Virtual Hard Drives: The New Bypass for Secure Email Gateways and Antivirus Scanners

In a recent report by Kahng An, part of the Cofense Intelligence Team, a critical vulnerability in the detection capabilities of Secure Email Gateways (SEGs) and antivirus (AV) scanners was revealed. Cybercriminals increasingly use Virtual Hard Drive (VHD) files to evade detection and deliver malicious payloads. The report reveals how threat actors embed malware within VHD and VHDX files, sending them as email attachments or providing download links, bypassing security defenses.
The report details that virtual hard drive files (.vhd and .vhdx) are typically used for virtual machines. However, they can also be mounted in Windows as if they were physical volumes, allowing attackers to disguise malware within these files. Kahng An’s research emphasizes that many SEGs and AV scanners struggle to detect malicious content embedded within these virtual drives.
The report states, “The threat actors send emails with .zip archive attachments containing virtual hard drive files or embedded links to downloads that contain a virtual hard drive file that can be mounted and browsed through by a victim.” Once mounted, the victim is tricked into executing a malicious payload. Even more concerning is the fact that in older versions of Windows, these VHD files can be configured to automatically execute the malware using AutoRun functionality.
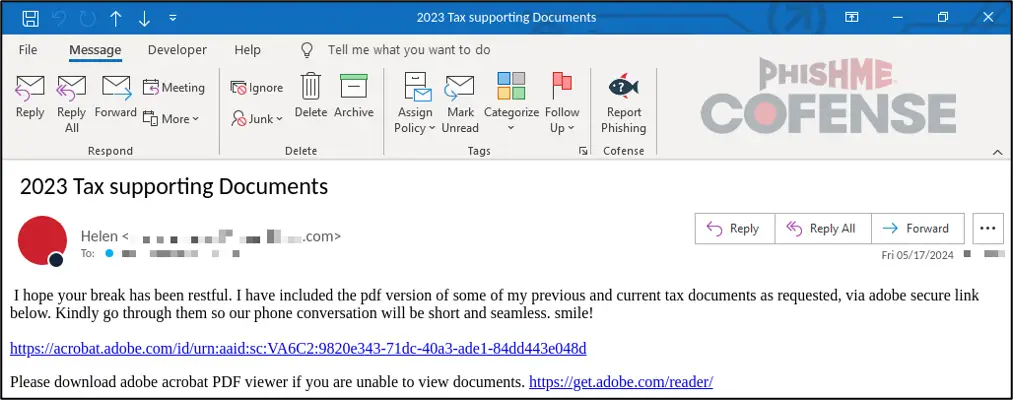
Sample email for a tax-themed campaign from May 2024 that utilized legitimate embedded URLs to bypass SEGs | Image: Cofense
Throughout 2024, various email campaigns have exploited this technique. The Cofense Intelligence Team’s report identifies campaigns delivering Remote Access Trojans (RATs), including Remcos RAT and XWorm RAT. These campaigns use themes such as tax returns, shipping updates, and job applications, each tailored to deceive unsuspecting recipients.
For example, a tax-themed campaign in May 2024 used embedded links to download a VHD file named “Tax_Organizer.exe,” which delivered Remcos RAT by loading a malicious DLL. Similarly, a shipping-themed campaign in June and July spoofed Canada Post and postal services, attaching .zip archives containing VHD files disguised as package labels. In these instances, unsuspecting users would open files like “package_photo.lnk,” which executed a Visual Basic script that delivered XWorm RAT.
One of the most alarming aspects of the report is the effectiveness with which these virtual hard drive files bypass SEGs. Threat actors can easily evade detection by embedding malicious VHD files in email attachments or links. The report highlights specific examples where major SEGs, including Cisco Secure Email Gateway, Proofpoint Messaging Security Gateway, and FireEye Email Security, failed to detect these threats. In the case of the tax-themed campaign, Cisco’s ThreatScanner and AMP components provided false-negative results despite the embedded malicious files.
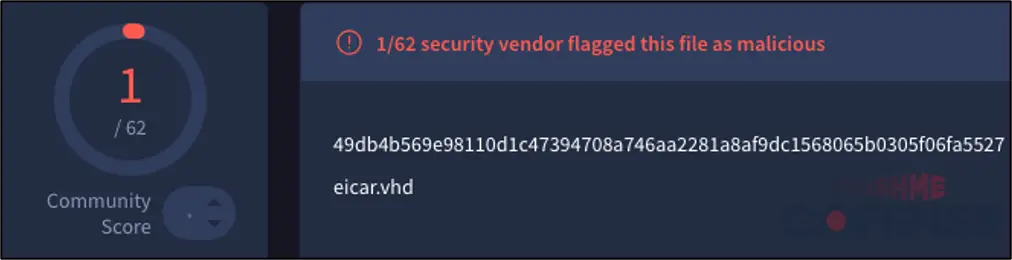
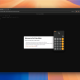
1 out of 62 detections on VirusTotal for an EICAR test file within a .vhd file | Image: Cofense
Beyond SEGs, the report also explores the challenges antivirus scanners face when analyzing VHD files. According to An’s findings, “antivirus solutions struggle to detect malicious content within the hard drive images.” Tests conducted using the EICAR test file demonstrated that while standalone files were detected by almost all antivirus programs, the same files embedded within a VHD or VHDX file were flagged by only a few. This presents a significant vulnerability, as even well-known malware can go undetected when hidden within a VHD.
Threat actors are also taking advantage of the malleable nature of virtual hard drive files, making them even harder to detect. By modifying the file hash, either by changing the amount of allocated storage space or the file format (e.g., from .vhd to .vhdx), attackers can avoid detection by antivirus solutions relying on static hash-based identification. The report points out that this flexibility enables attackers to manipulate VHD files and reduce the likelihood of detection by scanning systems.