Vibe v3.0 releases: A framework for stealthy domain reconnaissance
by do son · Published · Updated
Vibe
Vibe is a tool designed to perform post-ex lateral movement techniques while remaining undetected by network detection tools including Threat Hunting appliances. It works by pulling down all information about a domain, allowing users to perform the same domain net commands offline. It also enumerates additional information that is not typically shown in these queries. It also provides the ability to scan systems to see what shares are available and what privileges the account used, has access to. Vibe also provides the ability to enumerate user’s currently logged into systems, as well as, who has been logged in while remaining undetected.

Changelog v3.0
- Python 3 support
- Optional password prompt on launch
- SPN collector
Installation
sudo apt-get install libsasl2-dev python3-dev libldap2-dev libssl-dev
git clone https://github.com/Tylous/Vibe.git
pip install -r requirements.txt
Usage
./vibe.py -h
usage: vibe.py [-h] -U username -P password -D domain -I IP [-o]
optional arguments:
-h, --help show this help message and exit
-U username, --Username username
Username
-P password, --Password password
Password
-D domain, --Domain domain
Fully Qualified Domain Name
-I IP, --IP IP IP address of Domain Controller
-o, --Offline Offline Mode
-r, --Remove Remove Database
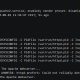
root@kali:~/# ./vibe.py -U admin -P Password! -D STARLABS.local -I 172.16.144.185
___ ___ ___ ________ _______
|\ \ / /||\ \ |\ __ \ |\ ____\
\ \ \ / / /\ \ \ \ \ \|\ /_ \ \ \_____
\ \ \/ / / \ \ \ \ \ __ \ \ \ ____\
\ \ / / \ \ \ \ \ \|\ \ \ \ \____
\ \__/ / \ \__\ \ \_______\ \ \______\
\|__|/ \|__| \|_______| \|______|
(@Tyl0us)
[+] Creating DB
[+] Credentials Valid, Generating Database
[+] Sucessful Database Created
0.434292078018
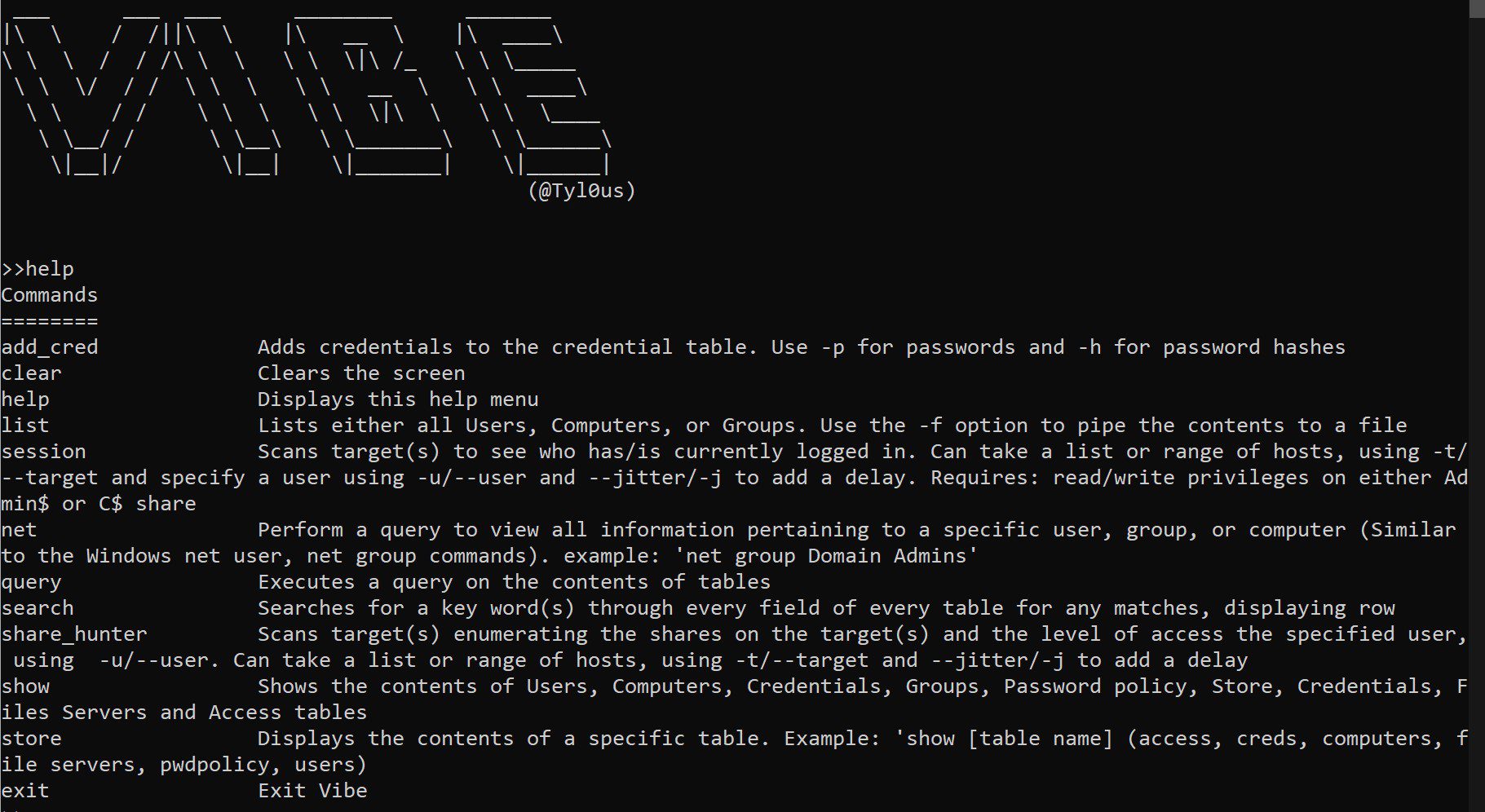
>>help
Commands
========
add_cred Adds credentials to the credential table. Use -p for passwords and -h for password hashes
clear Clears the screen
help Displays this help menu
list Lists either all users, computers, or groups. Use the -f option to pipe the contents to a file
session Scans target(s) to see who has/is currently logged in. Can take a list or range of hosts, using -t/--target and specify a user using -u/--user and --jitter/-j to add a delay. Requires: read/write privileges on either Admin$ or C$ share
net Perform a query to view all information pertaining to a specific user, group, or computer (Similar to the Windows net user, net group commands). example: 'net group Domain Admins'
query Executes a query on the contents of tables
search Searches for a key word(s) through every field of every table for any matches, displaying row
share_hunter Scans target(s) enumerating the shares on the target(s) and the level of access the specified user, using -u/--user. Can take a list or range of hosts, using -t/--target and --jitter/-j to add a delay
show Shows the contents of Computers, Credentials, Groups, Password policy, Store, Credentials, Files Servers and Access tables
store Displays the contents of a specific table. Example: 'show [table name] (access, creds, computers, file servers, pwdpolicy, users)
exit Exit Vibe
>>
Domain Information Querying
The show command displays the contents of a table, specific information across all tables or the available modules, using the following syntax:
>>show users
