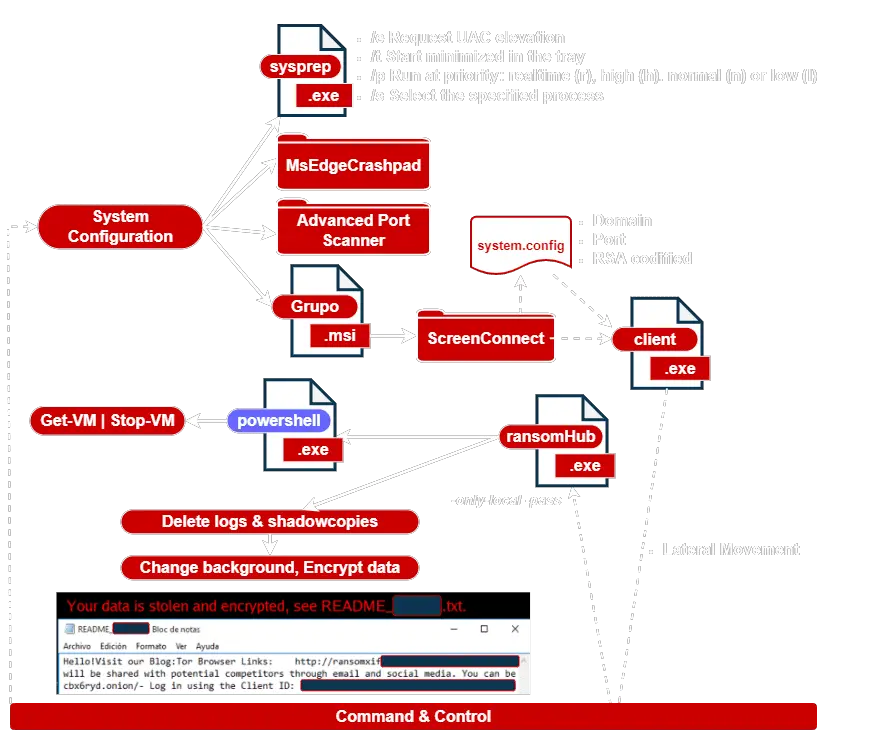
Infection chain – sample1.exe
Cybersecurity researchers at Lab52 have issued a warning about the RansomHub ransomware gang. This adaptable and sneaky group is using a combination of old and new tactics to breach systems, including Advanced Port Scanner and hidden PowerShell scripts. Their ransomware, obfuscated to hinder analysis, has been linked to the Knight ransomware, suggesting a larger network of cybercriminals at play.
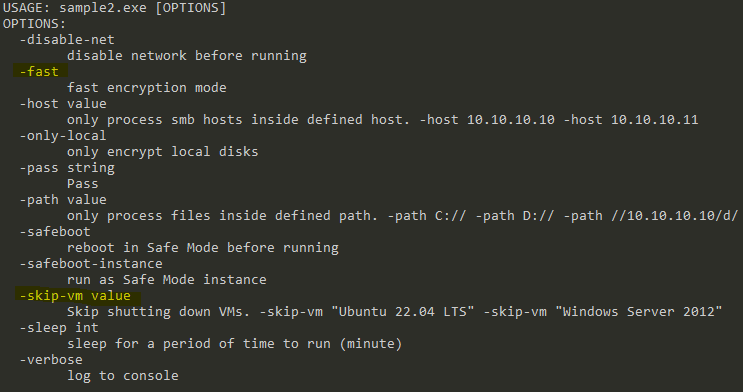
In a recent analysis, Lab52 examined two samples of RansomHub ransomware, revealing distinct characteristics and deployment methods. Sample1.exe, analyzed months ago, is known for its default behavior of shutting down virtual machines, a feature that cannot be disabled.
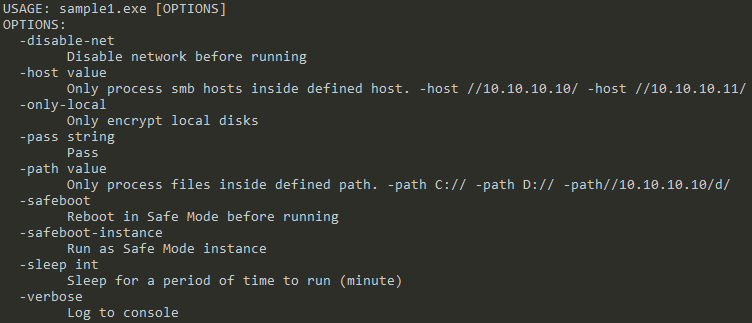
In contrast, Sample2.exe, observed in the field during June 2024, includes options for both virtual machine shutdown and “fast encryption mode,” offering more flexibility to the attackers.
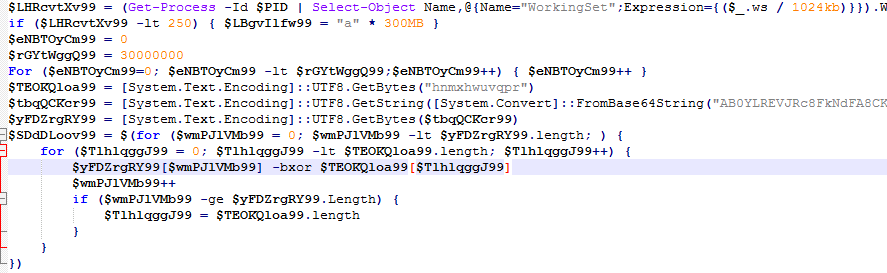
Both samples require a password for execution and employ sophisticated obfuscation methods to evade static analysis. Developed in Go, RansomHub utilizes the open-source obfuscator Garble, which complicates analysis by removing module names and replacing them with random strings. Tools like GoReSym and decryption scripts from OALabs can aid in deciphering some of the obfuscated data, though not all strings can be decrypted due to optimized functions.

The deployment tactics of RansomHub vary between samples. For sample1.exe, attackers used tools such as Advanced Port Scanner and ScreenConnect to identify devices for infection. In contrast, the deployment of sample2.exe involved obfuscated PowerShell scripts with execution delays, further complicating detection and analysis. These scripts can be successively deobfuscated until the dependent file, which changes names across different deployments, is revealed.
Emerging in 2024, RansomHub operates as a Ransomware-as-a-Service (RaaS) group, with its code linked to Knight ransomware, which was available on underground forums earlier this year. RansomHub gained notoriety when BlackCat affiliates, previously involved in an attack on Change Healthcare, targeted the organization again using RansomHub. This group has become a formidable alternative to other ransomware groups whose popularity has waned.
During June, RansomHub emerged as one of the most impactful ransomware groups globally. Public sources processed by Lab52 indicate a significant increase in the number of victims. The ransomware’s impact has been particularly pronounced in Latin America, where it ranked second among the most impactful ransomware groups in Q1 2024. In Europe, RansomHub reached the fourth position in June and recorded the highest number of known victims during that month.
For more detailed information on RansomHub’s infection chains and its global impact, refer to the full Lab52 report.
Related Posts:
- RansomHub: A New Ransomware-as-a-Service Threatens Multiple Operating Systems
- Ransomhub’s SCADA Hack: A Wake-Up Call for Industrial Cybersecurity
- Zerologon Vulnerability Strikes Again: RansomHub Exploits Legacy Flaw
- Popular Chinese Text Editors Compromised in Targeted Attack
- Defend Your Cloud: 8220 Gang Targets Linux & Windows