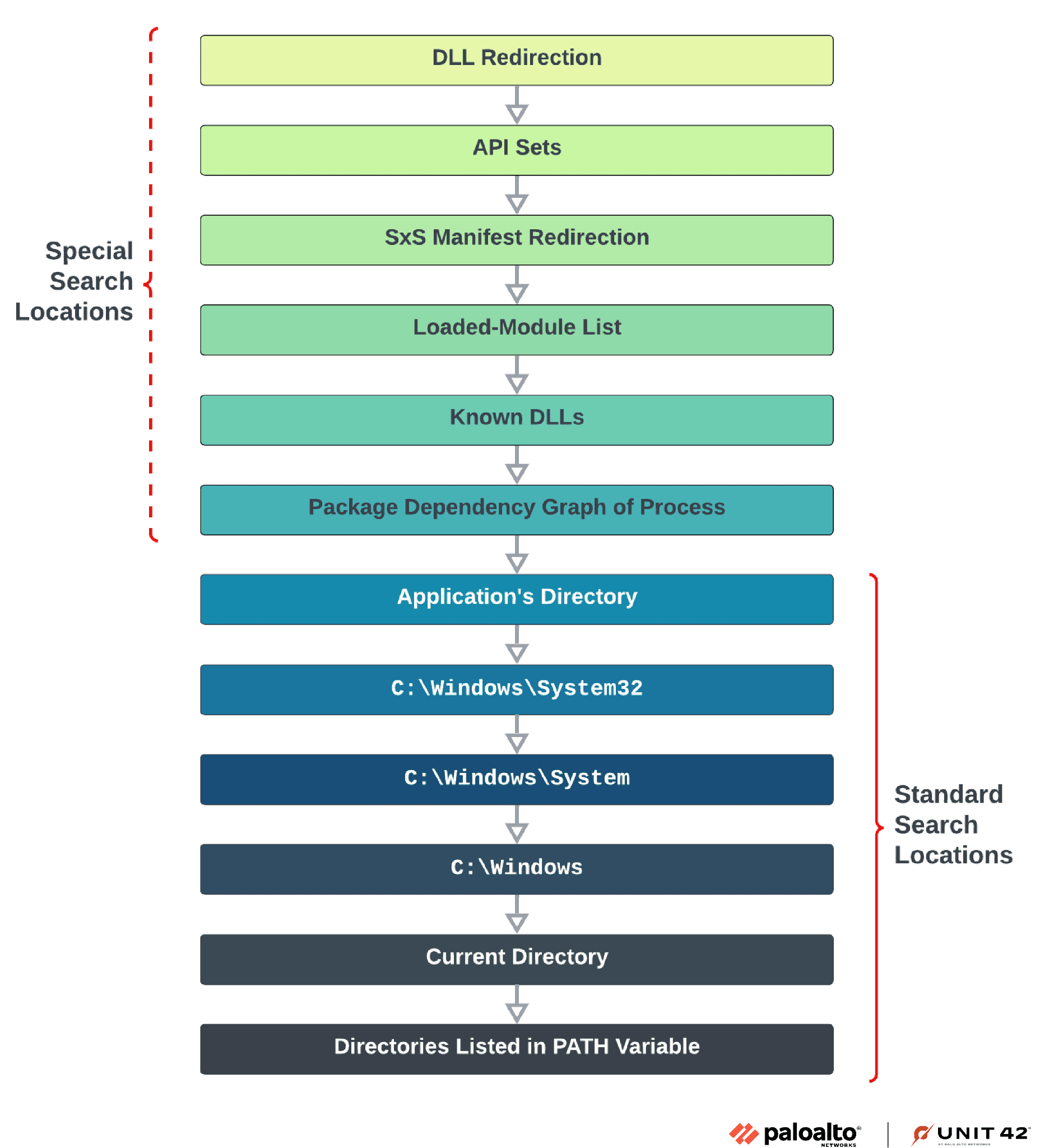
Flow chart of the Windows DLL search order
In the cybersecurity threats, DLL hijacking remains a classic maneuver in the arsenal of cyber adversaries. This technique, despite its age, continues to offer a stealthy passage for threat actors to deploy malware, underscoring the arms race between cyber defenders and attackers. A recent report from Unit 42 sheds light on the evolving landscape of DLL hijacking, revealing the intricacies of this enduring threat and offering a beacon of guidance for mitigating this attack surface.
