrot TDS, and monitoring for unusual .php files are critical steps in detecting and mitigating this threat.





