Attack flow
A recently uncovered phishing campaign demonstrates a concerning level of sophistication in its efforts to infiltrate systems and deploy an array of powerful Remote Access Trojans (RATs). Security researchers at FortiGuard Labs have discovered that attackers are using trusted public cloud platforms, like Amazon Web Services (AWS) and GitHub, to store their malicious payloads, ultimately compromising the security of target systems.
Email Lure and Obfuscation Tactics

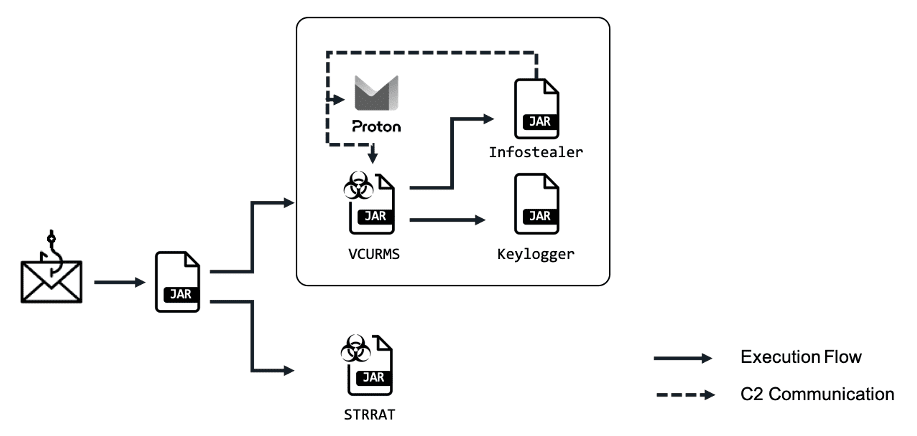
The campaign’s initial point of entry is through meticulously crafted phishing emails, often mimicking official business communications or notifications of pending payments. These deceptive emails aim to lure unsuspecting victims into clicking on embedded buttons or links, which triggers the download of a harmful Java Archive (JAR) file. This file might masquerade as an ordinary document, further obscuring its malicious nature.
The JAR file is where the attack truly intensifies. To hinder analysis and bypass security solutions, the code within the file is heavily obfuscated using a commercially available protector. Once executed, it serves as a springboard for further infections. It reaches out to download and install additional payloads, including both well-known and newly discovered threats.
Introducing VCURMS: A New Threat
One of the most concerning discoveries in this campaign is the deployment of a new Java-based RAT named VCURMS. This RAT possesses an unusual method of communication, relying on email protocols to interact with its command and control (C2) server. The attacker uses Proton Mail, a privacy-focused email service, further shielding their operations from potential surveillance.
Payload Delivery and Data Theft
The attackers don’t stop at VCURMS RAT. The campaign also includes STRRAT, a potent RAT with a history of malicious exploits. Alongside these RATs, password-stealing malware and a sophisticated keylogger are installed. This allows the attackers to capture keystrokes, potentially exposing highly sensitive login credentials and other confidential information. Interestingly, VCURMS appears to borrow components from Rude Stealer, an infamous infostealer, suggesting that the attackers are continuously refining their tools and techniques.
The Evolving Threat Landscape
This phishing campaign underscores the adaptability of cybercriminals who are constantly refining their techniques. Their use of trusted cloud platforms and commercial obfuscation tools demonstrates their determination to remain undetected. Organizations and individuals alike must consistently update their security strategies to stay ahead of these evolving threats.