WackoPicko: vulnerable web application used to test web application vulnerability scanners
WackoPicko is a website that contains known vulnerabilities.
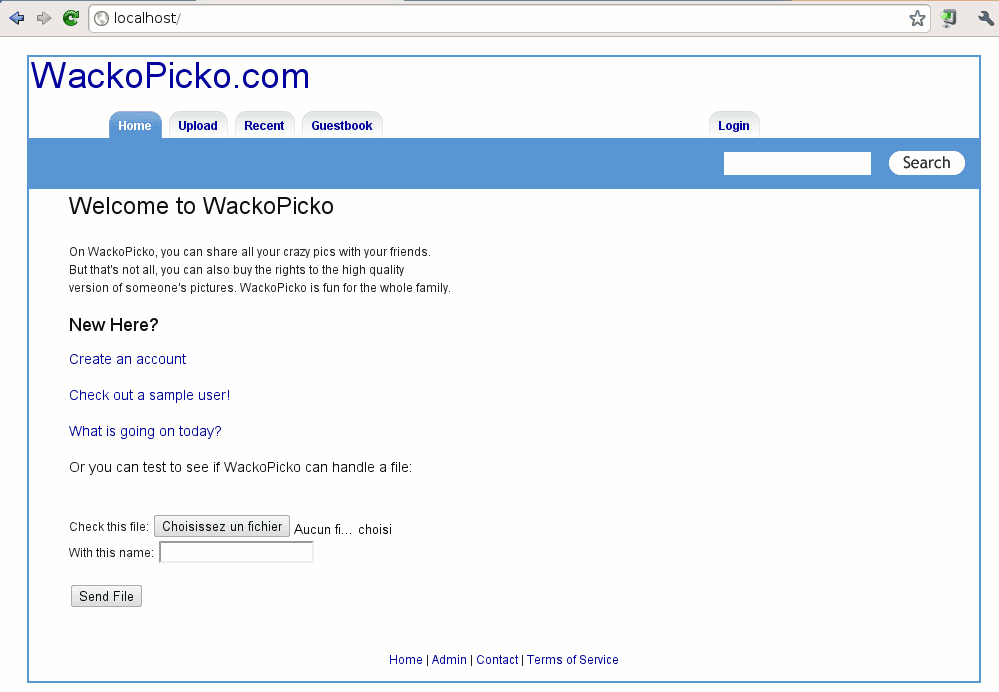
WackoPicko is a photo sharing and photo-purchasing site. A typical user of WackoPicko is able to upload photos, browse other user’s photos, comment on photos, and purchase the rights to a high-quality version of a photo.
- Authentication. WackoPicko provides personalized content to registered users. Despite recent efforts for a unified login across websites, most web applications require a user to create an account in order to utilize the services offered. Thus, WackoPicko has a user registration system. Once a user has created an account, he/she can log in to access WackoPicko’s restricted features.
- Upload Pictures. When a photo is uploaded to WackoPicko by a registered user, other
users can comment on it, as well as purchase the right to a high-quality version. Comment On Pictures. Once a picture is uploaded into WackoPicko, all registered users can comment on the photo by filling out a form. Once created, the comment is displayed, along with the picture, with all the other comments associated with the picture. - Purchase Pictures. A registered user on WackoPicko can purchase the high-quality the version of a picture. The purchase follows a multi-step process in which a shopping cart is filled with the items to be purchased, similar to the process used in e-commerce sites. After pictures are added to the cart, the total price of the cart is reviewed, discount coupons may be applied, and the order is placed. Once the pictures are purchased, the user is provided with links to the high-quality version of the pictures.
- Search. To enable users to easily search for various pictures, WackoPicko provides a search toolbar at the top of every page. The search functionality utilizes the tag field that was filled out when the picture was uploaded. After a query is issued, the user is presented with a list of all the pictures that have tags that match the query. Guestbook. A guestbook page provides a way to receive feedback from all visitors to the WackoPicko web site. The form used to submit feedback contains a “name” field and a “comment” field.
- Admin Area. WackoPicko has a special area for administrators only, which has a different login mechanism than regular users. Administrators can perform special actions, such as deleting user accounts or changing the tags of a picture.
Vulnerabilities
- Reflected XSS: In the search form, the query parameter is vulnerable.
- Stored XSS: The comment field is vulnerable to a persistent XSS attack.
- SessionID vulnerability: The session cookie value used for the administration authentication is based on a weak and guessable implementation (auto-incremental value).
- Stored SQL Injection: The first name field of the register users form contains a stored SQL injection which is then used unsanitized on the similar user’s page.
- Reflected SQL Injection: The username field is vulnerable.
- Directory Traversal: The tag field has a directory traversal vulnerability enabling a malicious user to overwrite any file the web server user has access to.
- Multi-Step Stored XSS: The comment field is vulnerable to XSS, however, must go through a preview form.
- Forceful Browsing: The user doesn’t have to purchase the picture to see the high-quality version.
- Command-line Injection: The password field is vulnerable to command line injections.
- File Inclusion: The /admin/index.php page is vulnerable to a file inclusion vulnerability, however, you have to include %00 at the end.
- Parameter Manipulation: The userid parameter can be manipulated to see any user’s page when you need to be logged in otherwise.
- Reflected XSS Behind JavaScript: The name parameter is vulnerable.
- Logic Flaw: A coupon can be applied multiple times reducing the price of an order to zero. The coupon in the initial data is SUPERYOU21.
- Reflected XSS Behind a Flash Form: The value parameter is vulnerable.
- Weak username/password: There is a default username/password combination of admin/admin.
Install
Docker Image
Simply run the following, which will map your local port 8080 to the port 80 in the container. Change the 8080 to another port if you like:
docker run -p 127.0.0.1:8080:80 -it adamdoupe/wackopicko
Once the docker image is downloaded and running, you should be able to access wackopicko on your browser: http://localhost:8080.
Note that Windows users might need some additional steps to do the port forwarding correctly. Google is your friend, use it well.
Install From Source
First, ensure that short_open_tag PHP ini option is enabled:
http://www.php.net/manual/en/ini.core.php#ini.short-open-tag
Import the WackoPicko database into MySQL using a command like the following:
mysql -u -p < current.sql
This will create the MySQL user wackopicko with the password webvuln!@# as well as create the wackopicko table.
The wackopicko table contains all of the data that was present while testing the scanners in Why Johnny Can’t Pentest.
The final step is to enable read/write access to the upload directory of WackoPicko for the web server user. An easy way to do this is:
chmod 777 -R upload

Image: aldeid
Valid Logins
Regular users
- scanner1/scanner1
- scanner2/scanner2
- bryce/bryce
Administrator users
- admin/admin
- adamd/adamd
Copyright (c) 2010 Adam Doupe
Source: https://github.com/adamdoupe/