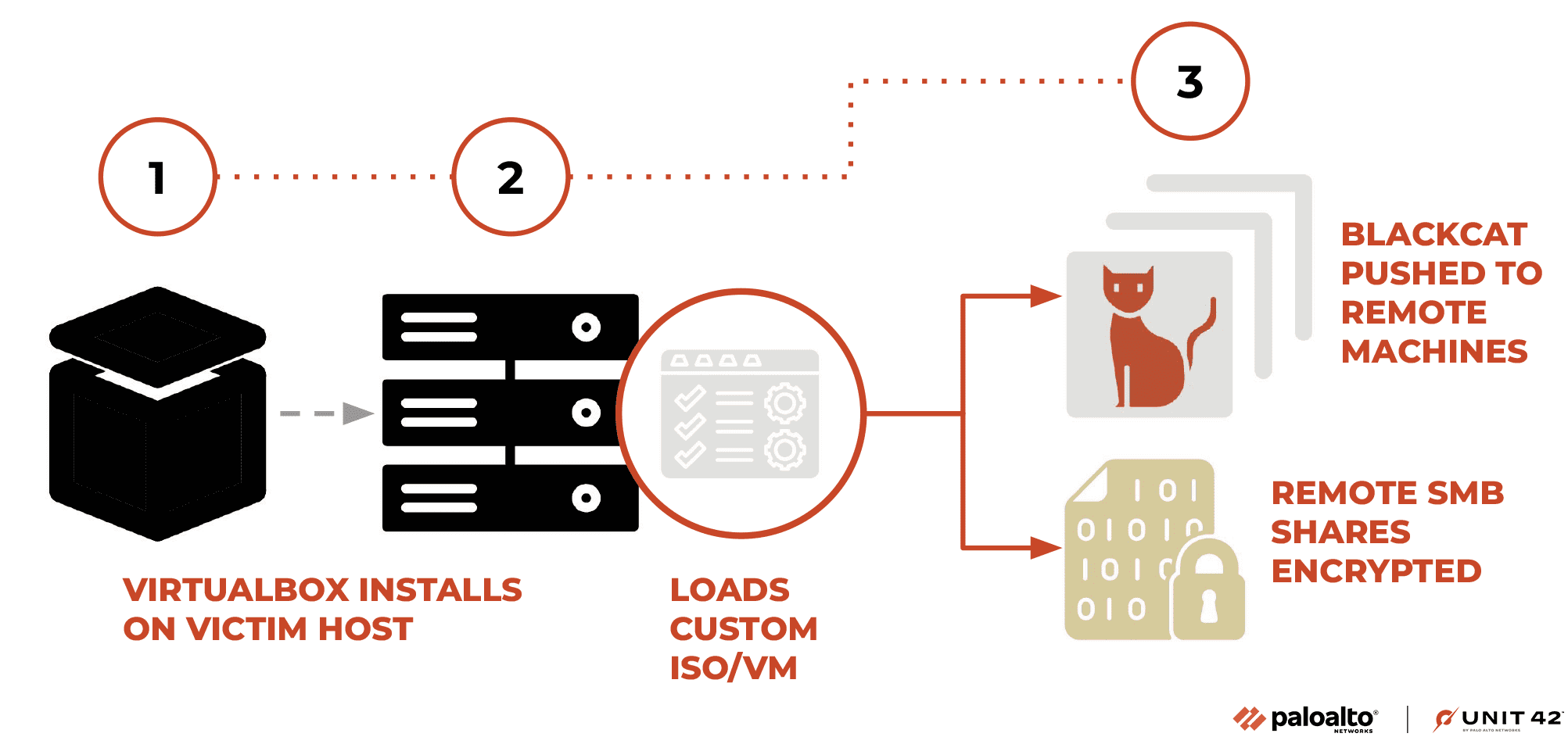
Diagram of Munchkin tool process.
Researchers from Palo Alto Networks’ Unit 42 have discovered that the cybercrime syndicate, ALPHV/BlackCat, has initiated the deployment of a novel tool dubbed ‘Munchkin’. This tool capitalizes on virtual machines to discreetly propagate encryptions across network devices. Munchkin empowers BlackCat to function on remote systems or to encrypt network partitions of SMB (Server Message Block) and CIFS (Common Internet File System).
The integration of Munchkin into BlackCat’s already formidable and sophisticated arsenal amplifies the allure of RaaS (Ransomware-as-a-Service) for cybercriminals aspiring to collaborate with BlackCat in the distribution of ransomware software.

Munchkin is essentially a customized distribution of Linux Alpine OS in ISO format. Once a device is compromised, the hackers install VirtualBox and cultivate a new virtual machine utilizing the Munchkin ISO file. The resultant virtual machine incorporates an array of scripts and utilities, enabling cybercriminals to harvest passwords, proliferate through the network, formulate the BlackCat ‘Sphynx’ encryptor, and execute code on devices.
Upon the machine’s boot-up, the password is altered to one solely known to the assailants. Using the ‘tmux’ utility, the primary ‘controller’ module is instigated, which subsequently commences the downloading of attack scripts. This controller module employs an embedded configuration file, which provides access tokens, victim credentials, configuration directives, blacklists of folders and files, tasks to be executed, and target hosts for encryption.
Embedded within the malware’s code, Unit 42 identified a missive from BlackCat’s authors directed at their associates. This message cautions the imperative of erasing the ISO image from target systems due to the lack of encryption on configurations, in a bid to preclude malware sample leakages and negotiations between the extorters and the victim.
Munchkin simplifies the execution of myriad tasks for BlackCat associates, adeptly circumventing the defense mechanisms on the victim’s device. Virtual machines offer a layer of insulation from the operating system, rendering their detection and analysis more intricate. The selection of Alpine OS ensures a minimal digital footprint, while automated operations diminish the need for manual interference.
The modularity of Munchkin, which offers an array of Python scripts, distinct configurations, and the facility to swap payloads as required, renders the tool effortlessly adaptable to specific objectives or campaigns.