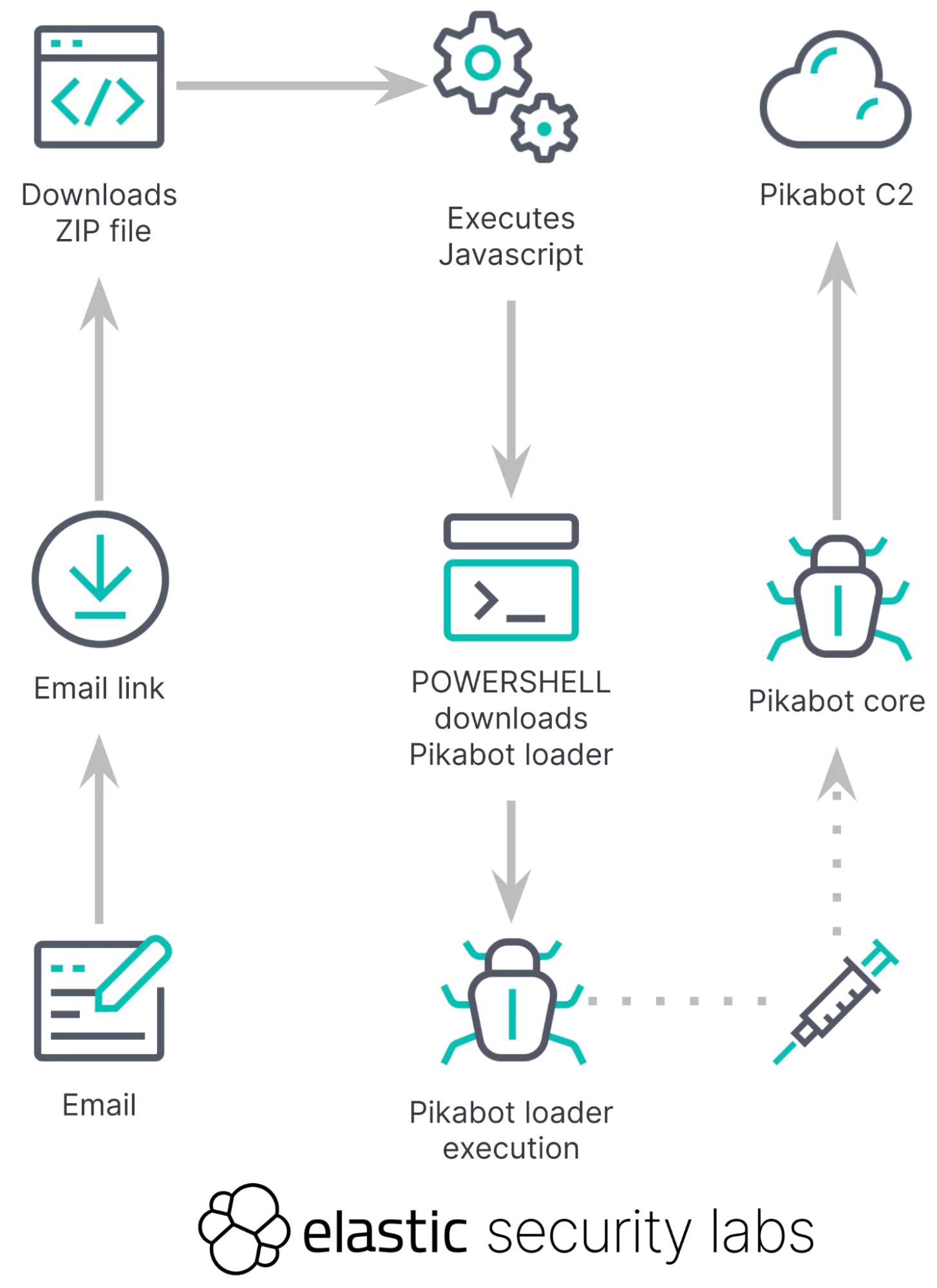
PIKABOT execution flow
Elastic Security Labs observes a significant overhaul of the PIKABOT loader and core modules, marking a resurgence of this persistent malware family. This deep-dive analysis unveils the revamped techniques PIKABOT uses for unpacking, obfuscation, core functionality, and network communication. Understanding its new tactics is essential for defenders to counter this evolving threat.

