Direct attacker scanning
According to a comprehensive report by Palo Alto Networks, the cybersecurity realm is witnessing a significant uptick in malware-initiated scanning attacks. This method, diverging from traditional direct scanning approaches, involves the use of infected hosts to scan and exploit vulnerabilities in other systems. The strategic shift enables attackers to not only mask their tracks more effectively but also to bypass geofencing restrictions, expand their botnet armies, and exploit the resources of compromised devices for extensive scanning operations.
Malware-initiated scanning represents a cunning evolution in cyberattack methodologies. Threat actors deploy malware to hijack legitimate systems, turning them into unwilling participants in the scanning of networks for vulnerabilities. This method offers several strategic advantages, including obscuring the attackers’ origins, leveraging the computational resources of infected hosts, and bypassing defensive measures designed to block scans from known malicious sources.
The report highlights several key indicators of malicious scanning activity, such as an unusually high volume of scanning requests, which can signal the presence of malware on a network. By correlating these characteristics with known malware signatures, cybersecurity researchers can detect both known and emerging threats.

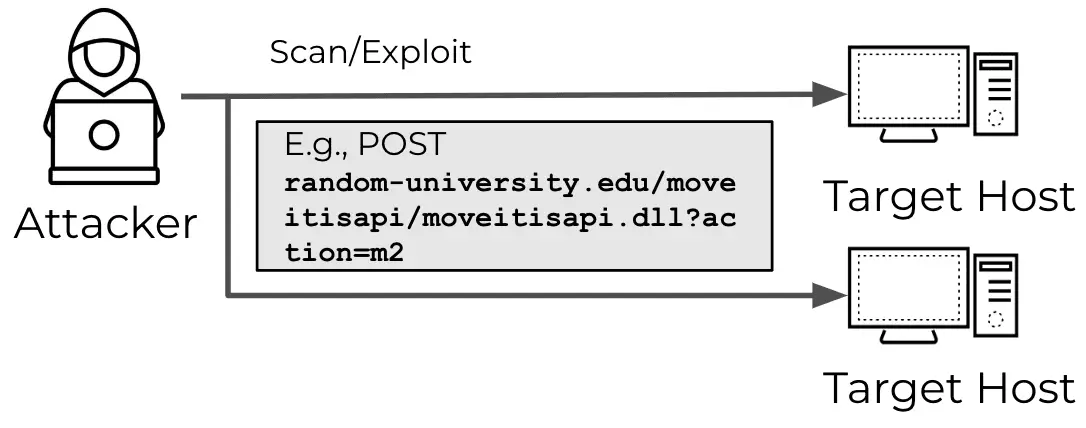
An illustrative example provided involves a hypothetical attack on “random-university.edu,” where an attacker uses an HTTP POST request to exploit a known vulnerability, CVE-2023-34362. Without adequate protection, such an attack could easily breach the target’s defenses.
Palo Alto Networks’ telemetry data sheds light on the growing complexity and volume of scanning attacks. For instance, URLs related to the MOVEit vulnerability CVE-2023-34362 were requested over 7,000 times by more than 1,400 devices in 2023 alone. This pattern underscores the attackers’ penchant for exploiting newly disclosed vulnerabilities, often before defenses can be adequately fortified.
The Mirai botnet, infamous for its disruptive power, serves as a case study in the report. Mirai variants have been observed exploiting vulnerabilities in Zyxel routers and other devices, using them as springboards to scan for and infect additional targets. This not only perpetuates the botnet’s spread but also underscores the critical importance of patching vulnerabilities promptly to disrupt such chains of infection.
Another focal point of the report is the spike in scanning activity targeting recently disclosed Ivanti vulnerabilities. Within days of their disclosure, tens of thousands of hosts were scanned, exploiting high-severity flaws for authentication bypass, command injection, and server-side request forgery. This rapid mobilization of threat actors highlights the urgent need for constant vigilance and swift response to vulnerability disclosures.
This report offers a stark reminder of the evolving threat landscape. While not every scan is malicious, increased vigilance and proactive security measures are crucial. Staying informed of the latest vulnerabilities and security best practices will help individuals and organizations stay ahead in the fight against cyber threats.