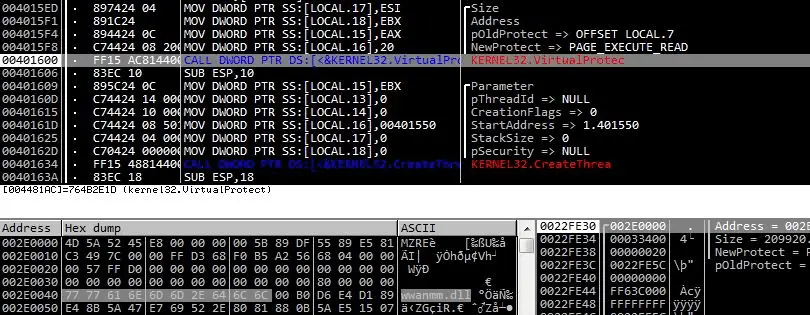
Shellcode and strings used for wwanmm.dll
Threat analysts have observed that hackers are installing Cobalt Strike beacons in vulnerable Microsoft SQL Server to inject malware in targeted networks.
This new attack pattern was first discovered by ASEC researchers at comprehensive cybersecurity provider Ahn Lab. Hackers deploy Cobalt Strike beacons on vulnerable Microsoft SQL servers to gain initial access to target networks and deploy malicious payloads. The vulnerable Microsoft SQL Server was the primary target of hackers.
Once the attack chain starts, the attacker scans the MS-SQL server with TCP port 1433 and then performs brute force and dictionary attacks in an attempt to crack the password.
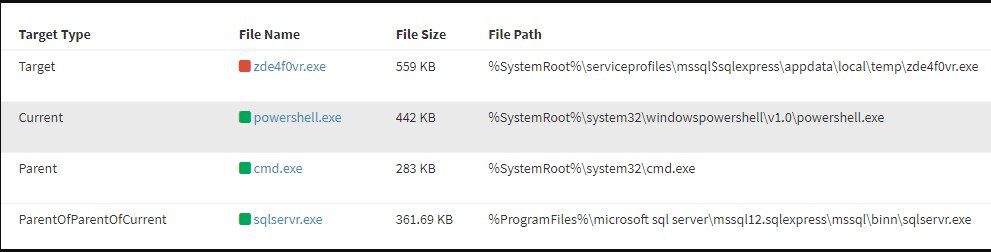
ASEC researchers observed that the attackers deploy cryptocurrency mining tools such as Lemon Duck, KingMiner, and Vollgar when attackers have access to the servers. Attackers achieve persistence by installing Cobalt Strike and using it for lateral movement.

“Cobalt Strike that is executed in MSBuild.exe has an additional settings option to bypass detection of security products, where it loads the normal dll wwanmm.dll, then writes and executes a beacon in the memory area of the dll. As the beacon that receives the attacker’s command and performs the malicious behavior does not exist in a suspicious memory area and instead operates in the normal module wwanmm.dll, it can bypass memory-based detection,” explains the report by Ahn Lab’s ASEC group.
It’s unclear how the attackers took control of the MS-SQL server and installed the malware, but experts believe that the targeted system had inappropriately managed the account credentials. In addition, Ahn Lab’s ASEC group also released compromise indicators for these attacks, including download URLs, MD5 hashes of beacons, and C2 server URLs.