VulnWhisperer 1.8 releases: Create actionable data from your Vulnerability Scans
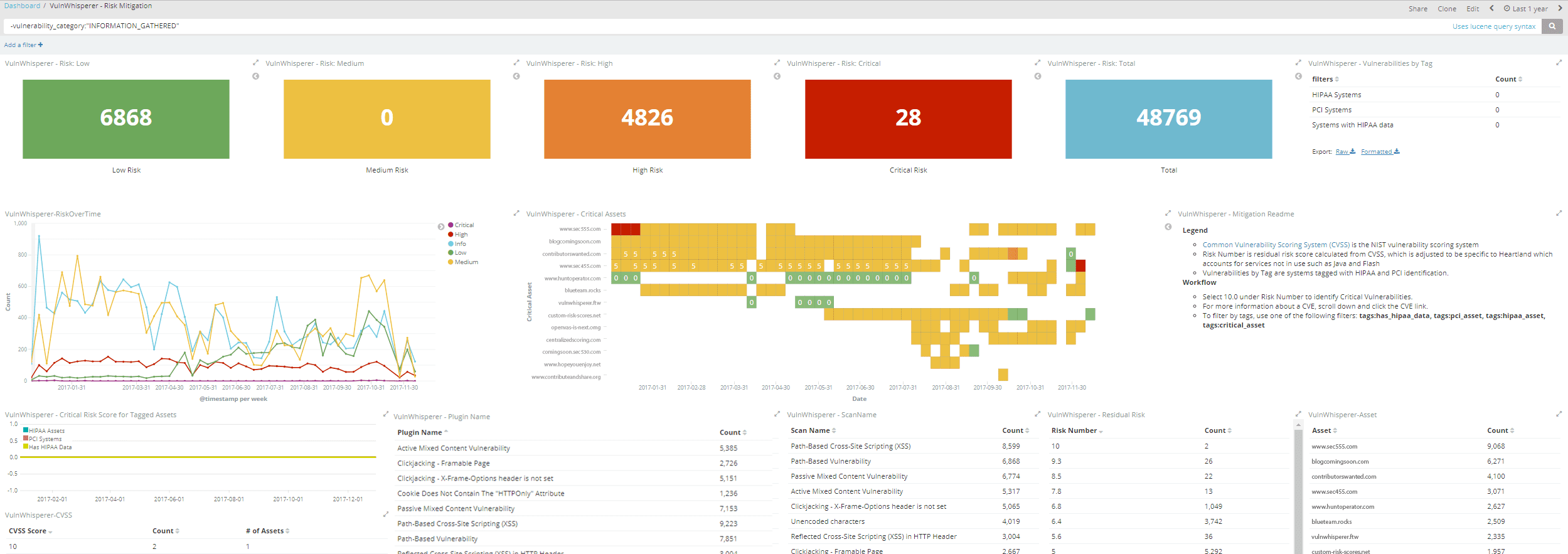
VulnWhisperer is a vulnerability data and reports aggregator. It will pull all the reports and create a file with a unique filename which is then fed into logstash. Logstash extracts data from the filename and tags all of the information inside the report (see logstash_vulnwhisp.conf file). Data is then shipped to elasticsearch to be indexed.

Currently Supports
Vulnerability Frameworks
Changelog
v1.8
This release has been focused on stabilizing the project, fixing bugs and improving existing processes and offering a more consistent and easy to deploy product to the end-user.
Changes:
- Completion of Jira Closed Cycle Sync Use Cases and general improvements.
- Fix of all reported VulnWhisperer bugs.
- Deleted VulnWhisperer’s qualysapi fork dependency and merged code with the original library
- Implementation of project testing and coverage, including mocking API calls from the modules.
- Implemented docker-compose testing.
- Updated Travis to check on each commit against all implemented tests.
- Moved completely to ELK6 and fixed Issues with ElasticSearch and Kibana (ELK5 now deprecated).
- Fix of Qualys WAS module
- Improvement of Nessus download handling
- Unused code cleanup
- Added file logging and improved logging format
- Reorg of the project resources structure
- Updated documentation both in Readme and Wiki page.
Installation
Requirement
- ElasticStack 5.x
- Python 2.7
- Vulnerability Scanner
- Optional: Message broker such as Kafka or RabbitMQ
Install
git clone https://github.com/austin-taylor/VulnWhisperer.git
cd VulnWhisperer
pip install -r requirements.txt
python setup.py install
Configuration
There are a few configuration steps to setting up VulnWhisperer:
- Configure Ini file
- Setup Logstash File
- Import ElasticSearch Templates
- Import Kibana Dashboards
Run
To run, fill out the configuration file with your vulnerability scanner settings. Then you can execute from the command line.
vuln_whisperer -c configs/example.ini -s nessus
or
vuln_whisperer -c configs/example.ini -s qualys
Next, you’ll need to import the visualizations into Kibana and setup your logstash config. A more thorough README is underway with setup instructions.
For windows, you may need to type the full path of the binary in vulnWhisperer located in the bin directory.
Demo
Copyright (c) 2017 Austin Taylor







