Image: Pen Test Partners
Security researchers have disclosed two critical vulnerabilities in Proroute H685t-w 4G routers that could allow remote attackers to compromise affected devices, potentially leading to unauthorized access, data breaches, and disruption of network services.
CVE-2024-45682 (CVSS 8.8): Command Injection Vulnerability Enables Complete System Takeover
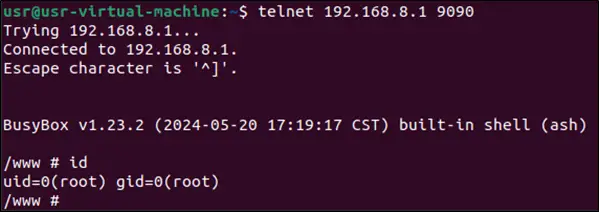
The most severe of the two flaws, tracked as CVE-2024-45682, is an authenticated command injection vulnerability that allows an attacker to execute arbitrary code on the underlying operating system. This vulnerability could be exploited by any user with access to the router’s web interface, even with limited privileges. The attacker could gain full control of the device, enabling actions like installing malware, exfiltrating sensitive information, or launching further attacks on the connected network.
CVE-2024-38380 (CVSS 5.5): Cross-Site Scripting Vulnerability Facilitates Account Hijacking
The second vulnerability, identified as CVE-2024-38380, is a reflected cross-site scripting (XSS) flaw that could allow an attacker to inject malicious scripts into web pages viewed by users of the affected router. This vulnerability could be exploited to steal session cookies, hijack user accounts, or launch phishing attacks.
Researcher Discovers Flaws, Vendor Releases Patch
Joe Lovett, a security researcher at Pen Test Partners, discovered the vulnerabilities and responsibly disclosed them to CISA. The vendor has responded by releasing firmware version 3.2.335, which addresses both flaws. Proroute urges all users of the H685t-w 4G router to update their devices to the latest firmware version as soon as possible.
Users Urged to Take Immediate Action
The severity of these vulnerabilities underscores the importance of timely patching. Users of Proroute H685t-w 4G routers are strongly advised to update their devices to firmware version 3.2.335 or later without delay. Delaying patching could leave networks exposed to significant risk.
Related Posts:
- Researchers found 4G LTE flaws that can steal user information, location and issue false warnings
- Thailand’s largest 4G mobile operator TrueMove H encounters AWS S3 bucket data leakage