Unmasking Sandman APT: SentinelLabs Decodes China’s Cyber Shadow
In the shadowy realm of cyber warfare, the Sandman APT group emerges as a formidable force. Associated with China-based threat clusters, Sandman exemplifies the escalating sophistication in global cyber espionage, particularly with its adoption of the Lua programming language, historically associated with Western cyber actors. SentinelLabs, Microsoft, and PwC threat intelligence researchers unravel the intricacies of Sandman’s operations and their broader implications.
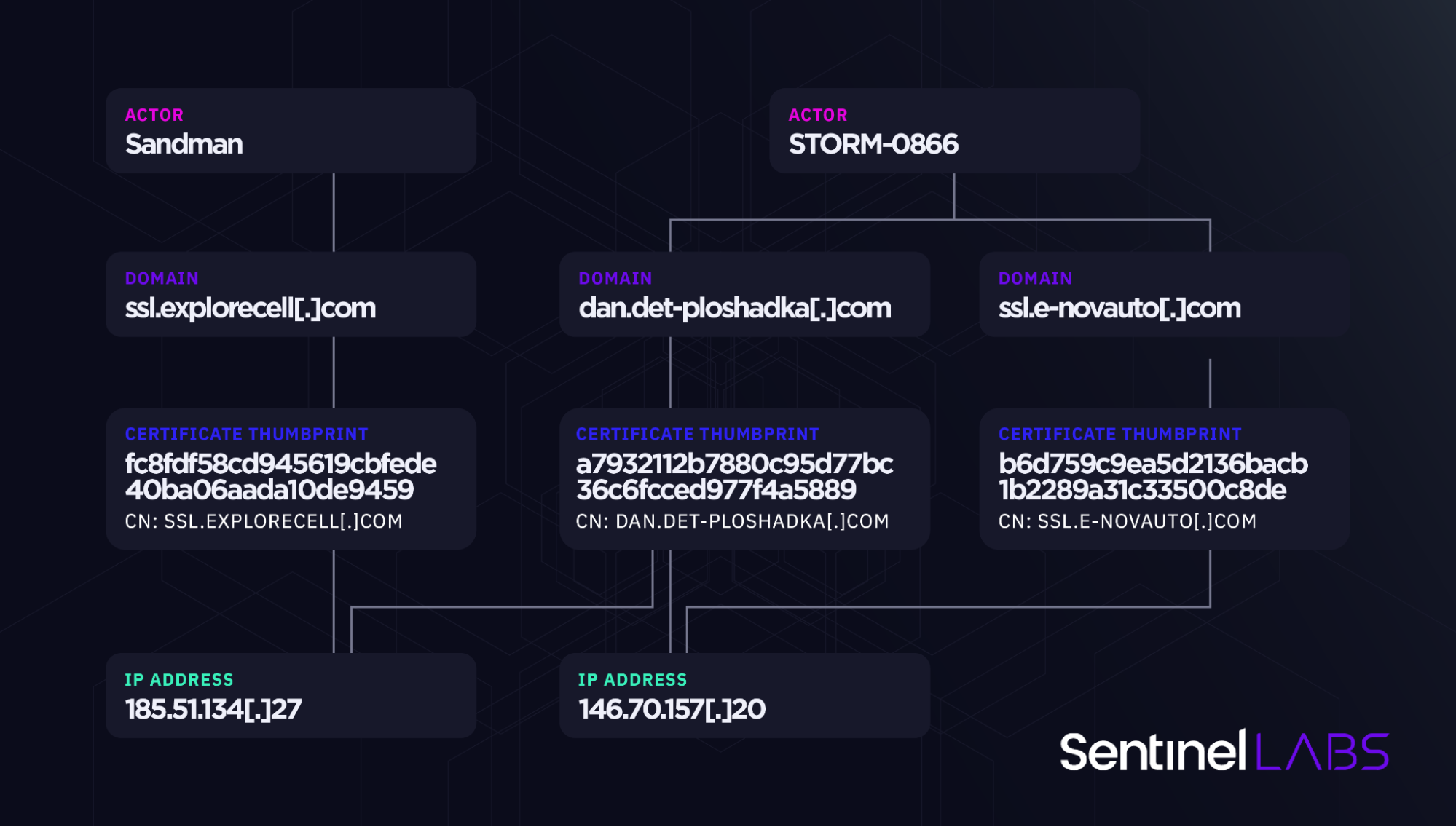
The Sandman APT, identified as likely being China-based, is intricately linked to known threat clusters, including STORM-0866/Red Dev 40. These groups share not only sophisticated malware tools like the KEYPLUG backdoor but also infrastructure control and domain naming conventions, painting a picture of coordinated cyber operations across multiple entities.

Infrastructure overview | Image: SentinelLabs
Sandman’s use of Lua-based malware, particularly LuaDream, alongside KEYPLUG in victim environments, marks a strategic shift in cyber espionage tactics. LuaDream’s modularity and the multifaceted nature of its deployment highlight Sandman’s advanced operational capabilities and adaptability.
Sandman’s activities predominantly target entities in the Middle East and the South Asian subcontinent, aligning with the operational focus of STORM-0866/Red Dev 40. This geographic focus underscores the strategic intent behind Sandman’s operations, impacting critical sectors like telecommunications and government entities.
Attributing Sandman’s activities to specific nation-state actors is challenging, given the shared infrastructure and development practices observed. This complexity is further compounded by the potential involvement of third-party vendors in supplying operational tools, making Sandman a distinct yet interconnected player in the broader Chinese threat landscape.
The emergence of the Sandman APT group is a significant development in the ever-evolving cyber threat arena. Their sophisticated use of Lua-based malware, targeting strategies, and operational coordination highlight the need for continuous vigilance and collaboration within the global cyber intelligence community.





