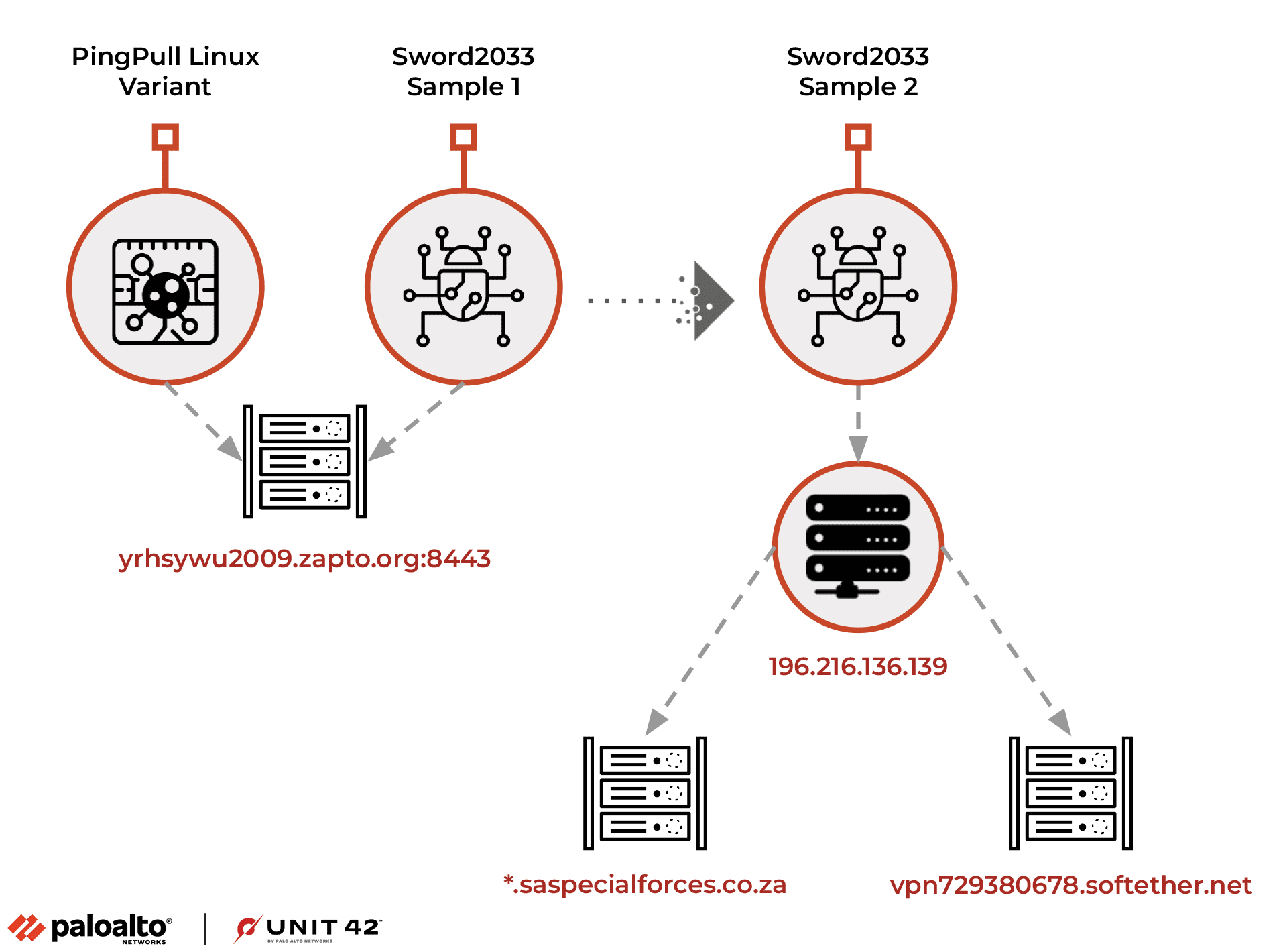
PingPull/Sword2033 infrastructure visualization. | Image: Unit 42
Researchers from Unit 42 have recently discovered a new variant of the PingPull malware, which targets Linux systems and is used by the Chinese APT group, Alloy Taurus. This group, also known as GALLIUM or Softcell, is known for conducting cyberespionage campaigns against telecommunications companies, financial institutions, and government entities in Asia, Europe, and Africa. In addition to the PingPull variant, the researchers also identified a backdoor they track as Sword2033, linked to the same command and control (C2) infrastructure.
The first samples of PingPull malware were found in September 2021, and its functionality was outlined by Unit 42 in June 2022. The newly discovered Linux variant of PingPull malware communicates with a domain over port 8443 for C2 and uses a statically linked OpenSSL library. It employs the same AES key as the original Windows PE variant of PingPull and shares several similarities with the web shell China Chopper.

The Sword2033 backdoor, designed to connect to port 8443 over HTTPS, supports three basic functions: uploading a file to the system, downloading a file from the system, and executing a command. The C2 domain analysis revealed links to Alloy Taurus activities, with evidence of the domain impersonating the South African military. In February 2023, South Africa participated in combined naval exercises with Russia and China, making this impersonation uniquely notable.
Furthermore, the researchers found sustained connections between the Sword2033 C2 server and IP hosting subdomains for an organization financing long-term urban infrastructure development projects in Nepal. This discovery highlights the ongoing threat posed by the Alloy Taurus group and emphasizes the need for organizations to remain vigilant in their cybersecurity efforts.