FortiGuard Labs uncovered a threat actor leveraging a sophisticated attack to distribute the CHAVECLOAK banking Trojan. The attack begins with a malicious PDF, downloads a ZIP file, and employs DLL side-loading for malware execution. The CHAVECLOAK campaign specifically targets Brazil to exfiltrate financial data.

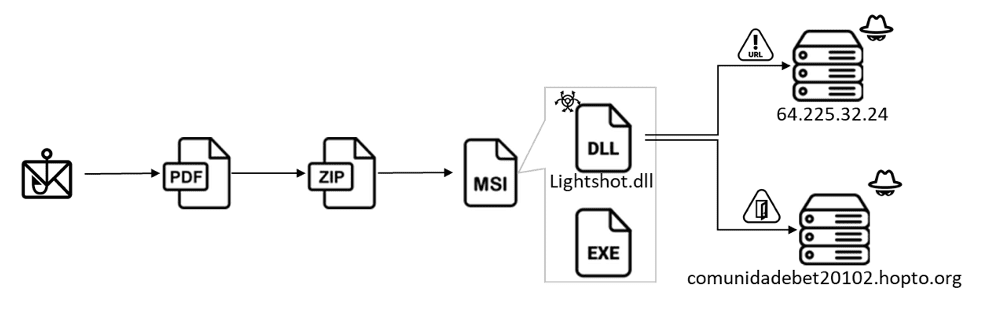
The inception of this assault lies within an innocuous-seeming PDF document. Masquerading as a contract requiring the recipient’s attention, it beckons the user to click a button to proceed with reading and signing the alleged documents. This act of apparent benignity is a facade; a malicious downloader link is ingeniously embedded within the document. Through a series of redirects involving the use of a free link-shortening service, victims find themselves downloading a ZIP file that serves as the Trojan’s horse, smuggling CHAVECLOAK into the system of its prey.
Upon the unsuspecting user’s engagement with the ZIP file, an MSI installer is unleashed. Within this installer lies a cacophony of benign files alongside the malignant “Lightshot.dll,” a file whose recent modification date belies its malicious intent. The installer, through a guise of legitimacy, executes “Lightshot.exe,” setting the stage for the sinister act of DLL sideloading. This technique enables the execution of malicious code under the cover of a legitimate application, thereby facilitating the covert theft of sensitive information without alarming the user or traditional security measures.
Once activated, CHAVECLOAK begins by gathering system information to establish a foothold on the victim’s device, ensuring its persistence through registry modifications. What follows is a methodical surveillance of the user’s interactions with financial platforms, including banks and cryptocurrency services. Through a combination of keylogging, screen blocking, and deceptive pop-ups, CHAVECLOAK captures the login credentials of its victims, transmitting this pilfered data back to its Command and Control (C2) server.
Interestingly, an older variant of this Trojan was discovered, revealing a progression in the sophistication of its deployment mechanisms. This variant utilizes a Delphi executable to embed its payload more discreetly, further refining its methods to evade detection and enhance its data harvesting capabilities.
“CHAVECLOAK exemplifies the sophistication of contemporary banking trojans, necessitating continual vigilance and proactive cybersecurity measures to safeguard against evolving threats within the financial landscape of South America,” the researcher concludes.