Update Beware! “Coyote” Trojan Uses Disguise to Infiltrate Brazilian Banks
Recently, researchers at Kaspersky Labs uncovered a new breed of banking Trojans dubbed “Coyote.” Unlike its predecessors, Coyote employs a cunning blend of cutting-edge technologies and innovative distribution tactics to infiltrate systems, primarily targeting users of over 60 banking institutions in Brazil.
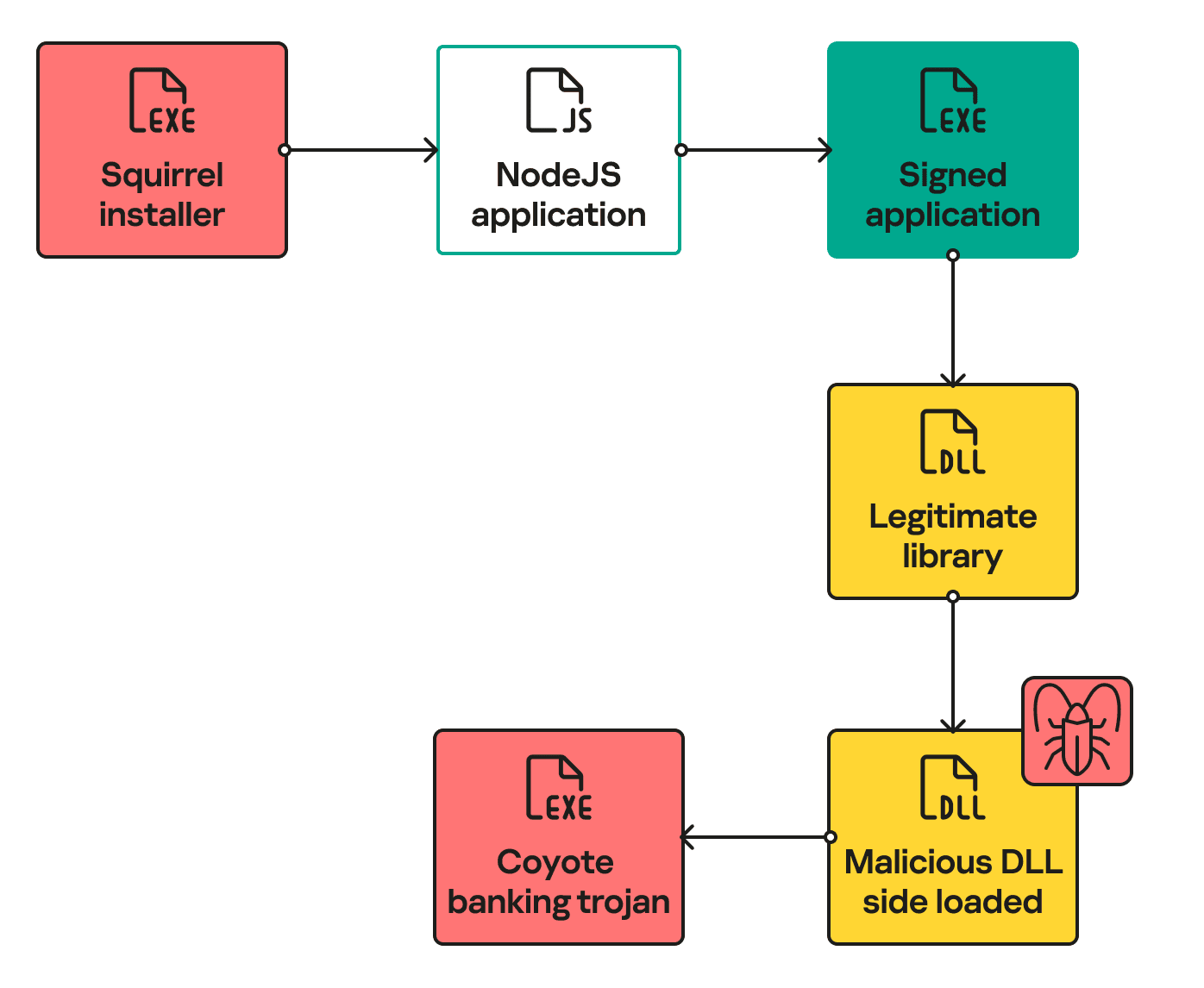
Traditionally, banking Trojans have relied on well-known methods like Delphi language and MSI installers for distribution. However, Coyote diverges from this norm by leveraging the Squirrel installer, NodeJS, and a relatively new multiplatform programming language called Nim. This unconventional approach allows Coyote to conceal its initial loader within what appears to be a benign update packager.

Coyote infection chain | Image: Kaspersky Labs
Upon execution, Coyote’s malicious Squirrel installer unpacks a NodeJS application compiled with Electron. This application, operating under the guise of legitimate processes like Chrome and OBS Studio, executes obfuscated JavaScript code to initiate the infection process. What sets Coyote apart is its utilization of DLL sideloading within the libcef.dll library, a technique employed for loading its banking malware component.
Adding to its complexity, Coyote employs Nim as a loader to unpack and execute a .NET executable in memory, akin to the functionality seen in Donut. This dynamic loading mechanism enhances the malware’s stealth and resilience, ensuring persistence through processes like obs-browser-page.exe, even after the system reboots.
Unlike its counterparts, Coyote refrains from extensive code obfuscation, opting instead for AES-encrypted string obfuscation. This technique involves generating a unique key for each executable and decrypting strings on-demand, enhancing the malware’s evasive capabilities.
Coyote achieves persistence by manipulating Windows logon scripts, enabling it to monitor user activity and intercept sensitive banking information. With a keen focus on Brazilian banking applications, Coyote meticulously tracks over 60 targeted applications, sending collected data to its command and control (C2) server via SSL channels.
At the heart of Coyote’s operation lies its C2 communication infrastructure, which utilizes SSL channels with mutual authentication. Upon establishing contact with the C2 server, Coyote transmits vital information such as machine details, randomly generated GUIDs, and the active banking application. In return, the server issues commands ranging from keylogging and taking screenshots to creating phishing overlays to harvest user credentials.
Coyote represents a paradigm shift in the realm of Brazilian banking Trojans, embracing modern technologies like Node.js, .NET, and advanced packaging techniques. The inclusion of Nim as a loader underscores the malware’s sophistication, highlighting the adaptability of threat actors in leveraging the latest languages and tools for nefarious purposes.





