In the landscape of cybersecurity, the energy sector remains a critical area vulnerable to sophisticated cyberattacks. Forescout Vedere Labs’ recent threat briefing sheds light on two distinct cyberattacks targeting this sector in Denmark and Ukraine, attributing them to Sandworm, a Russian military threat actor renowned for its advanced persistent threats (APTs).
The report by Forescout Vedere Labs provides a comprehensive analysis of two separate attack waves on Denmark’s energy infrastructure. The initial findings by SektorCERT, Denmark’s CERT for critical infrastructure, indicated two distinct attacks. However, the Vedere Labs’ analysis suggests a different narrative.
The first wave exploited a vulnerability (CVE-2023-28771) in Zyxel firewalls before public exploits were available, indicating a potentially targeted and sophisticated attack. This wave compromised the industrial control systems of multiple Danish energy companies, forcing some into island mode (disconnecting from the energy grid for safety).

Contrarily, the second wave appears as part of a broader, less discriminatory campaign against unpatched firewalls, not specifically targeted by Sandworm. This wave’s tactics resembled a mass exploitation effort, with attackers leveraging a well-known CVE and changing staging servers periodically.
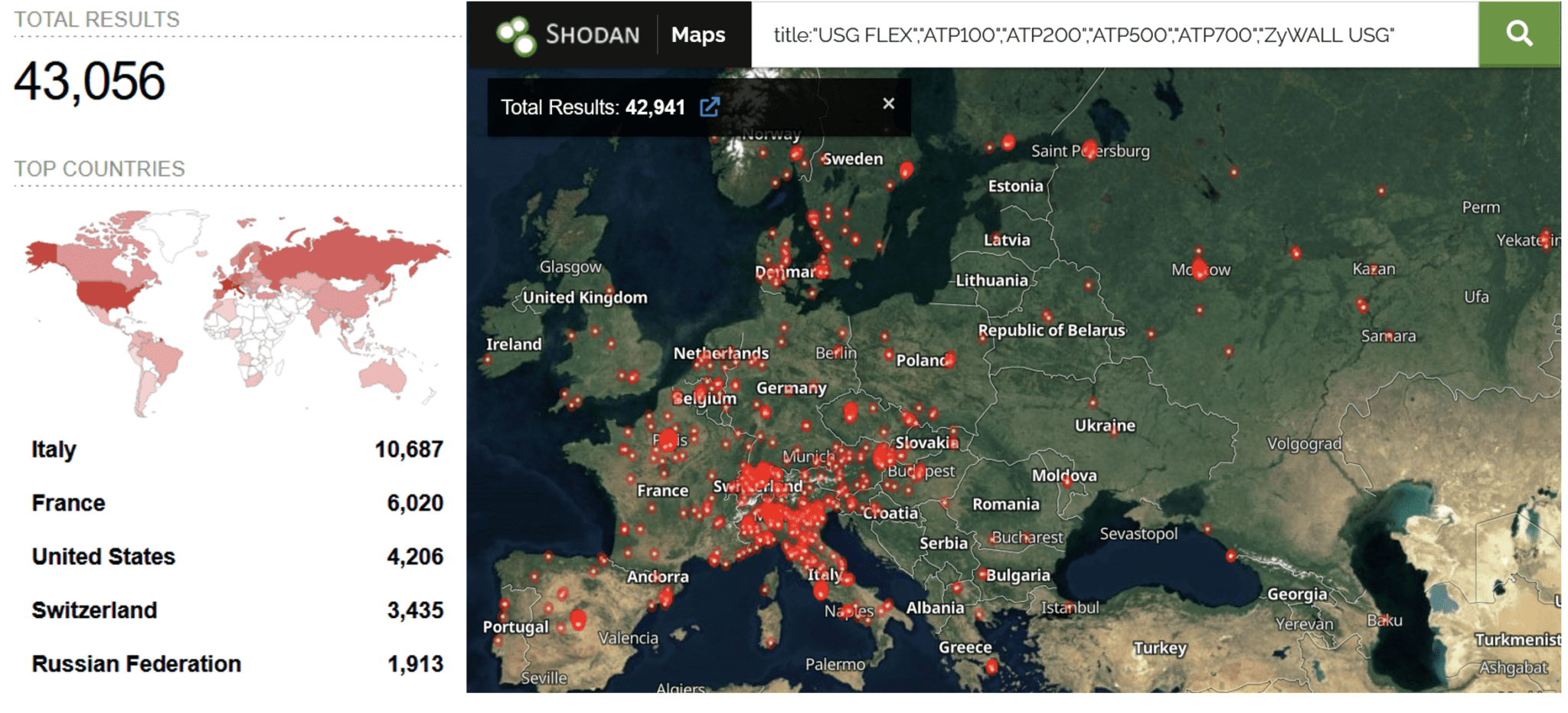
Forescout’s Adversary Engagement Environment (AEE) revealed that the exploitation of Zyxel vulnerabilities is not limited to Denmark. The indiscriminate nature of these attacks poses a significant risk to European critical infrastructure, with a substantial number of vulnerable Zyxel firewalls across the continent.
One notable aspect of these attacks is the use of ‘living off the land’ (LotL) techniques. While not necessarily faster than custom malware, LotL offers a stealth advantage, enabling attackers to avoid detection and leverage existing systems. This approach highlights the attackers’ evolving tactics and the need for robust defense mechanisms.
The Forescout Vedere Labs report emphasizes the importance of comprehensive network monitoring and rapid response in mitigating cyber threats. The distinction between state-sponsored and crimeware mass-exploitation campaigns often becomes clear only in retrospect, underscoring the need for detailed threat intelligence.
The analysis also underscores the vulnerability of perimeter security devices and the importance of additional monitoring. With over 43,000 exposed Zyxel firewalls in Europe, the report calls for heightened vigilance and robust security measures to protect critical infrastructure against these evolving cyber threats.