PIKABOT: A Brief Overview
PIKABOT has long been a tool of choice for malicious actors, facilitating the distribution of payloads like Cobalt Strike or even launching ransomware attacks. On February 8th, Elastic Security Labs stumbled upon a fresh campaign featuring an updated variant of this notorious loader. The new PIKABOT version introduces a novel unpacking method alongside heavy obfuscation, marking a significant evolution in its design. The core module includes a new string decryption implementation and a series of modifications aimed at dodging detection with even greater efficiency.
The updated PIKABOT distinguishes itself through a unique combination of technical sophistication:
- Subtle Loader Delivery: PIKABOT now hides its payload within seemingly legitimate executables, scattering base64-encoded chunks throughout the .data section. This stealthy approach bypasses basic file scanning.
- Obfuscated, Yet Evolving: Code remains heavily obfuscated, now with fewer densely-packed inline functions. This change potentially simplifies the development process for the authors, enabling them to iterate more quickly.
- Plaintext Configuration (Temporarily?): Unexpectedly, configuration data is now held in plaintext during runtime. This could be a temporary measure during active development, but also carries risks for the malware operators if defenders find and exploit the configuration.
- Downgraded Encryption? Network communication shifts from AES to RC4 and byte-shifting, potentially reducing the strength of encryption for intercepted traffic. However, this might be a deliberate attempt to hinder traffic anomaly detection systems.
These updates are not merely technical tweaks but represent a strategic evolution of PIKABOT. The developers have invested in creating a more resilient and elusive threat, capable of bypassing conventional detection mechanisms.
Loader Evolution: Unpacking in Depth
- Hidden Payload: Upon execution, the tampered executable extracts chunks of base64 data from its .data section. These chunks represent pieces of the true PIKABOT payload.
- Custom Decryption: The loader employs a custom algorithm involving bitwise operations to decode individual chunks. This obfuscation layer adds complexity for analysis and potentially evades some detection tools.
- Reflective Loading: To minimize its footprint, the loader utilizes reflective PE loading. This technique allows the malware to directly load and execute the PIKABOT payload within its own memory space, without writing the payload to disk for execution.
Evolving Obfuscation Techniques
- Shifting Strategies: While obfuscation remains a staple of PIKABOT, the over-reliance on inline functions has lessened. This may streamline the workflow for the malware developers, allowing them to iterate code changes more rapidly.
- Multiple Decoding Methods: PIKABOT adopts a variety of string decoding techniques, including stack strings and arrays with characters arranged in randomized order. This diversification keeps analysts on their toes.
Anti-Analysis: Staying Under the Radar
PIKABOT’s strong anti-debugging and anti-analysis capabilities persist:
- Direct Syscalls: The malware leverages direct syscalls to Zw APIs, circumventing the hooks of many userland monitoring tools and debugger traps.
- Thorough Process Scanning: It enumerates running processes to detect analysis tools or sandbox environments.
Core Updates & Network Behavior
- Victim Profiling & Language Checks: To ensure suitable targets, the malware collects extensive system information (OS version, display, memory, domains, processes, etc.) before checking the victim’s language settings. Russian or Ukrainian targets result in immediate termination.
- Configuration Puzzle: The presence of plaintext configuration in memory is an unexpected change. This might be a side-effect of active development or a deliberate choice to hinder analysis efforts.
- Encryption Changes: The replacement of AES with RC4 and byte-shifting for C2 communication could be a downgrade in overall network security. However, it may also be intended to make the traffic blend in with less-sensitive network flows.
- Familiar Functionality: Bot commands retain core capabilities from previous PIKABOT versions, allowing for remote execution, discovery, and process injection for further compromise.
The Development Cycle Continues
Several indicators point to PIKABOT being under active development:
- Incomplete Features: Unused command IDs and other unimplemented functionalities suggest a work-in-progress.
- Potential Vulnerabilities: The temporary(?) use of plaintext configuration could be exploited by skilled defenders.
Conclusion
The emergence of the updated PIKABOT campaigns serves as a stark reminder of the persistent and evolving nature of cyber threats. Elastic Security Labs’ detailed analysis not only sheds light on this specific threat but also emphasizes the broader need for continual adaptation and collaboration within the cybersecurity community.