Venom v1.1.0 releases: A Multi-hop Proxy for Penetration Testers
Venom – A Multi-hop Proxy for Penetration Testers
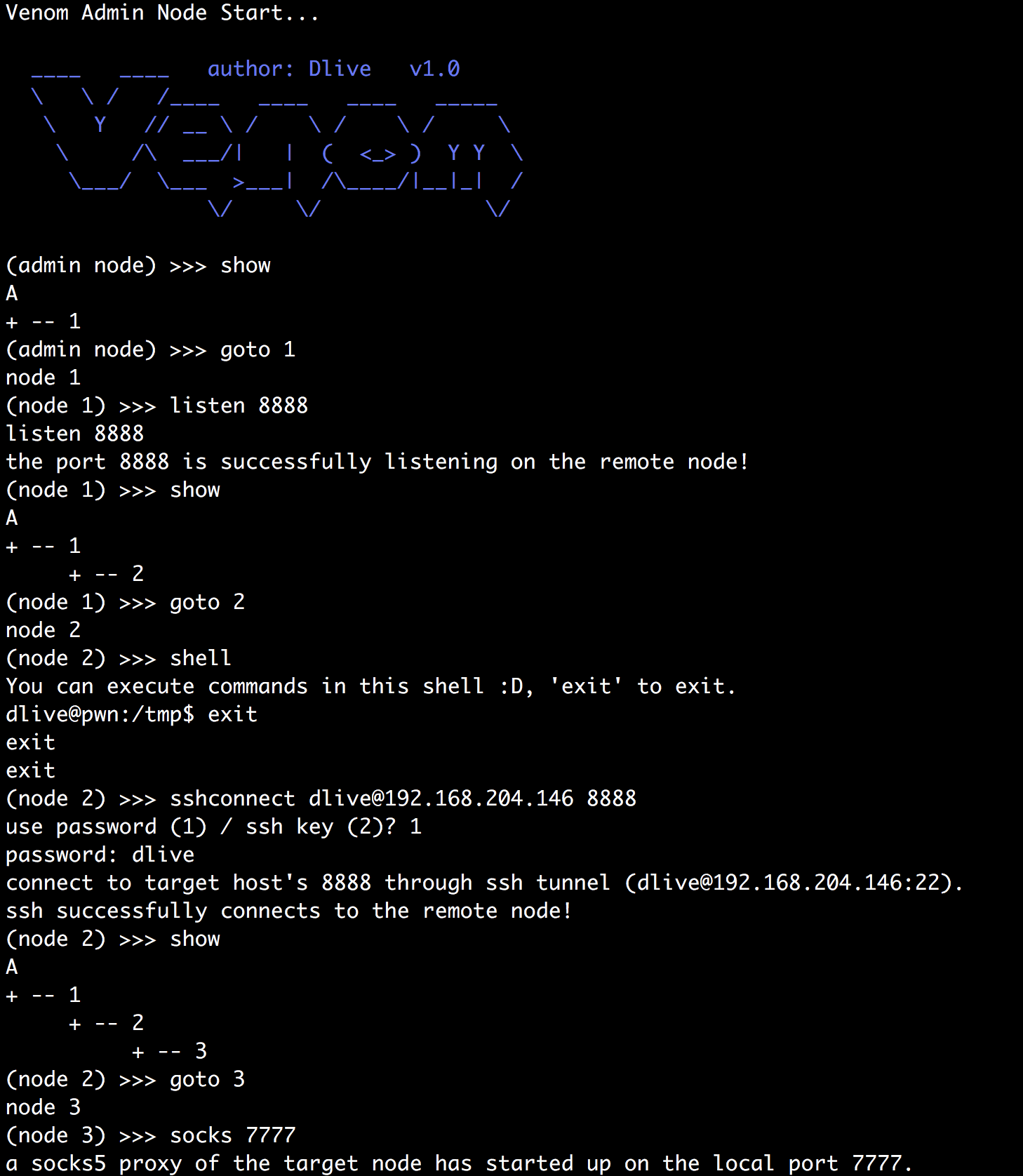
Venom is a multi-hop proxy tool developed for penetration testers using Go.
You can use venom to easily proxy network traffic to a multi-layer intranet and easily manage intranet nodes.

Features
- network topology
- multi-hop socks5 proxy
- multi-hop port forward
- port reuse (apache/mysql/…)
- ssh tunnel
- interactive shell
- upload and download file
- network traffic encryption
- supports multiple platforms(Linux/Windows/MacOS) and multiple architectures(x86/x64/arm/mips)
Since the IoT device (arm/mips/… architecture) usually has limited resources, in order to reduce the size of the binary file, the binaries for the IoT environment do not support port reuse and ssh tunnel, and in order to reduce memory usage, the binaries only support less network concurrency and smaller buffers.
Changelog v1.1.0
- Added a new feature: network traffic encryption (the
-passwdoption). - Fixed a bug in the admin node’s shell command (issue #3).
Tutorial
Copyright (c) 2010-2018 Google, Inc. http://angularjs.org