Understanding the Stealth Mechanism

Dynamic-link library (DLL) hijacking is a technique as old as it is effective, allowing attackers to mislead an operating system into executing a malicious binary in place of a legitimate DLL. This subterfuge not only grants access to the attackers but also camouflages their presence, making detection a formidable challenge. The essence of DLL hijacking lies in its exploitation of the DLL search order mechanism of Microsoft Windows, a sequence of locations a program checks when loading a DLL.
The DLL Search Order: A Double-Edged Sword
At the heart of DLL hijacking is the Windows DLL search order, a well-intentioned mechanism turned vulnerability. This order includes special search locations prioritized over standard ones, ranging from DLL redirection to known DLLs and package dependency graphs. However, it is the standard search locations—especially the application’s directory and the directories listed in the PATH environment variable—that adversaries most commonly exploit for their clandestine operations.
The Evolution of DLL Hijacking
Over the years, DLL hijacking has morphed, adopting new forms to stay one step ahead of defense mechanisms. Among the most prevalent techniques are DLL side-loading, DLL search order hijacking, and phantom DLL loading. Each method has its nuances but shares the common goal of leveraging the DLL loading process for malicious purposes, from gaining persistence to executing command and control communications.
DLL hijacking is flexible, offering attackers a range of tactics:
- DLL Side-Loading: The most common method involves dropping a malicious DLL into the same folder as a rarely used but legitimate program. The lack of attention makes this ideal for hiding malicious activity.
- Manipulating the Search Path: Attackers can modify the PATH environment variable to include a folder under their control. This ensures their fake DLL gets priority.
- Exploiting Missing DLLs: Some programs mistakenly try to load DLLs that don’t even exist. Attackers can plant their malicious DLL with the missing file’s name in the right place to exploit this flaw.
- The Persistence Angle: Beyond initial code execution, DLL hijacking can be used to make malware load every time you start a seemingly legitimate program, ensuring a long-term foothold within your system.
Real-World Intrusions: A Glimpse into the Dark
Unit 42’s report illuminates the tactics of both cybercrime and nation-state APT groups through real-world examples. From the sophisticated operations of Stately Taurus employing triple DLL side-loading for the ToneShell backdoor to the cunning use of phantom DLL loading by cybercriminals deploying CatB ransomware, these instances underscore the adaptability and persistence of threat actors.
DLL hijacking’s stealth and relative ease of execution make it a favorite across the threat landscape:
- State-Sponsored Espionage: Government-backed groups like those linked to China have used DLL hijacking to install backdoors like ToneShell for long-term surveillance and data theft.
- Multipurpose Malware: The infamous PlugX RAT, used by various threat actors, frequently leverages DLL side-loading to evade detection. This shows how adaptable the technique is for different criminal goals.
- Ransomware Payloads: Attackers have abused vulnerabilities in the Windows MSDTC service to deliver ransomware like CatB in the form of a fake DLL. This highlights its use in destructive attacks.
Mitigating the Threat: Strategies and Best Practices
Detecting and mitigating DLL hijacking attacks is an intricate affair, given the stealthy nature of this technique. Unit 42 emphasizes several principles for effective detection, focusing on abnormalities in the malicious DLL, the vulnerable application, and the loading event. Moreover, the report champions proactive measures to shrink the attack surface, urging developers to adopt best practices such as specifying fully qualified paths for DLL loading and leveraging DLL redirection and manifests.