ELECTRUM Cyber Breach Timeline | Image: Dragos
In the world of cybersecurity, the name ELECTRUM has become synonymous with precision, stealth, and disruption. This group, known for its meticulous cyber attacks on Ukrainian electric utilities, represents a new era of cyber warfare, where the lines between digital intrusion and real-world consequences are increasingly blurred. In a recent blog, the industrial cybersecurity company, Dragos delves into the workings of the ELECTRUM threat group, exploring their tactics, targets, and the implications of their actions.
ELECTRUM first caught the world’s attention with its involvement in a 2016 power outage that plunged a quarter of a million homes into darkness. This attack was not an isolated incident; it was part of a series of systematic cyber attacks targeting Ukraine’s electric utilities. These incidents have underscored the group’s capabilities and intentions, firmly establishing ELECTRUM as a significant threat in the cybersecurity landscape.

ELECTRUM’s approach is characterized by sophistication and patience. Their operations typically begin with gaining access to a network, followed by a period of dormancy. This allows them to conduct system reconnaissance and collect valuable information without raising suspicion. Once ready, they deploy custom scripts and tools to execute their planned attack.
One of their notable tools is a new version of CaddyWiper malware, used to erase their operational footprint from compromised IT systems, effectively covering their tracks and complicating forensic investigations.
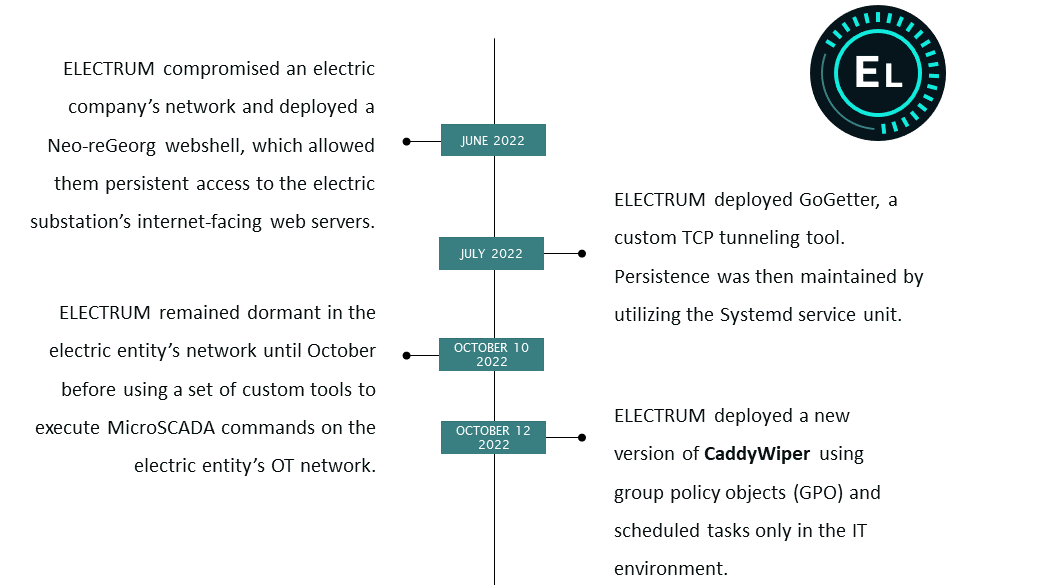
In 2022, the ELECTRUM threat group targeted a Ukrainian electric substation, gaining access through an end-of-life version of MicroSCADA software. This breach was part of a two-stage attack, beginning with access and reconnaissance, followed by disruption of the substation’s availability and control using custom living-off-the-land scripts. This incident demonstrated ELECTRUM’s ability to exploit vulnerabilities in operational technology environments and its persistence in pursuing strategic targets.
ELECTRUM’s activities have profound implications for the security of critical infrastructure worldwide. Their focus on electric utilities, a sector vital to any nation’s functioning, highlights the need for robust cybersecurity measures in operational technology environments. The use of native software like MicroSCADA in their attacks underscores the importance of securing even the most fundamental components of these systems.
To defend against threats like ELECTRUM, experts recommend a multi-faceted approach. This includes ensuring robust OT network monitoring, proactive threat hunting, and updating threat models to anticipate and mitigate potential cyber-attacks. The use of critical controls for OT cybersecurity, as identified by the SANS Institute, provides a solid framework for defending against adversary activities directed at ICS/OT systems.
ELECTRUM’s actions serve as a stark reminder of the evolving nature of cyber threats and the need for constant vigilance. Their targeted attacks on Ukraine’s electric utilities not only disrupt services but also signify a strategic move in cyber warfare. The shadow cast by ELECTRUM is a call to action for enhanced cybersecurity measures and international cooperation in the fight against such sophisticated adversaries.