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| Username | Home Directory | SID | Password Last Set | Last Logged On | Account Settings | Member Of |
+================+========================+=======+=====================+=====================+====================+========================================+
| Administrator | | 500 | 2017-11-28 16:40:56 | 2017-11-28 16:35:48 | DONT_EXPIRE_PASSWD | Domain Users |
| | | | | | NORMAL_ACCOUNT | WseInvisibleToDashboard |
| | | | | | ACCOUNT_DISABLED | Group Policy Creator Owners |
| | | | | | | Domain Admins |
| | | | | | | Enterprise Admins |
| | | | | | | Schema Admins |
| | | | | | | Administrators |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| Guest | | 501 | 1600-12-31 19:03:58 | 1600-12-31 19:03:58 | DONT_EXPIRE_PASSWD | Domain Guests |
| | | | | | PASSWD_NOTREQD | Guests |
| | | | | | NORMAL_ACCOUNT | |
| | | | | | ACCOUNT_DISABLED | |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| DefaultAccount | | 503 | 1600-12-31 19:03:58 | 1600-12-31 19:03:58 | DONT_EXPIRE_PASSWD | Domain Users |
| | | | | | PASSWD_NOTREQD | System Managed Accounts Group |
| | | | | | NORMAL_ACCOUNT | |
| | | | | | ACCOUNT_DISABLED | |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| Admin | | 1000 | 2017-11-28 16:40:24 | 2018-08-24 13:01:20 | DONT_EXPIRE_PASSWD | Domain Users |
| | | | | | NORMAL_ACCOUNT | Domain Admins |
| | | | | | | Administrators |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| krbtgt | | 502 | 2017-11-28 16:44:43 | 1600-12-31 19:03:58 | NORMAL_ACCOUNT | Domain Users |
| | | | | | ACCOUNT_DISABLED | Denied RODC Password Replication Group |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| ballen | \\\\SLServer01\\ballen | 1123 | 2017-11-28 17:40:08 | 2018-08-09 17:56:50 | DONT_EXPIRE_PASSWD | Domain Users |
| | | | | | NORMAL_ACCOUNT | SL_R&D |
| | | | | | | SL_Scientist |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| cramon | \\\\SLFS02\\cramon | 1125 | 2018-05-29 13:07:32 | 2018-08-23 21:47:26 | NORMAL_ACCOUNT | Domain Users |
| | | | | | | SL_R&D |
| | | | | | | SL_HelpDesk |
| | | | | | | Domain Admins |
| | | | | | | Enterprise Admins |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| hwells | | 1126 | 2017-11-28 17:51:51 | 2018-08-23 21:46:21 | DONT_EXPIRE_PASSWD | Domain Users |
| | | | | | NORMAL_ACCOUNT | SLServ01_Admin |
| | | | | | | SL_R&D |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| ssmith | | 2104 | 2018-08-09 20:54:14 | 2018-08-09 20:47:47 | NORMAL_ACCOUNT | Domain Users |
| | | | | | | SL_HR |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| csnow | \\\\SLFS01\\csnow | 2105 | 2018-08-09 19:35:05 | 2018-08-23 20:53:35 | NORMAL_ACCOUNT | Domain Users |
| | | | | | | SL_R&D |
| | | | | | | SL_Scientist |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| wwest | | 2608 | 2018-08-09 20:58:39 | 1600-12-31 19:03:58 | NORMAL_ACCOUNT | Domain Users |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
| iwallen | | 2610 | 2018-05-16 22:49:37 | 1600-12-31 19:03:58 | NORMAL_ACCOUNT | Domain Users |
+----------------+------------------------+-------+---------------------+---------------------+--------------------+----------------------------------------+
There are several different options that can be used with the show command including:
- access
- computers
- creds
- fgpolicy (only accessible if an account that has admin access to the domain contoller is used, on inital start up)
- file servers
- groups
- pwdpolicy
- store
- users
More…
Copyright (c) 2018 Tylous
Source: https://github.com/Tylous/