Watch Out for Latrodectus: New Malware from Suspected IcedID Developers Targeting Businesses
In a joint report by Proofpoint’s Threat Research team and Team Cymru, a potent new malware dubbed “Latrodectus” has been exposed. This downloader, likely the work of the same developers behind the infamous IcedID malware, is gaining traction among threat actors as a tool to gain initial access to target networks.
Latrodectus first made its appearance in email threat campaigns in late November 2023, marking a significant evolution in malware sophistication. Initially distributed by the threat actor known as TA577, a known proliferator of Qbot before it was disrupted in 2023, Latrodectus exhibited a sharp decline in activity from December 2023 through January 2024. However, its use surged in subsequent months, indicating a strategic recalibration by its operators.
Unlike its predecessors, Latrodectus is not merely a variant of existing malware but a brand new entity in the cyber threat landscape. Proofpoint researchers have pinpointed its unique characteristics, confirming its independence from the IcedID malware, albeit with a shared lineage likely due to common developers. Latrodectus distinguishes itself through various sandbox evasion functionalities, showcasing the malware authors’ increasing efforts to bypass cybersecurity defenses effectively.
Example TA577 campaign delivering Latrodectus | Image: Proofpoint
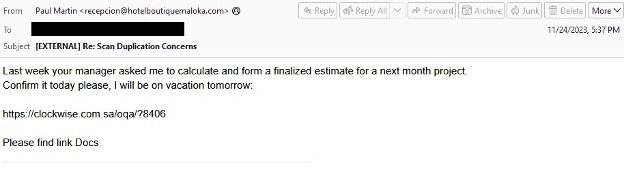
Latrodectus operates as a downloader with a clear objective: to download payloads and execute arbitrary commands. This operational capability was first harnessed by TA577 in a handful of campaigns before the baton was passed to TA578, another actor, which has since favored Latrodectus in its email threat campaigns. TA578’s modus operandi typically involves initiating contact through forms, a tactic that has proven effective in disseminating Latrodectus to unsuspecting victims.
In its initial deployment, TA577 did not rely on thread hijacking, a deviation from its usual tactics. Instead, it utilized a variety of email subjects and URLs to lure victims into downloading a JavaScript file responsible for executing the malicious Latrodectus DLL.

Example malicious contact form submission | Image: Proofpoint
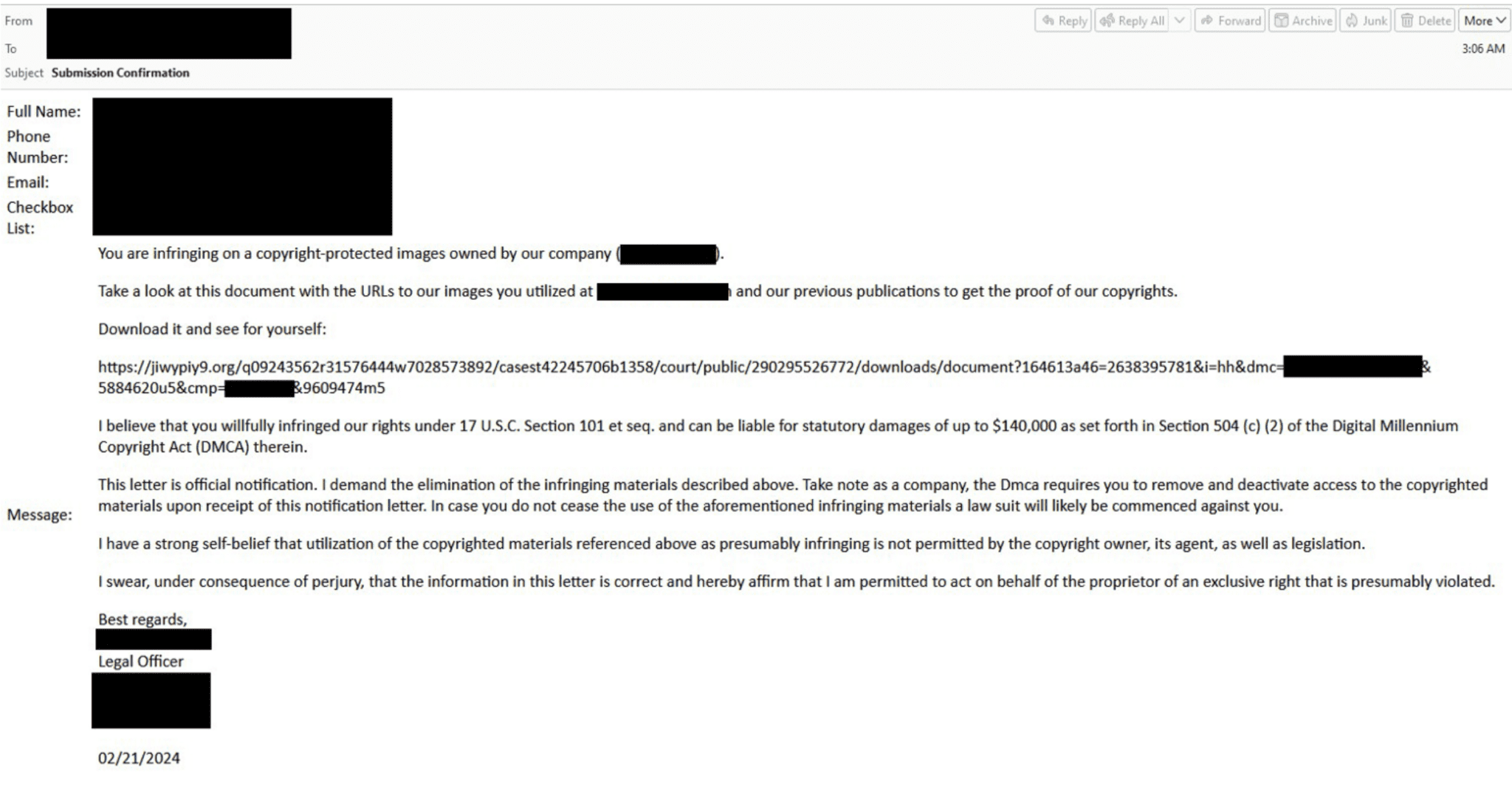
TA578, on the other hand, has adopted a more direct approach since mid-January 2024, almost exclusively distributing Latrodectus. This actor impersonates companies and sends legal threats about alleged copyright infringement, a tactic that not only heightens the credibility of the emails but also exploits the trust of recipients. The malware has been delivered through various ingenious methods, including DanaBot infections and impersonation scams, culminating in the execution of Latrodectus via an MSI from a WebDAV share.
Proofpoint anticipates that Latrodectus will become an increasingly preferred tool among threat actors, especially those previously aligned with IcedID. Its ability to evade sandbox detection underscores a broader trend in the cybercrime landscape, where malware authors are becoming more adept at circumventing defensive measures. This evolution demands a recalibration of cybersecurity strategies to better understand and mitigate the tactics, techniques, and procedures (TTPs) associated with this and similar malware.





