Universal Radio Hacker v2.9.5 releases: investigate wireless protocols like a boss
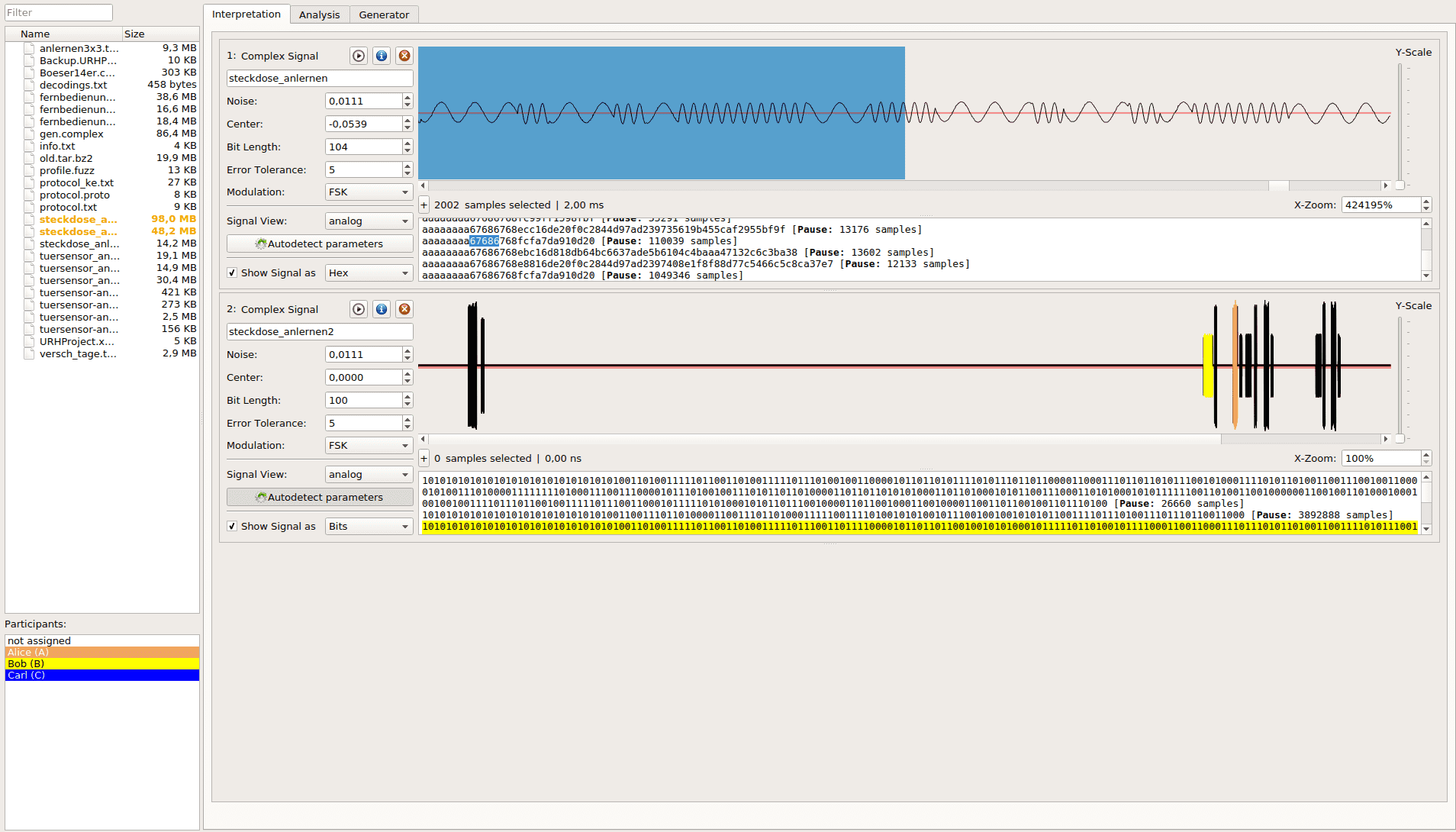
The Universal Radio Hacker (URH) is a tool for analyzing unknown wireless protocols. With the rise of the Internet of Things (IoT) such protocols often appear in the wild. Many IoT devices operate on frequencies like 433.92 MHz or 868.3 MHz and use proprietary protocols for communication. Reverse-engineering such protocols can be fascinating (»What does my fridge talks about?«) and reveal serious security leaks e.g. when bypassing smart alarm systems and door locks.
The Universal Radio Hacker is a software for investigating unknown wireless protocols. Features include
- hardware interfaces for common Software Defined Radios
- easy demodulation of signals
- assigning participants to keep an overview of your data
- customizable decodings to crack even sophisticated encodings like CC1101 data whitening
- assign labels to reveal the logic of the protocol
- fuzzing component to find security leaks
- modulation support to inject the data back into the system
With the rise of the Internet of Things (IoT) such protocols often appear in the wild. Many IoT devices operate on frequencies like 433.92 MHz or 868.3 MHz and use proprietary protocols for communication. Reverse-engineering such protocols can be fascinating (»What does my fridge talks about?«) and reveal serious security leaks e.g. when bypassing smart alarm systems and door locks.
