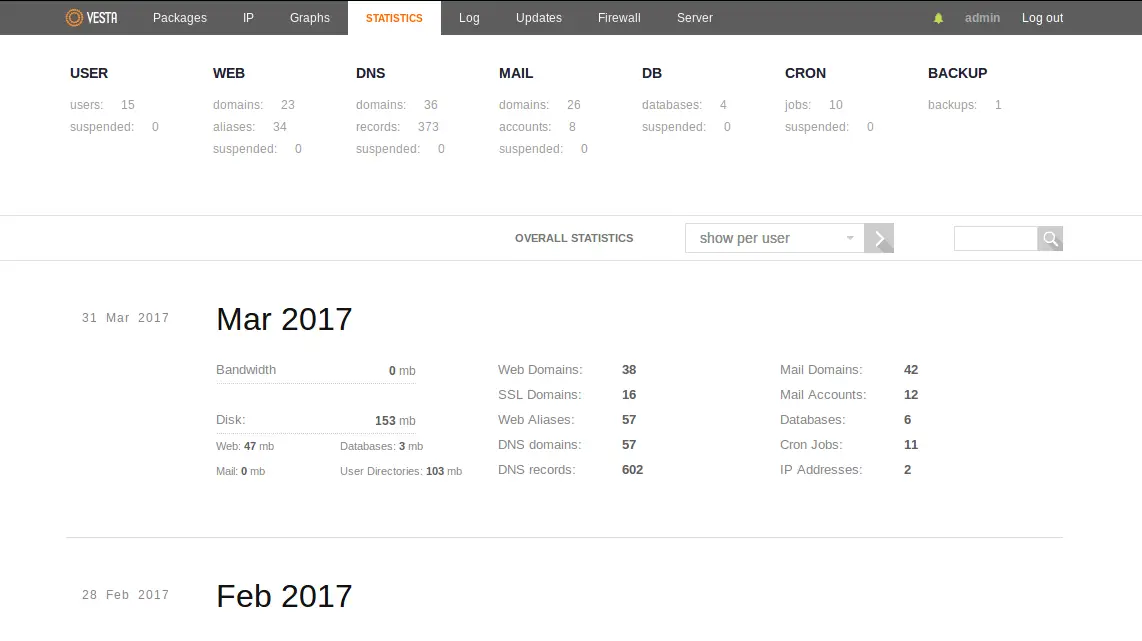
A recent analysis by Adrian Tiron, a Cloud Application Security Consultant at Fortbridge, has uncovered a critical vulnerability in the Vesta Control Panel—a popular web-based interface for managing Linux servers. The vulnerability allows attackers to take over the admin account by exploiting reduced seed entropy in Bash’s $RANDOM variable.
Vesta is known for its simplicity, allowing users to easily manage hosting, domains, and databases. However, like many systems that prioritize usability, security can sometimes take a back seat. In this case, Vesta’s password reset function, a core feature, relies on bash scripts that generate tokens using $RANDOM. The problem lies in the fact that $RANDOM is not cryptographically secure, and the seed it uses can be guessed through brute force.
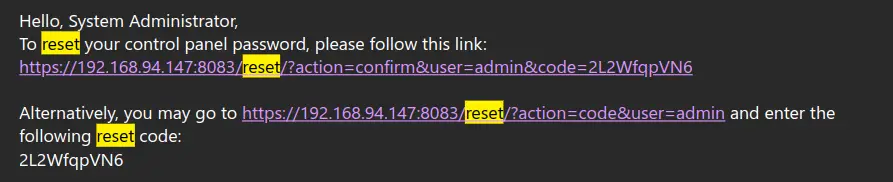
When a password reset is requested in Vesta, a token is generated using the bash $RANDOM variable, which is then sent to the user via email. This token is also stored in the user’s configuration file and is crucial to resetting the password. The $RANDOM variable generates a pseudo-random integer between 0 and 32,767, which, while appearing random, can be predicted with the right tools.
Tiron’s research leveraged a tool called BashRandomCracker, a project that can reverse-engineer the seed used by $RANDOM given a few samples. By providing three $RANDOM values, the tool can predict future values, including those that generate password reset tokens.
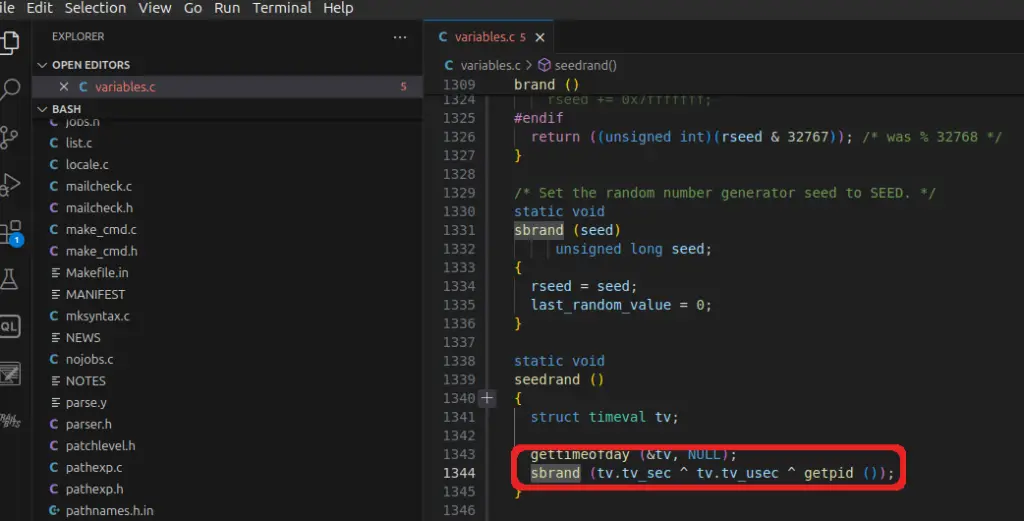
The vulnerability stems from the way Bash seeds its random number generator. The sbrand() function, which sets the seed, relies on the current timestamp (tv_sec), microseconds (tv_usec), and process ID (getpid()). However, this function only modifies the lower 20 bits of the timestamp, drastically reducing entropy. This means that an attacker can focus their brute force efforts within a much smaller range, centered around the last password reset timestamp.
An attacker can exploit this reduced entropy by:
- Calculating the Timestamp Range: Since only the lower 20 bits of the timestamp affect the seed, the attacker can calculate a range of timestamps within which the seed likely falls—typically around 12 days before and after the current timestamp.
- Brute-Forcing the Seed: By iterating through this range and generating potential reset tokens, the attacker can compare them against the reset token format and find a match.
- Resetting the Admin Password: Once the correct reset token is found, the attacker can use it to reset the admin password and gain full control over the Vesta Control Panel.
Adrian Tiron developed a proof-of-concept exploit using an extended version of bashrand to demonstrate the feasibility of this attack. By focusing on a narrowed timestamp range (e.g., the last year), the number of brute-force attempts is reduced from over 4 billion to around 31 million—a significant optimization that makes the attack practical.
Furthermore, tools like Turbo Intruder can automate the process of sending HTTP requests with different reset tokens, speeding up the exploitation process.
Related Posts:
- HTTP/2 Rapid Reset Attack: HTTP/2 Zero-Day Vulnerability Rocks Cybersecurity World
- Microsoft Signals End of an Era: Control Panel to be Phased Out