vault_scanner: swiss army knife for hackers
VAULT
Swiss army knife for hackers

Features
-
Scan website for the following vulnerabilities
- XSS
- LFI
- RFI
- SQLi
-
Scanner
- Port scanning : ACK, FIN, NULL, XMAS
- IP scanning : Ping Sweep, ARP
- SSL vulnerability scan
- OS scan
- Hash scanner : MD5, SHA1, SHA224, SHA256, SHA512
-
Others
- Information Gathering
- Clickjacking
- jQuery version checking
- Insecure cookie flags
- Testing HTTP methods
- Insecure headers
- Header/banner grabbing
- Finder
- Find comments in source code
- Find e-mails in source code
- Session fixation through cookie injection
- Brute force login through authorization headers
- URL Fuzzer
- WHOIS Lookup
- Google Dork
- Error handler checker
- Admin panel finder
- Open redirect vulnerability
- CMS Detection
- Detect Honeypots
- Detect DDoS attack
- Detect De-authentication attack
- Detect ARP spoof attack
-
Crawling
- Crawl a website and collect all the links
- Crawl and scrape the website for images
-
Attacks
- DDoS Attack
- ARP Spoofer
- DNS Spoofer
- De-authentication attack
- Network disassociation attack
- Ping of death
- MAC Flood attack
-
Utilities
- Generate customized backdoor
- Data monitoring
- Keylogger
- SSH Tunelling
- Generate sitemap
- MAC address changer
- Trace route
Install
git clone https://github.com/abhisharma404/vault_scanner.git
cd vault_scanner
sudo apt-get install python3-pip
sudo pip3 install virtualenv
virtualenv venv
source venv/bin/activate
pip3 install -r requirements.txt
Starting Vault :cd vault_scanner/src
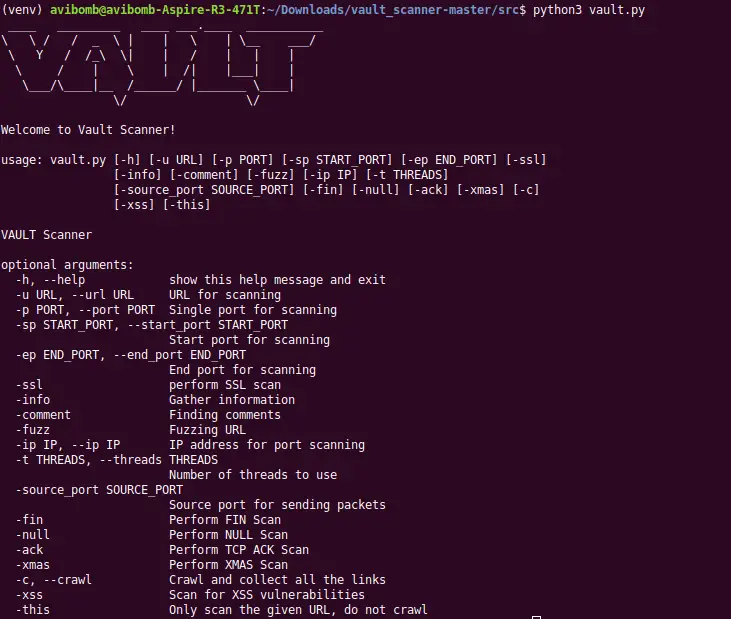
python3 vault.py
Usage
Copyright (c) [2018] [Abhishek Sharma]