So how can we join this game? Software Defined Radios (SDR) are the answer for this. Such devices allow sending and receiving on nearly arbitrary frequencies. Such devices allow sending and receiving on nearly arbitrary frequencies.
Like the name suggests SDRs need software to be properly operated. This is where the Universal Radio Hacker comes into play: It takes the samples from the SDR and transforms them into binary information (bits). But this is only the beginning: URH is designed to help you throughout the entire process of attacking the wireless communication of IoT devices.
In the upcoming sections, you will learn how to use URH and reverse engineer wireless protocols in minutes.
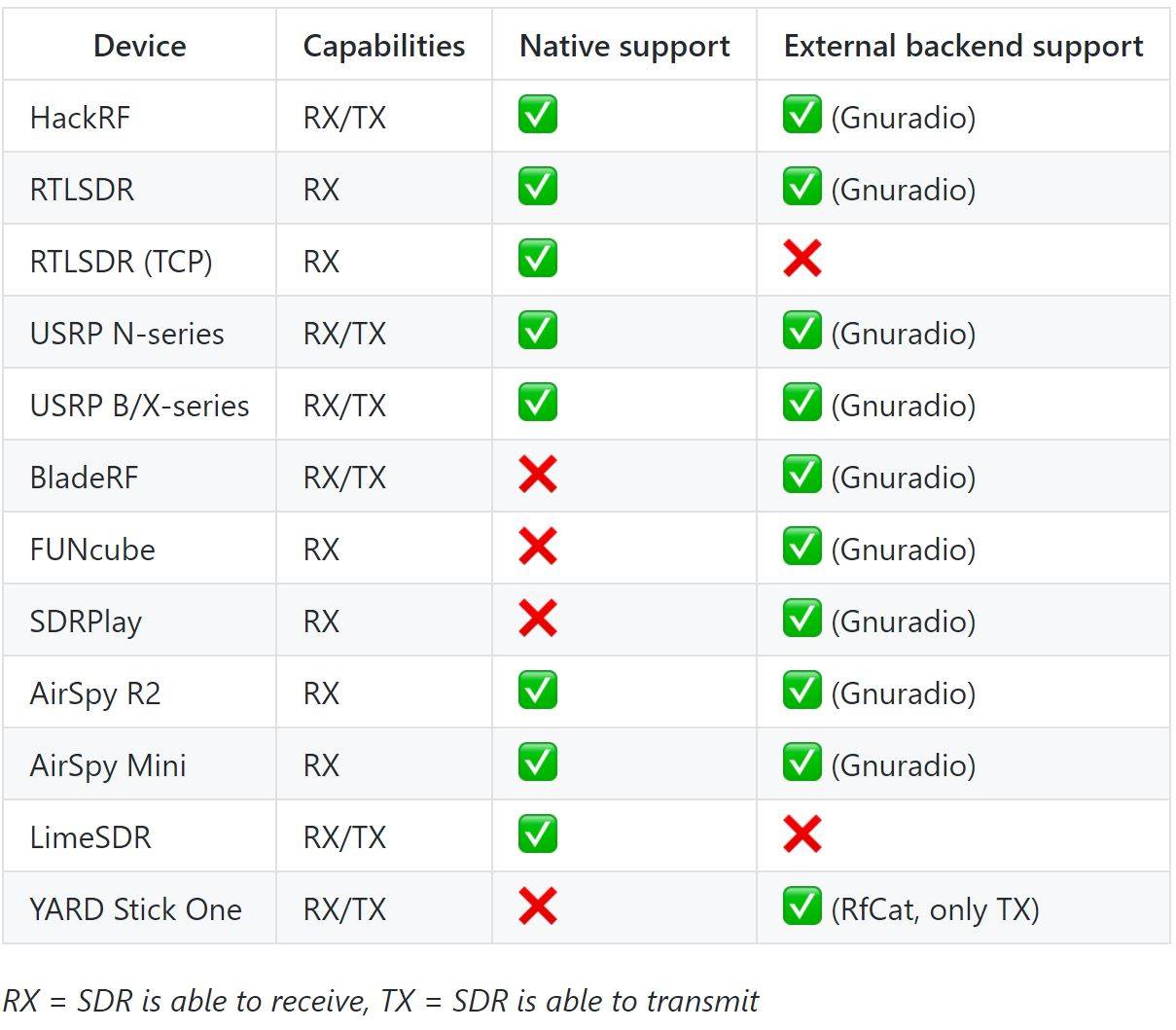
Supported devices
Changelog v2.9.5
- CI: Add missing
envdefinition to twine upload by @jopohl in #1029 - Fix error in WSPChecksum by @andynoack in #1046
- Bias-T checkbox for RTL-SDR device settings screen #2 by @jirjirjir in #1057
- pin to Cython version <3.0.0 by @jopohl in #1063
- Add noexcept to fix compiling of cythonext by @andynoack in #1065
- Upgrade Python versions in CI by @jopohl in #1074
Download & Tutorial

Demo
Universal Radio Hacker Copyright (C) 2017 Johannes Pohl and Andreas Noack
Source: https://github.com/jopohl/urh